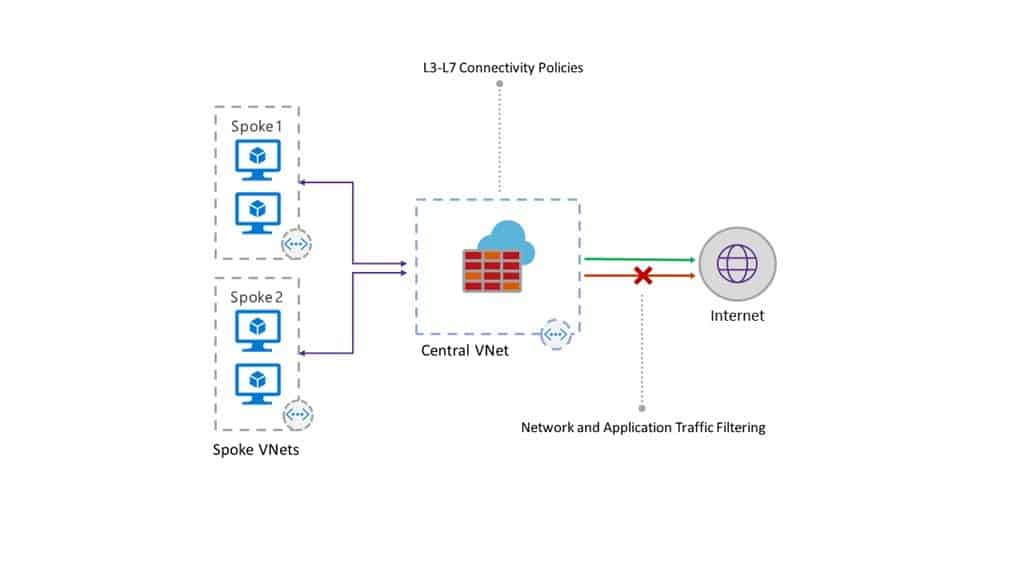
Last week Microsoft announced some cool new and long awaited Azure Network functionalities, which are now in public preview. One of them is the Azure Firewall, which is a fully stateful firewall as a service with built-in high availability and unrestricted cloud scalability. The Azure Firewall is centrally created, enforced, and allows you to log application and network connectivity policies across subscriptions and virtual networks.
This is especially helpful in scenarios where you simply want to block internet traffic or you need centralized management and logging. Obviously, there is still space for third-party firewall appliances with even more functionality, but if you need something easy to configure, without any additional licensing, which you can automatically configure using the existing tooling and has unrestricted scaling capabilities, the Azure Firewall is a great option.
It is also important to notice that the service is still in preview and additional functionality might be added as well as existing functionality might change.
(Image credit: Microsoft)
The Azure Firewall provides you with the following features:
- Stateful firewall as a service
- Built-in high availability with unrestricted cloud scalability
- Ability to centrally create, enforce, and log application and network connectivity policies
- Outbound source network address translation (SNAT) support
- Fully integrated with Azure Monitor for logging and analytics
Azure Outbound FQDN and network traffic filtering rules
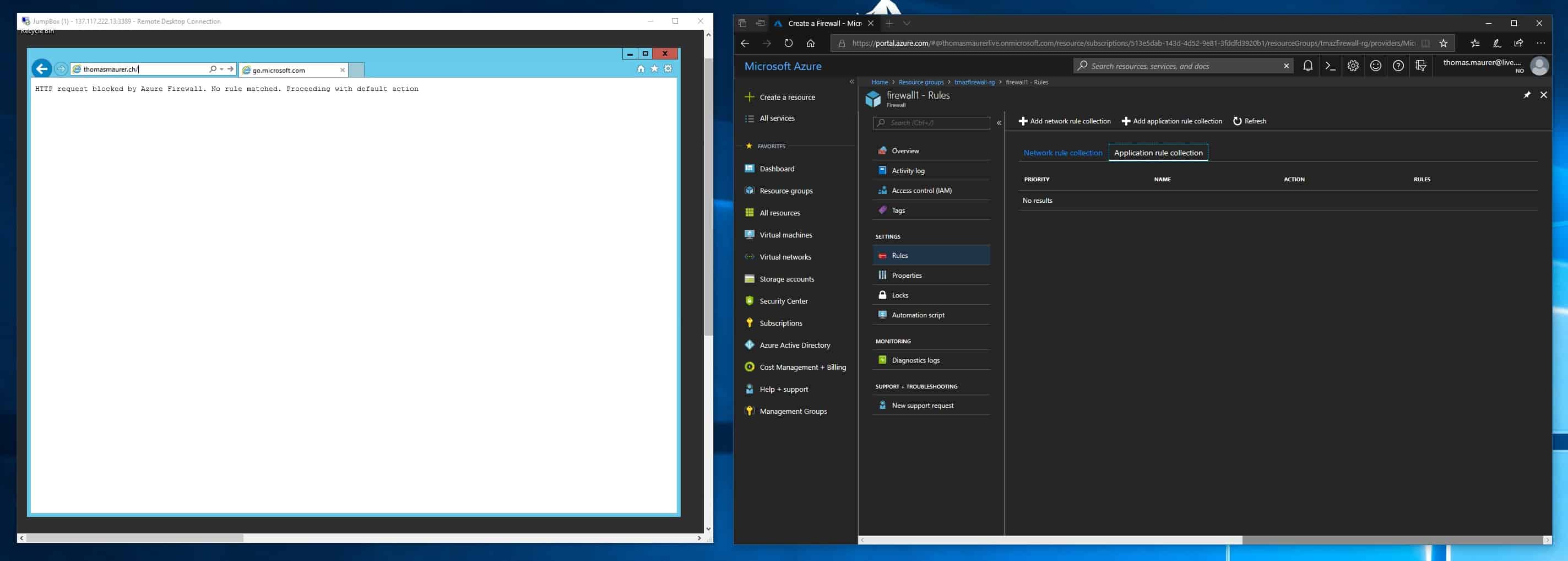
Azure Firewall is especially useful to manage outbound FQDN filtering, which helps you to protect data within your infrastructure by only allowing predefined FQDNs. It also allows you to centrally manage and enforce stateful filtering rules by source and destination address, port and protocol. This can be done by different networks across multiple subscriptions.
