PowerShell Unplugged 2022 Edition
April Edwards and I had the chance to host the PowerShell Unplugged 2022 Edition and the video is...
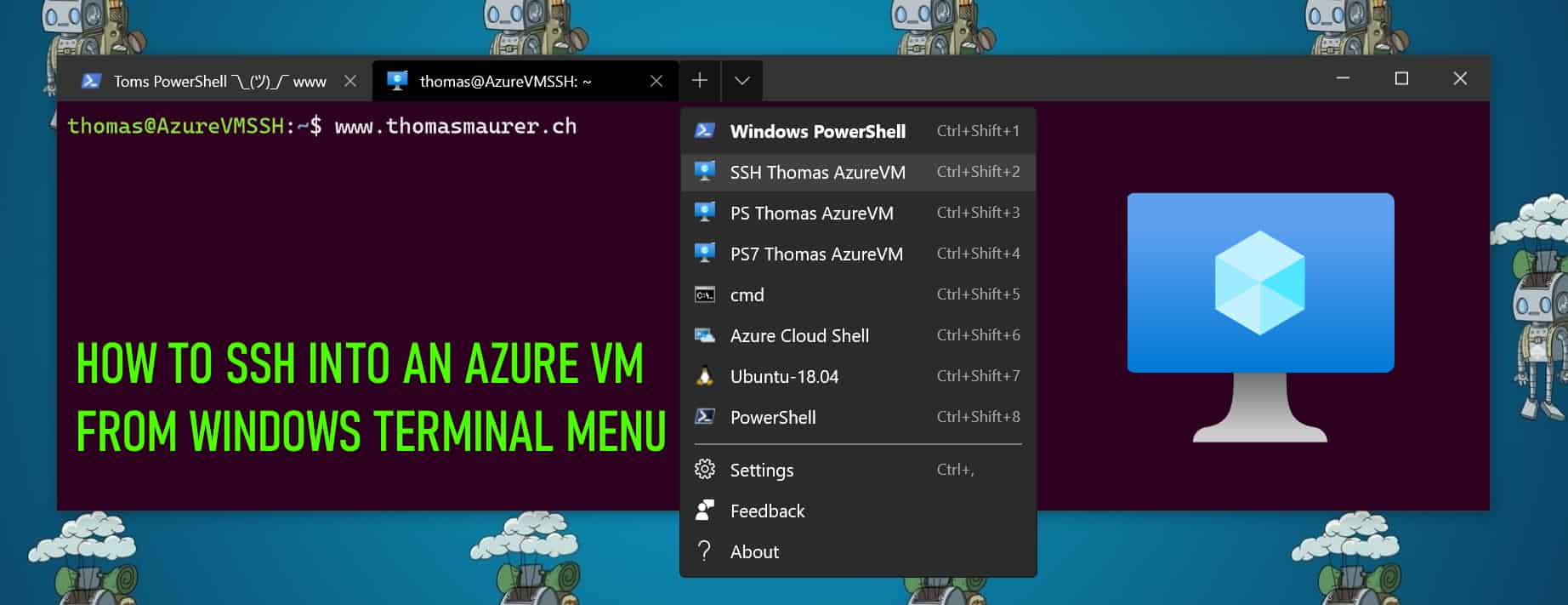
