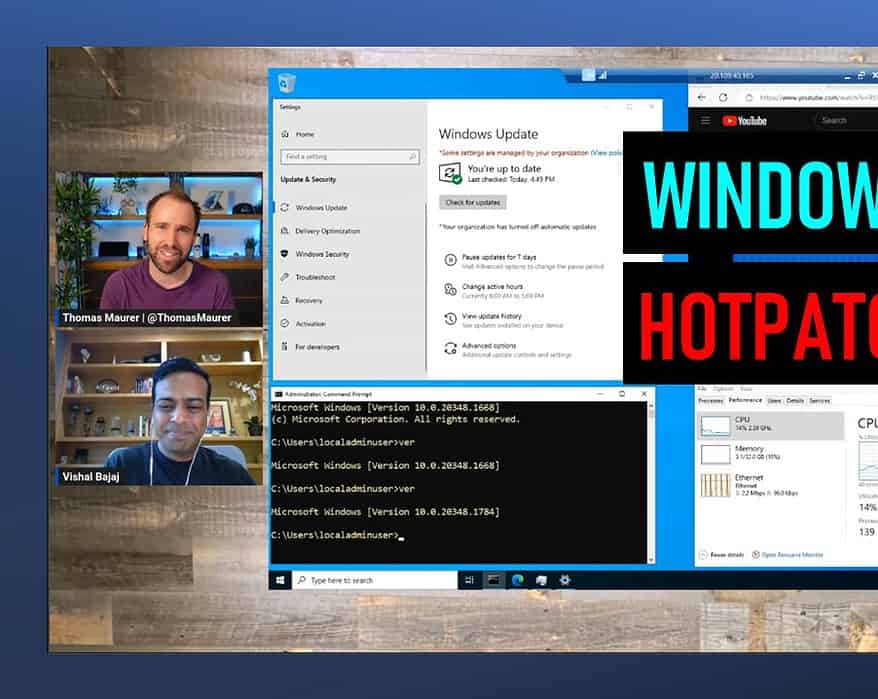
Hotpatching for Windows Server VMs on Azure with Desktop Experience
This week Microsoft announced the the General Availability of Hotpatching on Windows Server 2022...
How to In-place upgrade Windows Server in Microsoft Azure
Today I came across a tweet by Microsoft Program Manager Ned Pyle mentioning that in-place upgrade for Windows Server VMs in Microsoft...
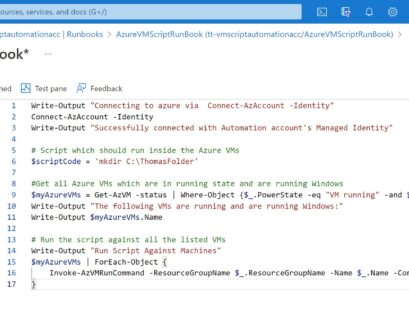
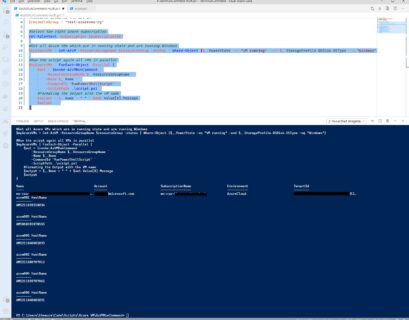
Schedule and Run PowerShell Scripts for Azure VMs using Azure Automation
A while ago I wrote a blog post on how you can run a PowerShell or Bash script against multiple Azure Virtual Machines (VMs) using Run...
