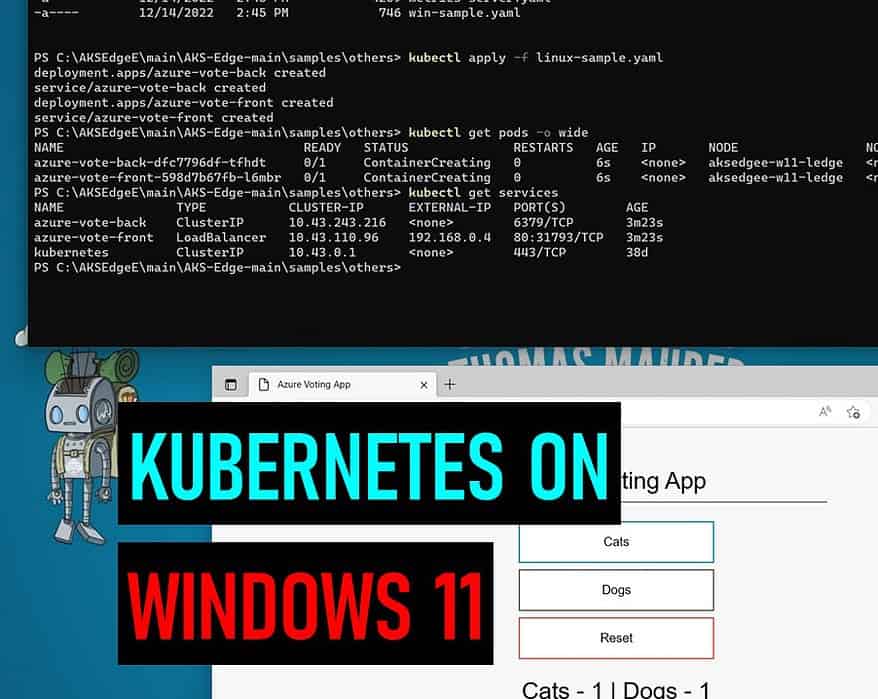
Install Kubernetes on Windows 10 and Windows 11 with AKS Edge Essentials
Awhile back I created a blog post on how you can install Kubernetes on Windows Server, and since...
Reset and Reinstall Windows 11 from the Cloud
In Windows 11 you have a new feature called Windows 11 Cloud Reset. This new feature helps you to reset and reinstall your Windows 11...
Install Sysinternals from the Microsoft Store
Yesterday at Sysinternals@25 special event for the birthday of the Sysinternals Suite, Mark Russinovich (Technical Fellow, CTO Microsoft...
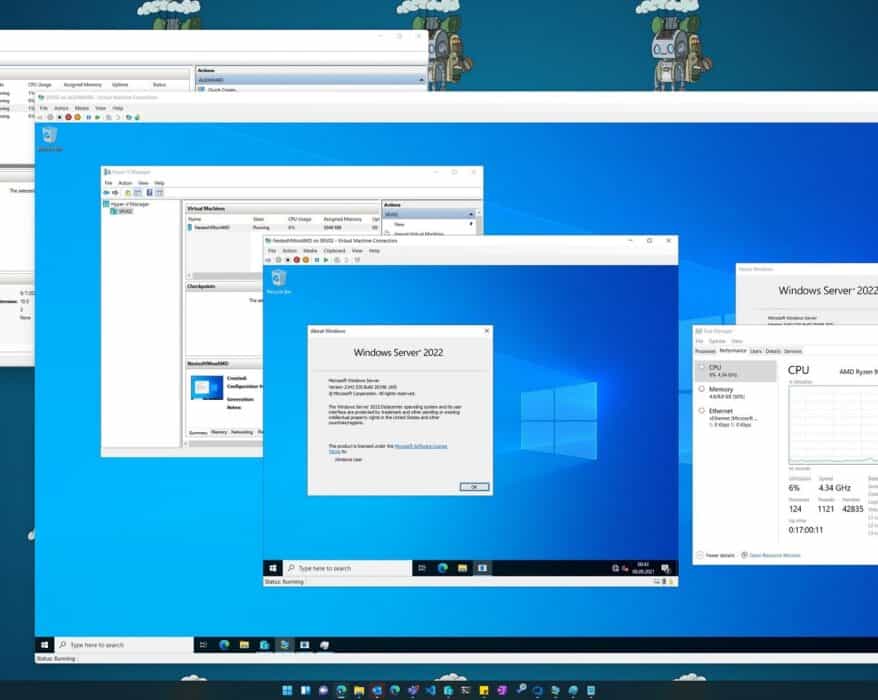
Hyper-V Nested virtualization for AMD processors
Windows Server 2022 just became generally available last week with a ton of great improvements in...
Install Azure Tools using WinGet
Sometimes you need to set up a fresh developer or admin workstation with all the latest Azure tools available. I created a quick list of...