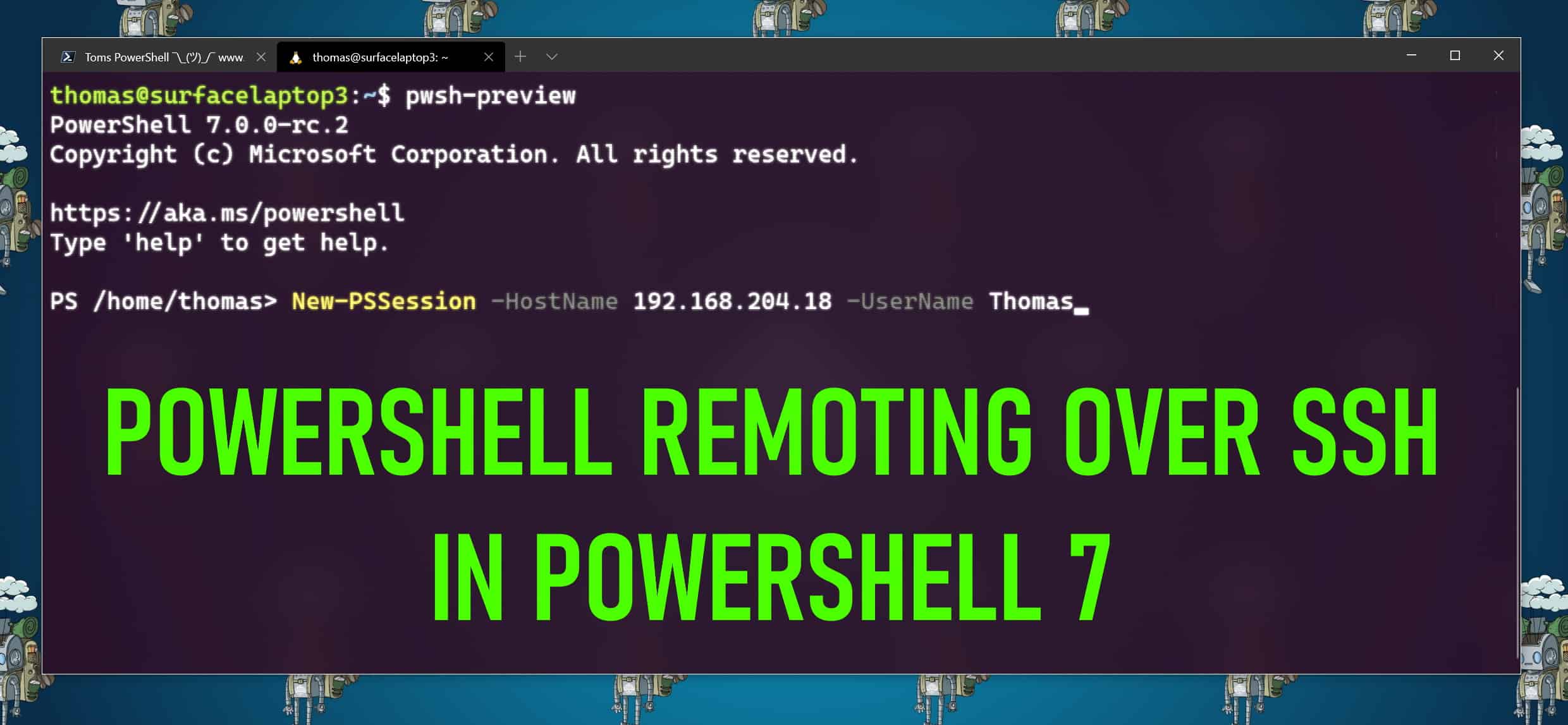
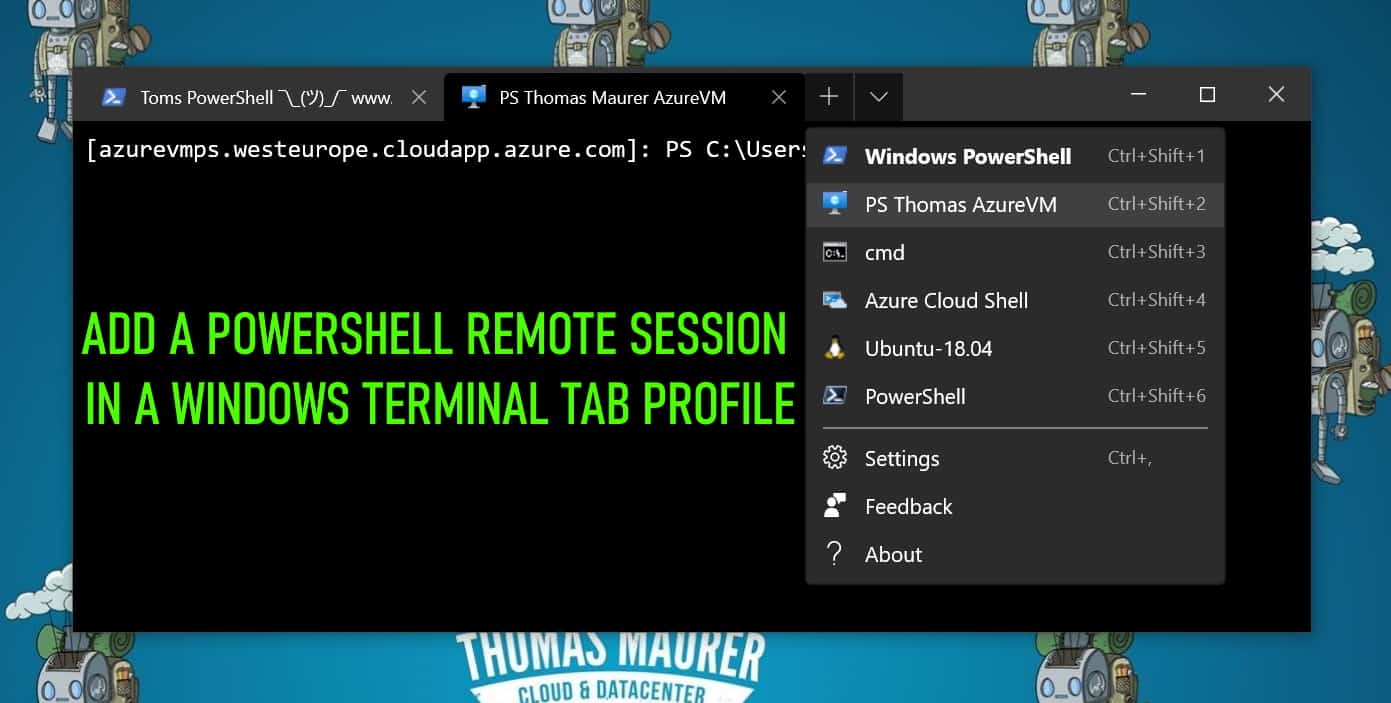
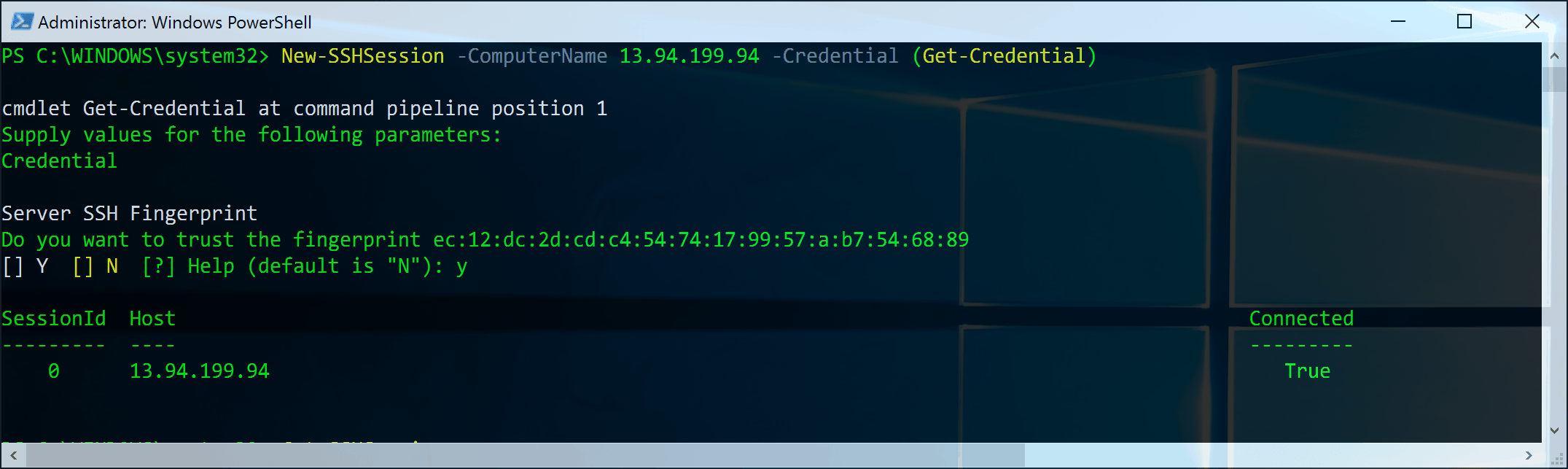
Enable PowerShell SSH Remoting in PowerShell 7
In this blog post, we will have a look at how you can enable and set up PowerShell SSH Remoting or PowerShell Remoting over SSh with...