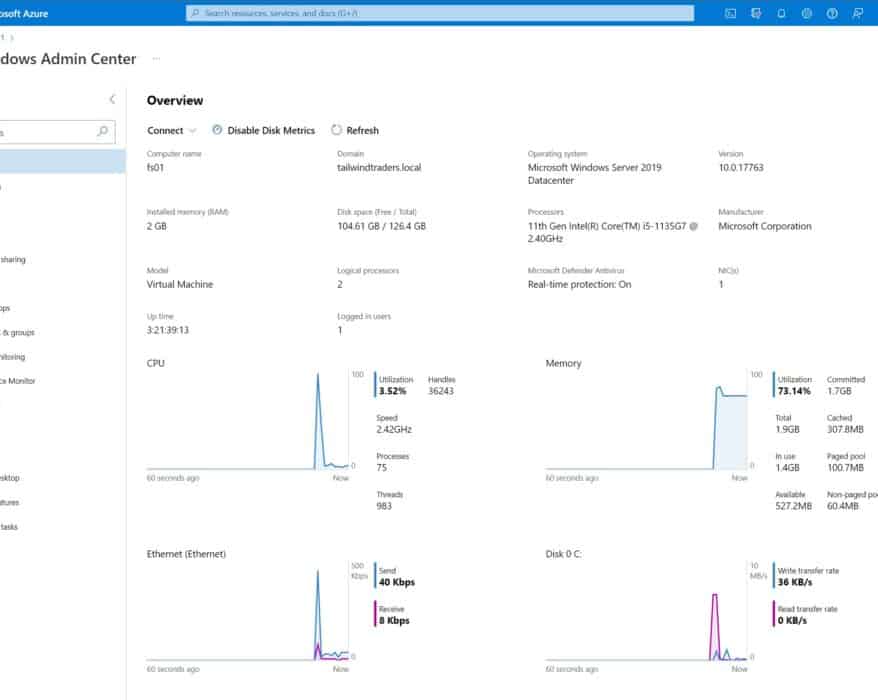
Manage Arc-enabled Windows Server with Windows Admin Center in the Azure Portal
With a new feature called Windows Admin Center in the Azure portal, you can now securely manage...
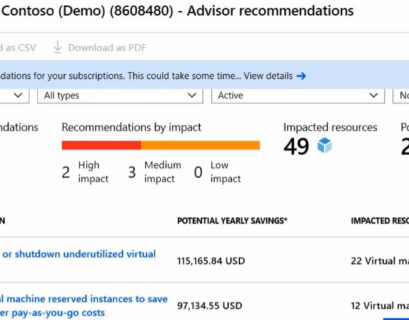
Azure Advisor: How to Improve performance, security, and reliability of your Azure VMs
Running virtual machines in Azure is great. However, there are a lot of things you need to think about to improve performance, security,...
How to run scripts against multiple Azure VMs by using Run Command
I wrote a blog post on how to run scripts in your Azure VM by using Run Command, and explained how handy this feature is to manage Azure...
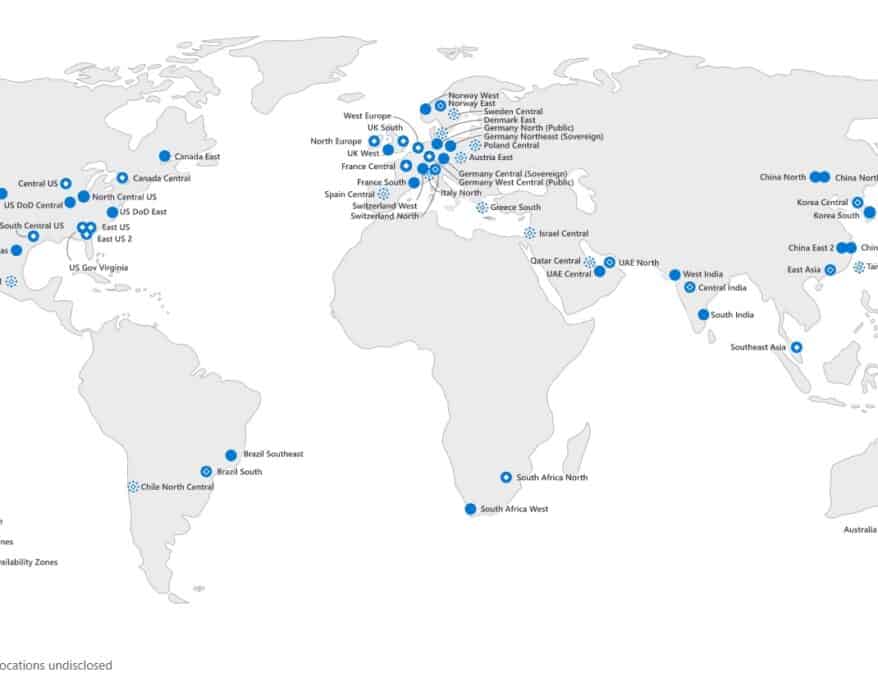
How to check the available VM Sizes (SKUs) by Azure Region
Do you want to know which Azure VM (virtual machine) sizes are available in an Azure region? Here...
