Create a Windows 10 development virtual machine
If you want to create a Windows 10 development virtual machine (VM) on your Windows 10 device,...
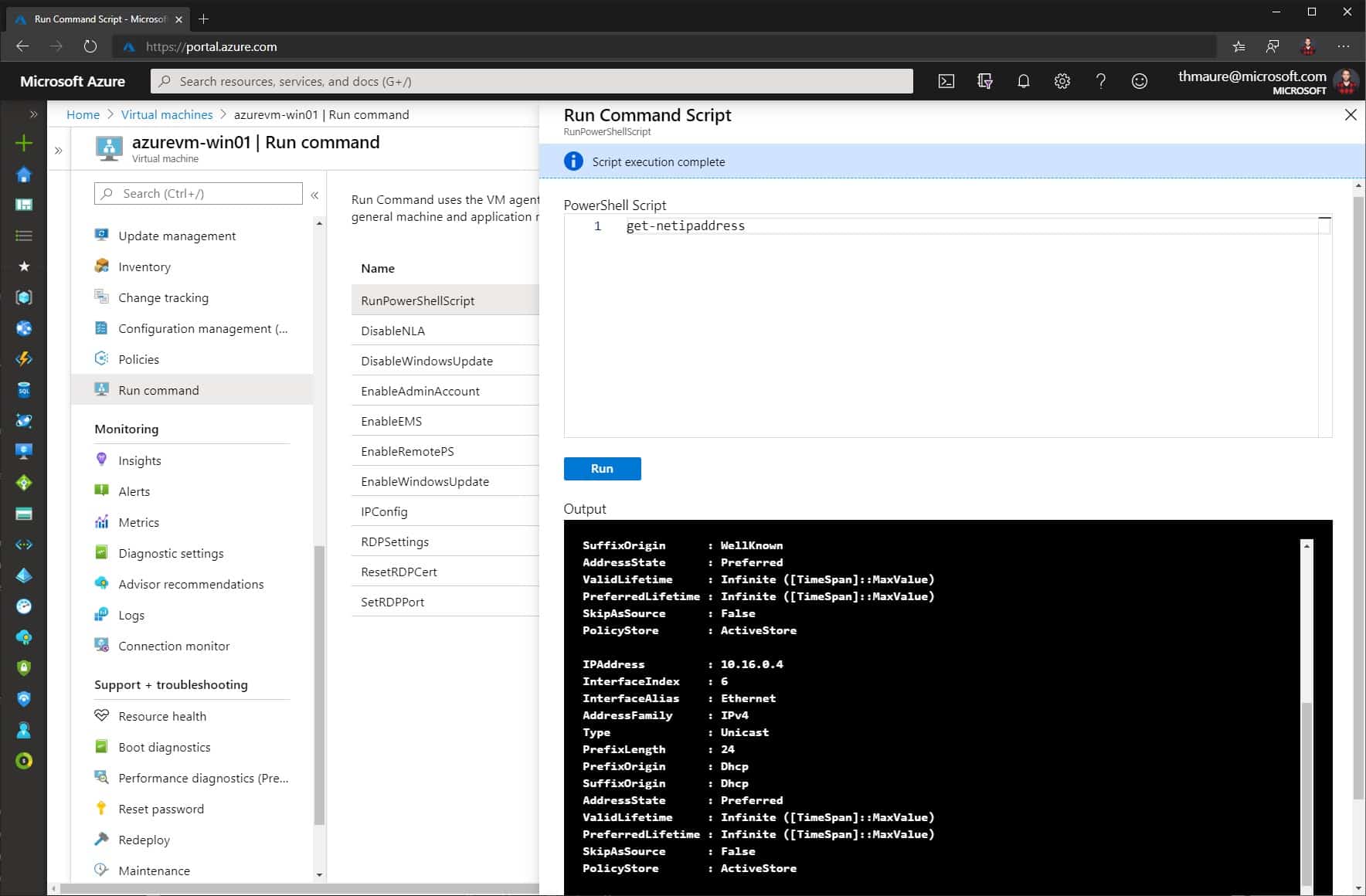
How to run scripts against multiple Azure VMs by using Run Command
I wrote a blog post on how to run scripts in your Azure VM by using Run Command, and explained how handy this feature is to manage Azure...