Mastering Azure with Cloud Shell
There are multiple ways to interact and manage resources in Microsoft Azure. You can use the Azure Portal or command line tools like the...
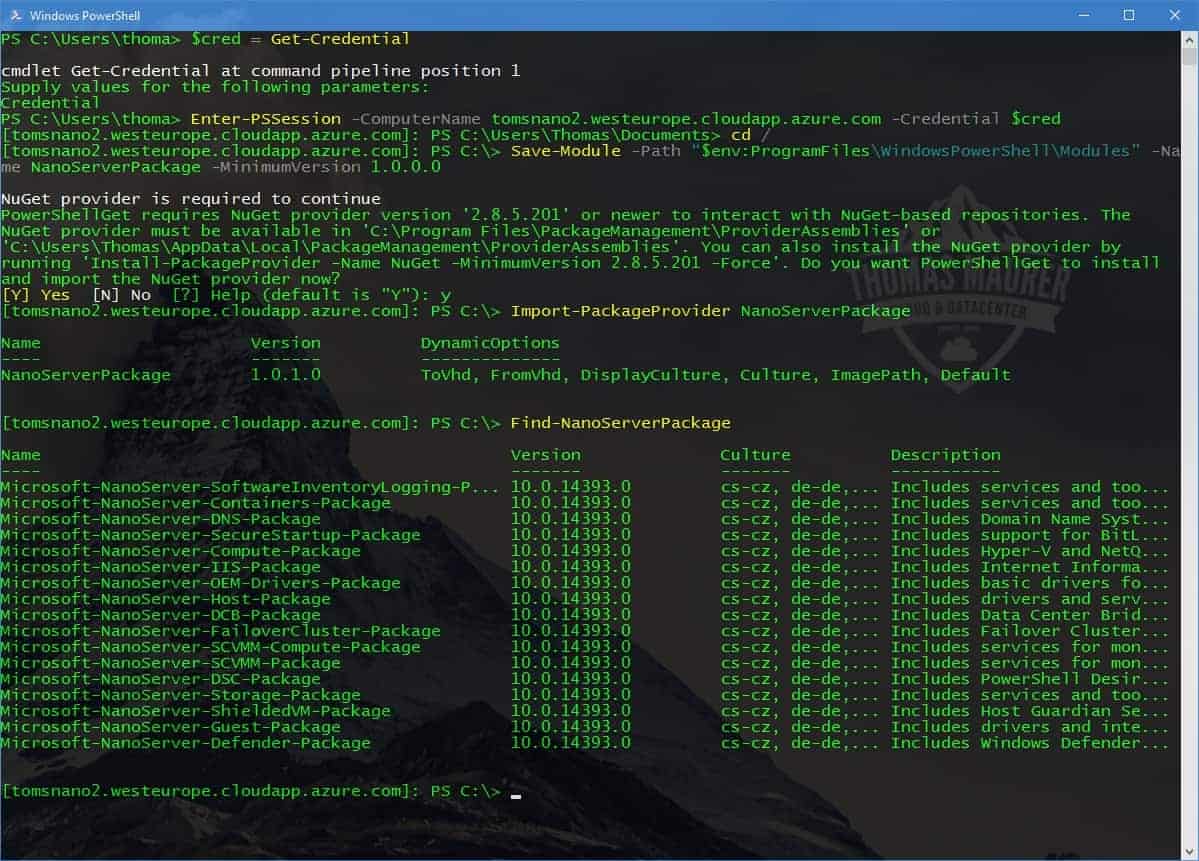
How to deploy Nano Server in Azure
In some other post I have written how you can deploy a Nano Server on premise using PowerShell or the Nano Server Image Builder. In this...