It also integrates in Azure Monitor for logging and lets you store log files on an Azure storage account which then can be used for example by Azure Log Analytics.
Integration into existing Azure network security
Azure Firewall is not just a new option, it also integrates in existing Azure network security features like Network Security Groups (NSG), Application Gateways, Services Endpoints and Azure DDoS Protection. Microsoft is also working with 3rd party vendors to help build scenarios where you can mix it with third party NVAs.
Setup Azure Firewall Public Preview
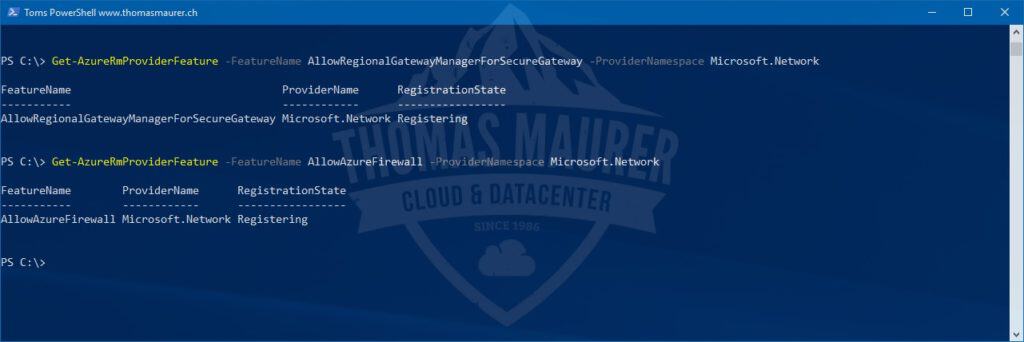
Today, Azure Firewall is in public preview, so you have to enable the service it in your subscription. To enable the Azure Firewall public preview, use the following Azure PowerShell commands:
Register-AzureRmProviderFeature -FeatureName AllowRegionalGatewayManagerForSecureGateway -ProviderNamespace Microsoft.Network Register-AzureRmProviderFeature -FeatureName AllowAzureFirewall -ProviderNamespace Microsoft.Network
This can take up to 30 minutes, you can check the registration status by using the following commands:
Get-AzureRmProviderFeature -FeatureName AllowRegionalGatewayManagerForSecureGateway -ProviderNamespace Microsoft.Network Get-AzureRmProviderFeature -FeatureName AllowAzureFirewall -ProviderNamespace Microsoft.Network
After the registration is complete, run the following command:
Register-AzureRmResourceProvider -ProviderNamespace Microsoft.Network
You can also find more about how to enable the Azure Firewall public preview on the Azure documentation page
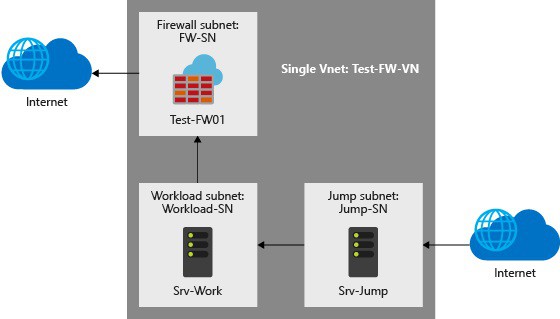
To build a sandbox environment to test this out you can use two deployment options:
(Image credit: Microsoft)
After that you can follow the simple tutorial to try it out: Tutorial: Deploy and configure Azure Firewall using the Azure portal or you just use the following Azure Resource Manager Template to build a quick Azure Firewall sandbox environment.
Pricing
The Azure Firewall right now is still in preview, but as it looks today, it will be metered per GB inbound and per GB outbound traffic which is going through the Azure Firewall.
If you have any questions feel free to comment in that post.
Tags: Azure, Azure Firewall, Azure FQDN filtering, Azure Monitor, Cloud FIrewall, Cloud Networking, Firewall, Firewall Logging, FQDN filtering, Logging, Microsoft, Netowrk Security, Network Security Group, Network Virtual Appliances, NSG, NVA, SNAT, Stateful Firewall, Virutal Network, WAF Last modified: March 13, 2019