How to check the available VM Sizes (SKUs) by Azure Region
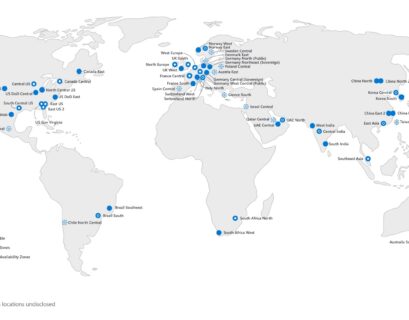
Do you want to know which Azure VM (virtual machine) sizes are available in an Azure region? Here are some simple ways like the Azure...
Learn about Windows Server Hyper-V and Virtualization
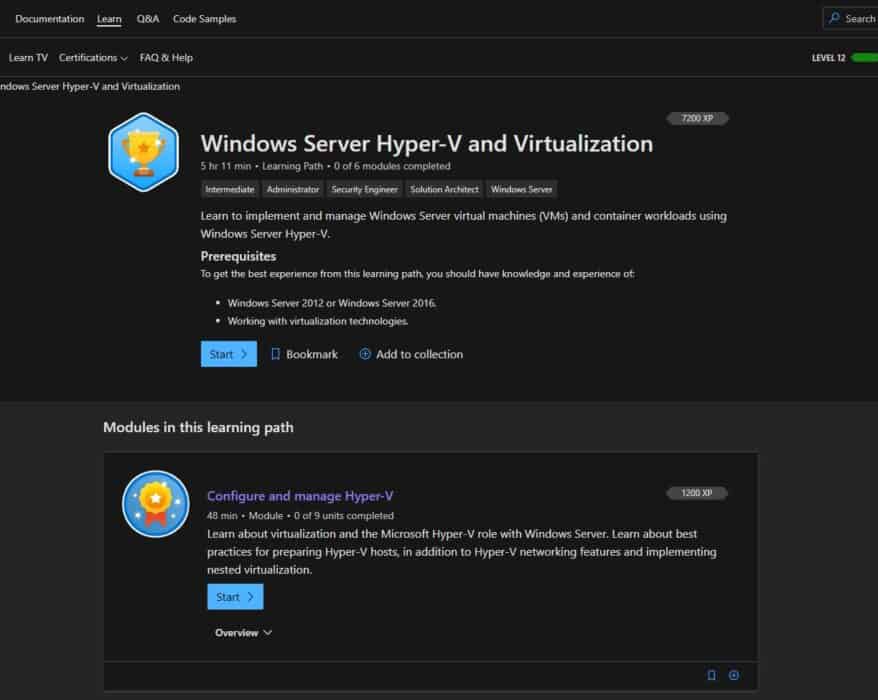
As you know, my background is doing a lot of datacenter and virtualization projects using Hyper-V...
How to Monitor an Azure virtual machine with Azure Monitor
This week in the Azure tip video, we are going to have a look at how to monitor an Azure virtual machine (VM) with Azure Monitor. You can...
Manage updates and patches for your Azure VMs
In this week’s Azure tip video we are going to have a look at how to manage updates and patches for your Azure virtual machines...
How to Run Scripts in your Azure VM using Run Command
You can access your Azure IaaS virtual machine (VM) in multiple ways like SSH or RDP, depending on...
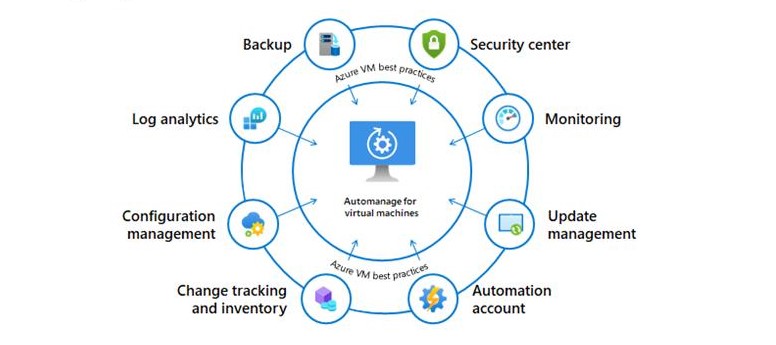
Automanage for Azure virtual machines
For me, one of the most impressive announcements at Microsoft Ignite, next to many of the Azure Arc and Azure Stack announcements, was the...
