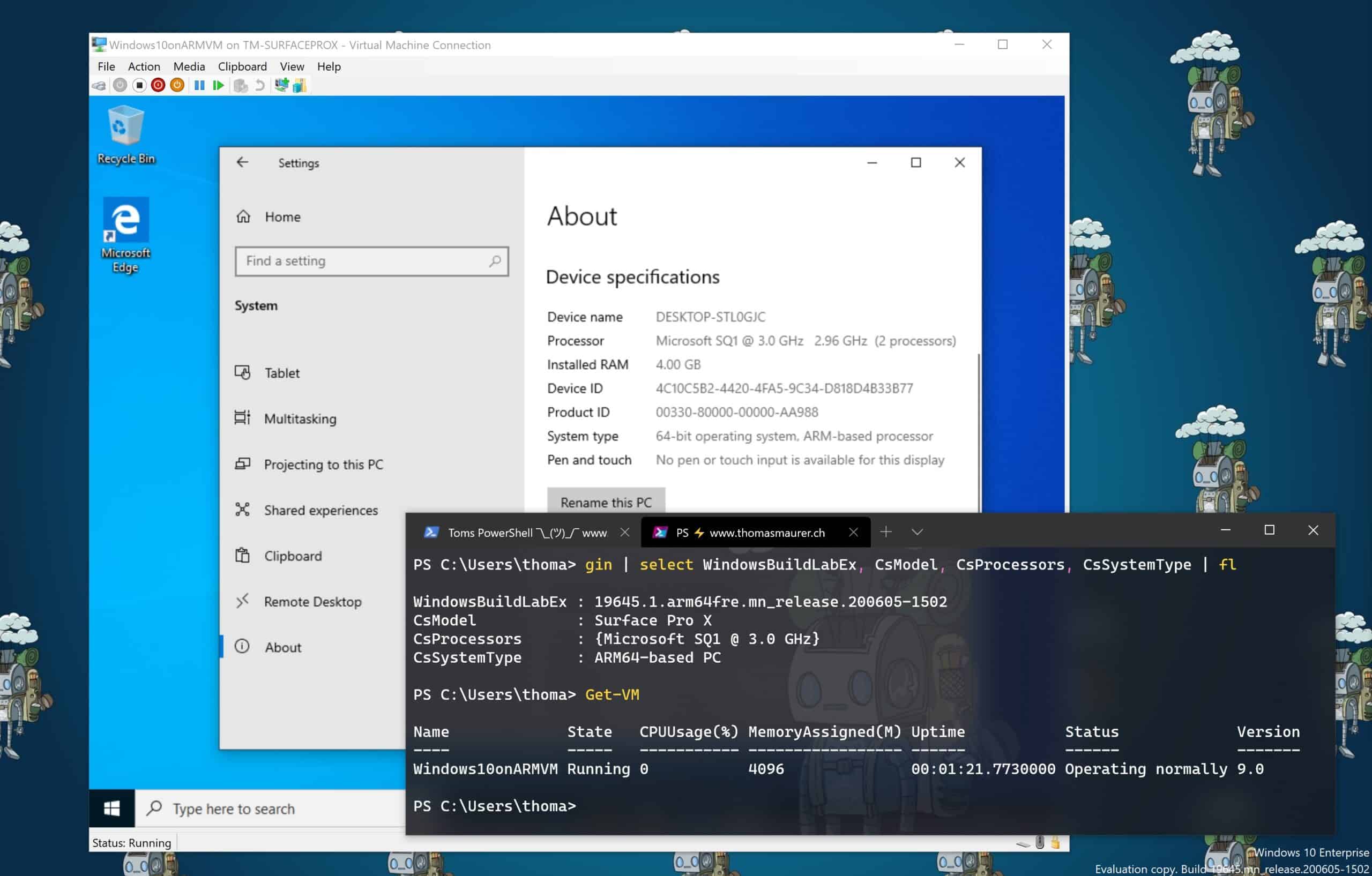
Run Hyper-V on Windows 10 on ARM and the Surface Pro X
Here is a quick blog post on how you can run Hyper-V virtual machines (VM) on Windows 10 on ARM and...
Surface Headphones 2 Mini Review
This week I just got my new Microsoft Surface Headphones 2, and since I got asked a lot about my first impressions, I want to share this...
Microsoft Surface USB-C Travel Hub Mini Review
Last week Microsoft started shipping the new Surface Dock 2 and the Microsoft Surface USB-C Travel Hub. Since I usually do a lot of...