Getting started with Windows Package Manager WinGet
In this blog post I want to quickly share how you can get started with the new Windows Package Manager and the WinGet CLI. At the Microsoft...
Create a Windows 10 development virtual machine
If you want to create a Windows 10 development virtual machine (VM) on your Windows 10 device,...
Install Apps from the Microsoft Store using WinGet
Back at Build 2020, Microsoft showed a new package manager for Windows called WinGet (Currently in Public Preview)....
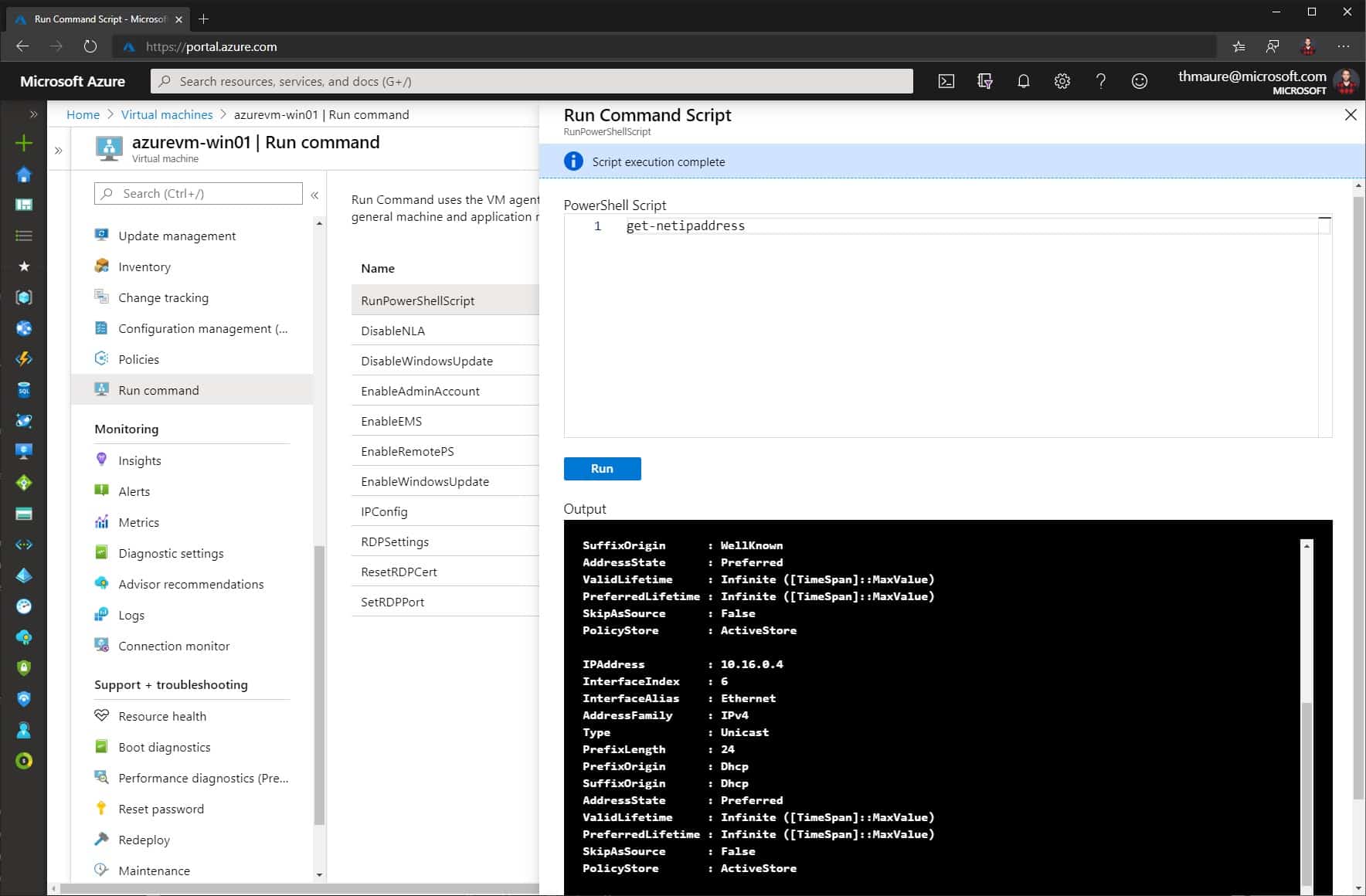
How to Run Scripts in your Azure VM using Run Command
You can access your Azure IaaS virtual machine (VM) in multiple ways like SSH or RDP, depending on your operating system and configuration....
Collect data from a Windows computer in a hybrid environment with Azure Monitor
I quickly want to share some of our new Azure tips videos. In this video, we are going to have a...