Using SSH with PowerShell
Microsoft announced that they will support SSH using PowerShell in Windows 10. Until now Microsoft...
How to Remote Manage your Nano Server using PowerShell
In a blog post some days ago I wrote how you can create your Nano Server Image and boot it inside a Virtual Machine. If you are familiar...
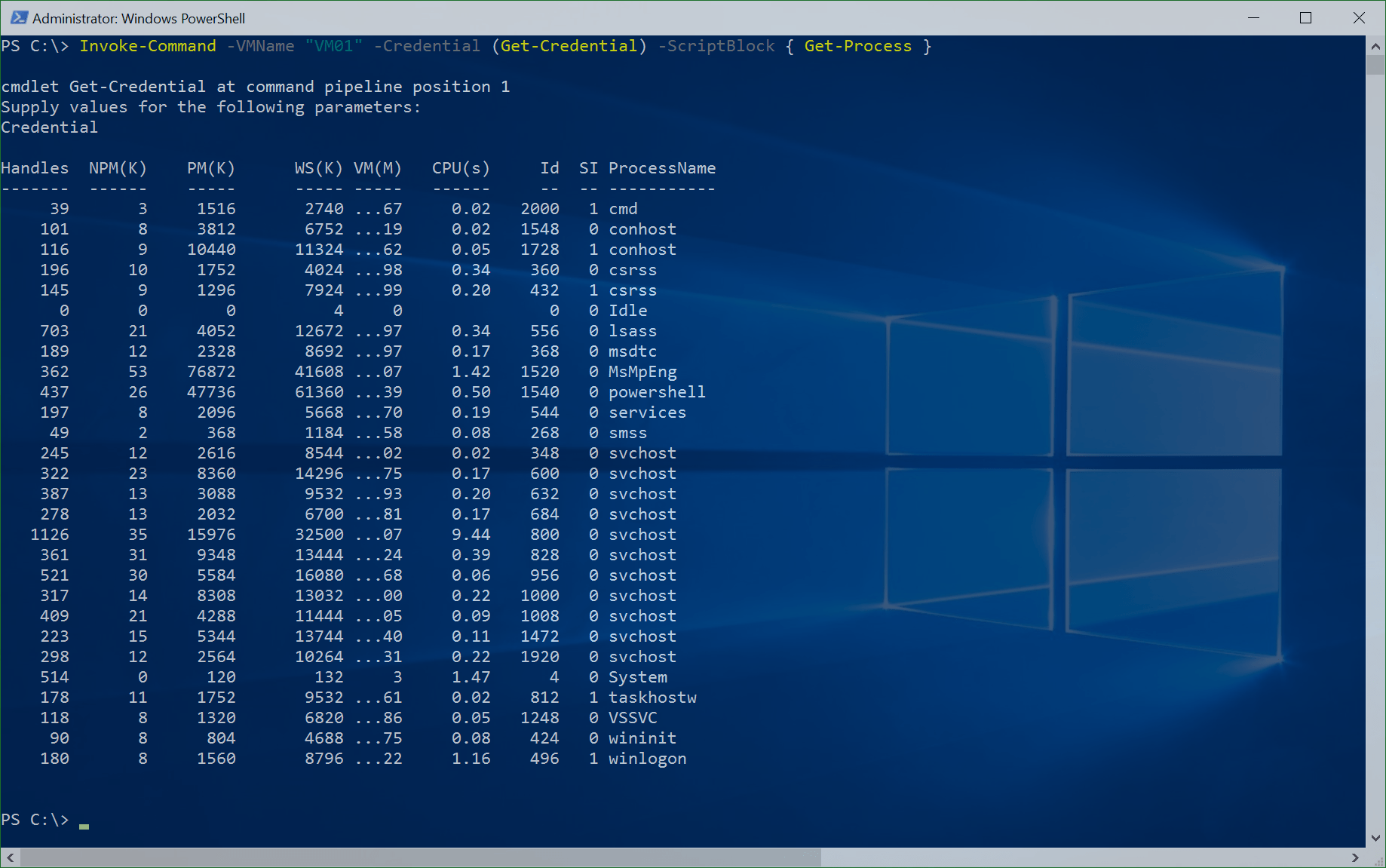
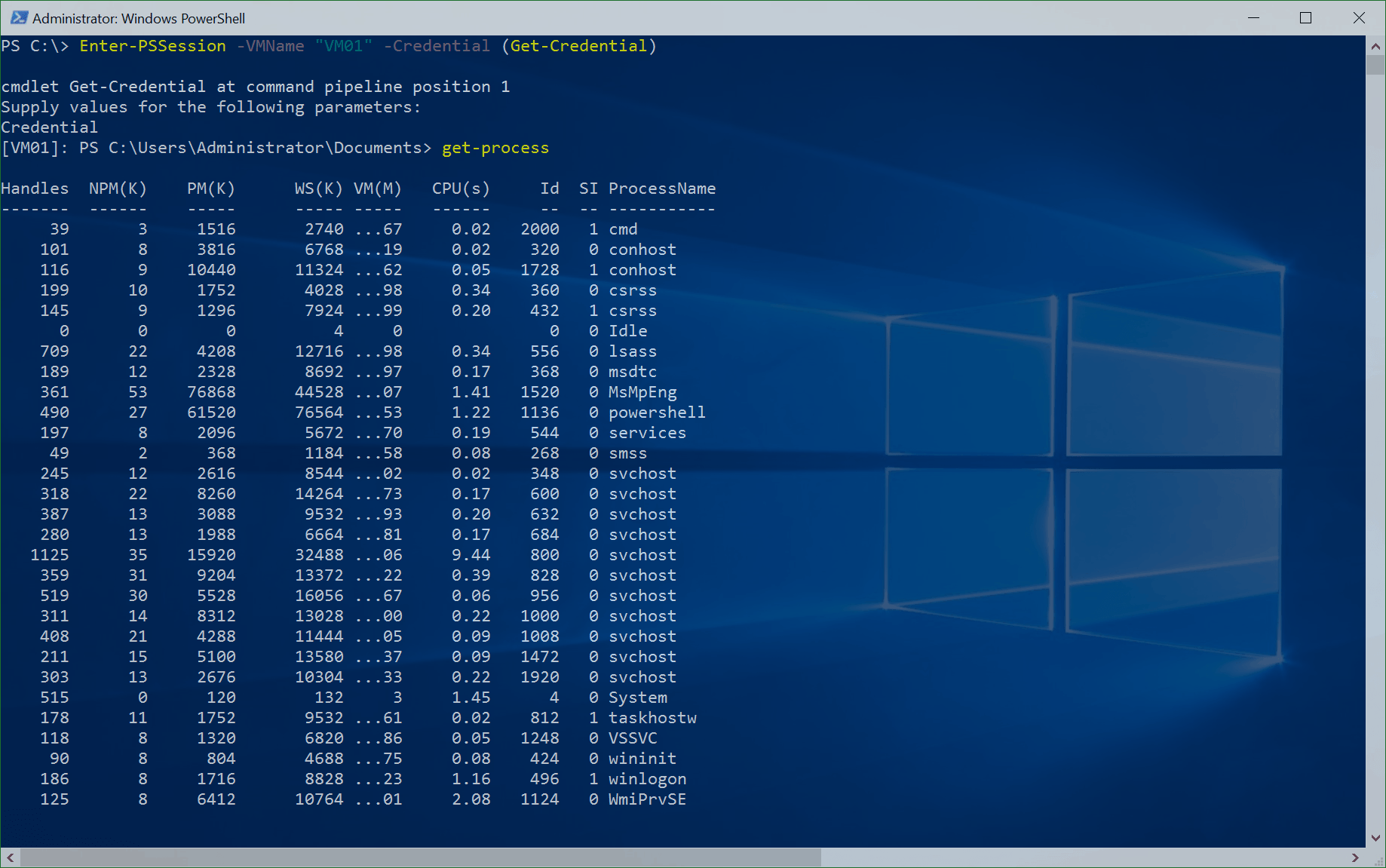
Hyper-V PowerShell Direct
One of the new features of Hyper-V in Windows Server 2016 and Windows 10 is called PowerShell Direct. PowerShell Direct lets you remotely...