My Surface Dock 2 Mini Review
Last week Microsoft started shipping the new Surface Dock 2 and the Microsoft USB-C Travel Hub. I...
How to Enable or Disable Hibernate on the Surface Pro X
I am sure you have seen that I am the proud owner of a Surface Pro X. The Surface Pro X is one of the latest Microsoft Surface devices, and...
How to host Tech Workshops and Trainings online
I just got asked by one of my blog readers, who is a consultant and trainer, about what tools I use to give online tech workshops and...
My Home Office Setup 2020 – How does yours look like?
A couple of days ago, Microsoft and other companies recommended that people work from home (if they...
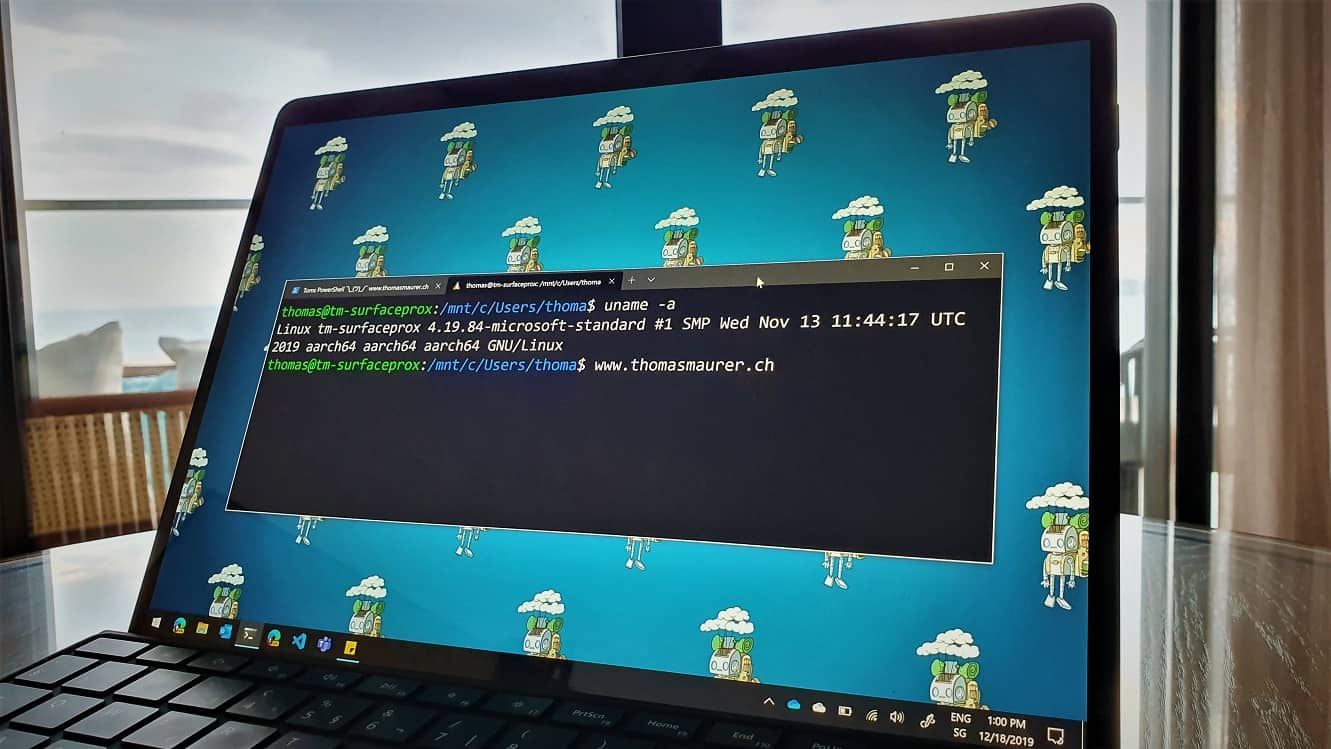
How to Install WSL 2 on Windows 10 on ARM
This is just a quick blog post about the experience on running the Windows Subsystem for Linux 2 (WSL 2) on Windows 10 on ARM, which comes...
Surface Pro X – First Impressions and Review
I just got my brand new Surface Pro X two weeks ago, and since then, I spent a couple of days with it and started to use it as my daily...
Microsoft House opened in Zürich
Microsoft Switzerland just announced the Microsoft “Pop-Up” House in Zürich. The...