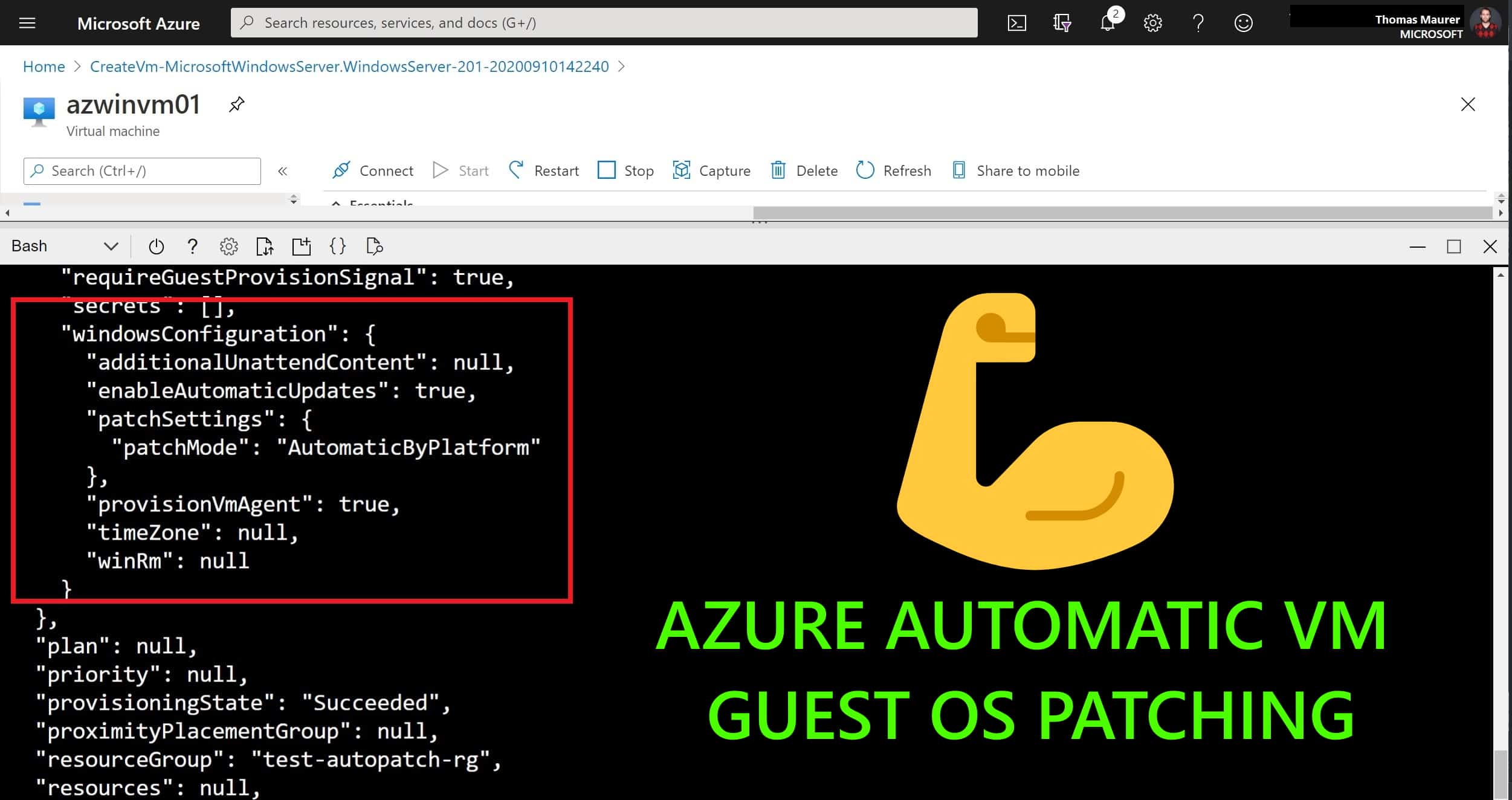
How to configure Azure Automatic VM guest OS patching
If you want to keep your Azure virtual machines (VMs) up-to-date, then there is a service called Azure Update Management, which helps you...
Learn Windows Server Hybrid and Azure IaaS VMs
A couple of weeks back I promoted a post about how you can learn about Windows Server on Azure and...