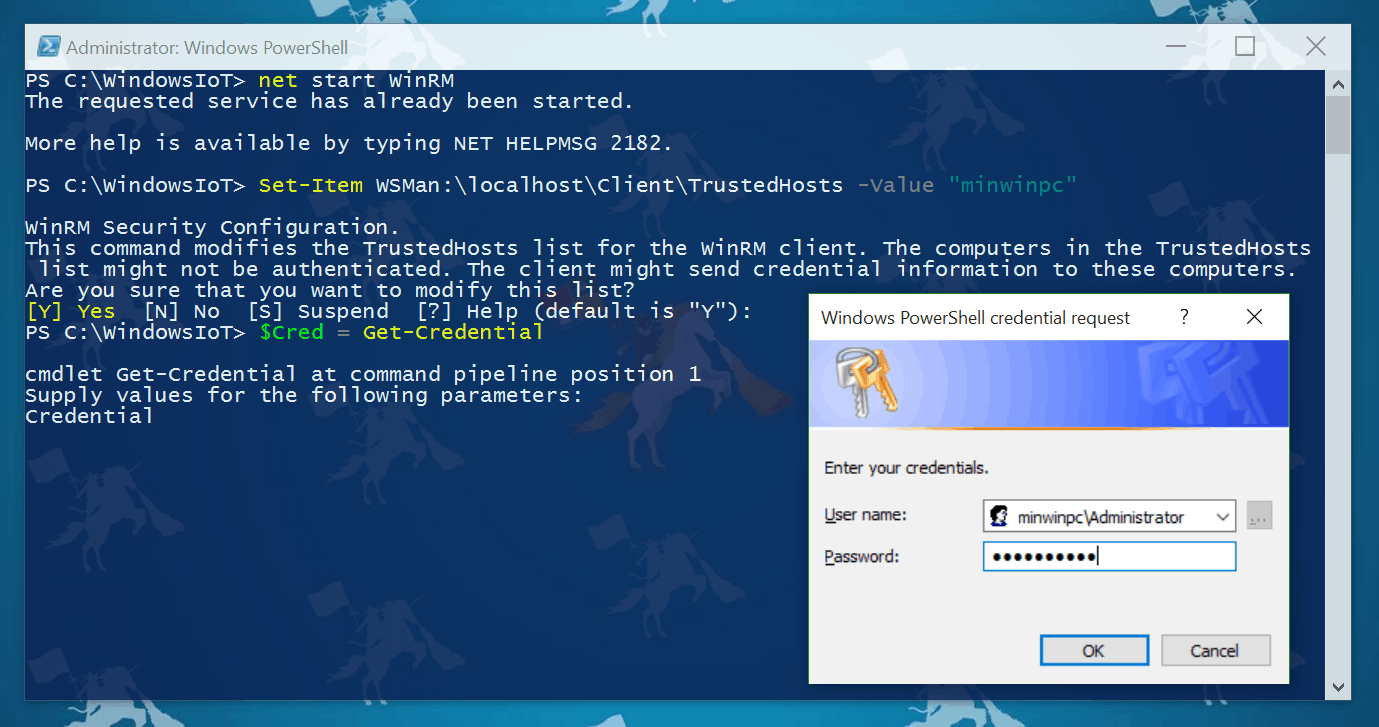
How to connect to Windows 10 IoT Core via PowerShell
After you have done the setup of your Raspberry Pi 2 with Windows 10 IoT Core you can now connected...