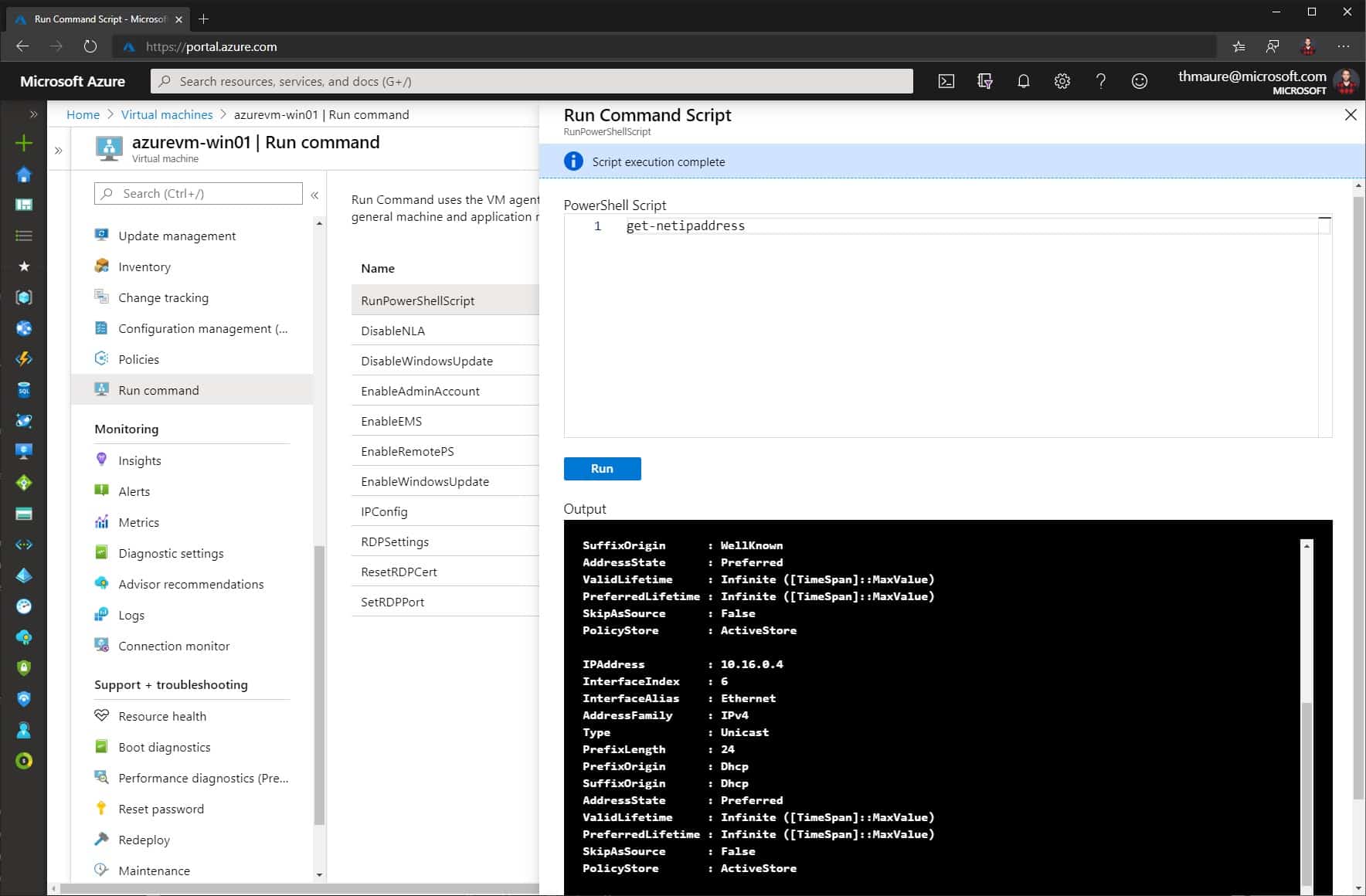
How to Run Scripts in your Azure VM using Run Command
You can access your Azure IaaS virtual machine (VM) in multiple ways like SSH or RDP, depending on your operating system and configuration....