Connect Ubiquiti UniFi Dream Machine to Azure VPN
A couple of days ago I got a Ubiquiti UniFi Dream Machine, which is an all-in-one device with an...
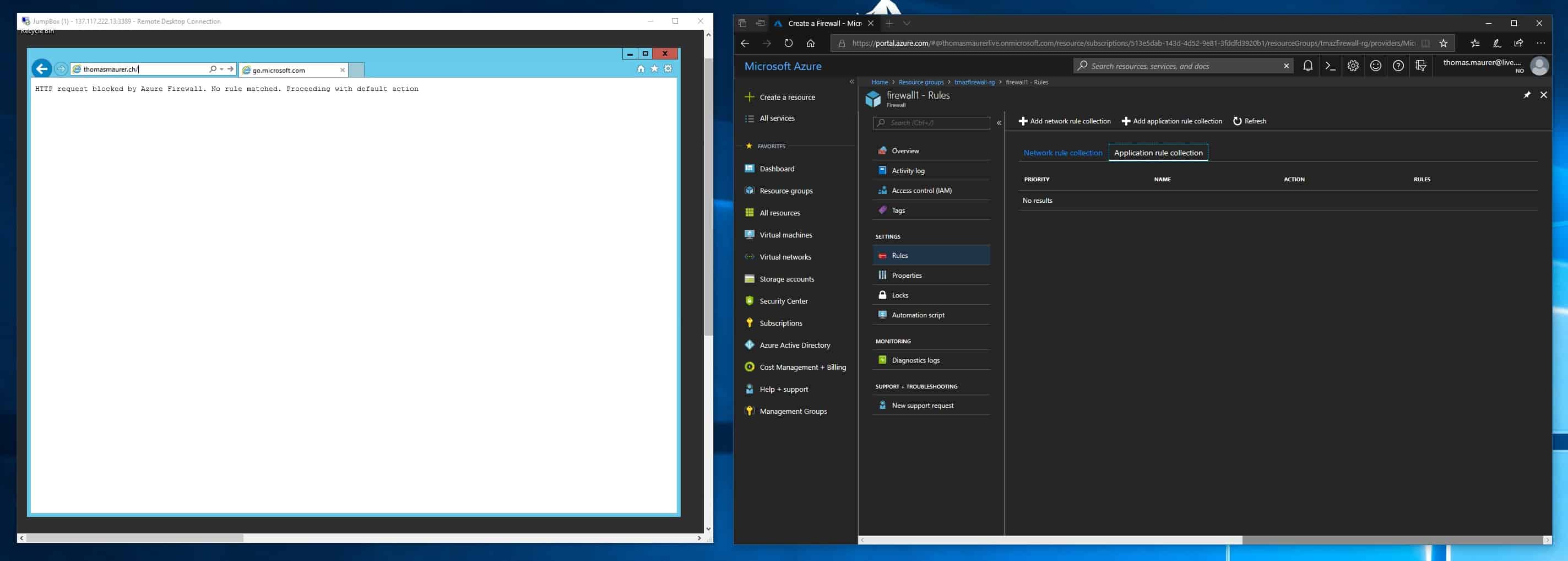
This is the Microsoft Azure Firewall
Last week Microsoft announced some cool new and long awaited Azure Network functionalities, which are now in public preview. One of them is...
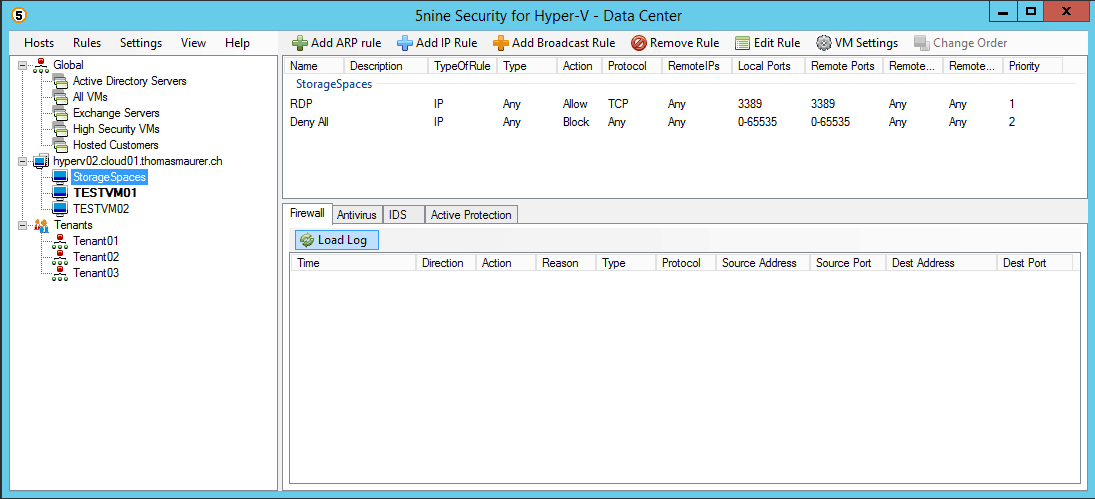
5nine Cloud Security for Hyper-V 4.0
Security is a critical part in your datacenter and with a high virtualization rate it gets even more critical and complex to manage....
Cisco UCS Hyper-V Cluster – Configure Blade Servers – Part 4
After we have installed the Cisco Blade Servers we now have to do some configuration on the Hosts....
Remote Disk Management with “RPC server is unavailable” Error
If you have a Windows Server 2008 R2 Core Server or a Hyper-V R2 Server, which is also managed like a Core Server, you are really happy if...
Windows PPTP VPN with Cisco Linksys RV042
Today I was setting up my little lab, I decided to create a Windows PPTP VPN for my lab network which should give me more comfort. First I...