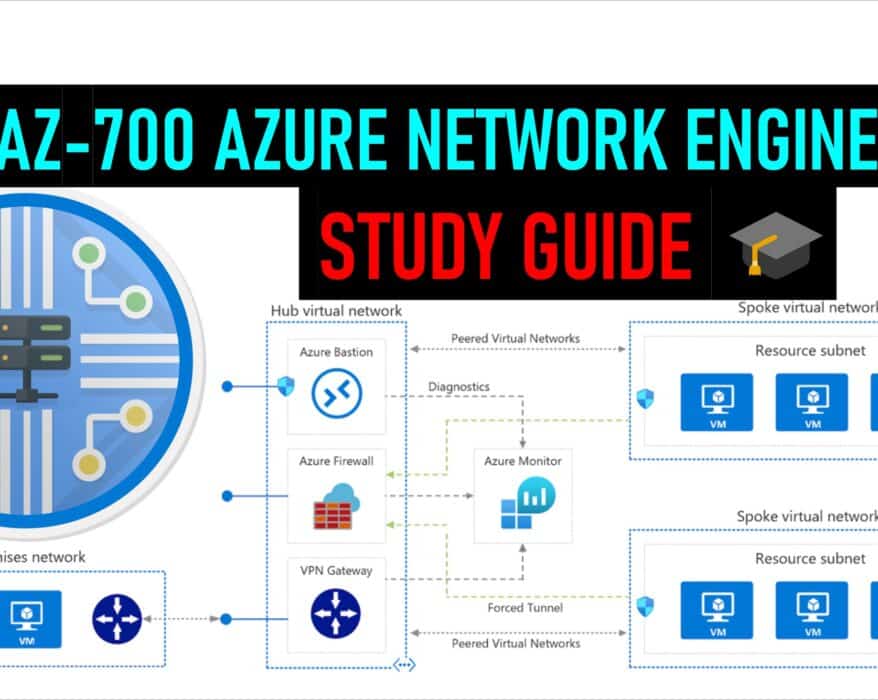
AZ-700 Study Guide: Azure Network Engineer
Microsoft announced the new beta exam Exam AZ-700 Designing and Implementing Microsoft Azure...
Install Intel NUC Windows Server 2019 Network Adapter Driver
As you know, I am using an Intel NUC as my Windows Server lab machine, where I run Windows Server 2019 and Hyper-V on. Many people asked me...
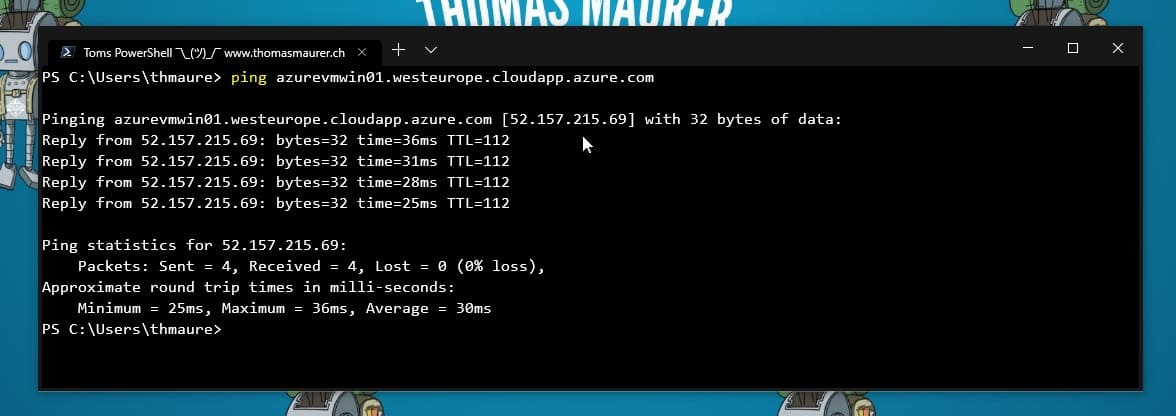
How to enable Ping (ICMP echo) on an Azure VM
This is just a very quick blog post because I got the question from a couple of people. In this blog post want to show you how you can...
How to set up Windows Server Azure Network Adapter
In my series about Windows Server 2019, I have a new feature I want to introduce to you, called the...
My Hardware Recommendations for Windows Server 2016
Many people are right now asking me about what they have to look out for, if they are going to buy hardware for there next Windows Server...
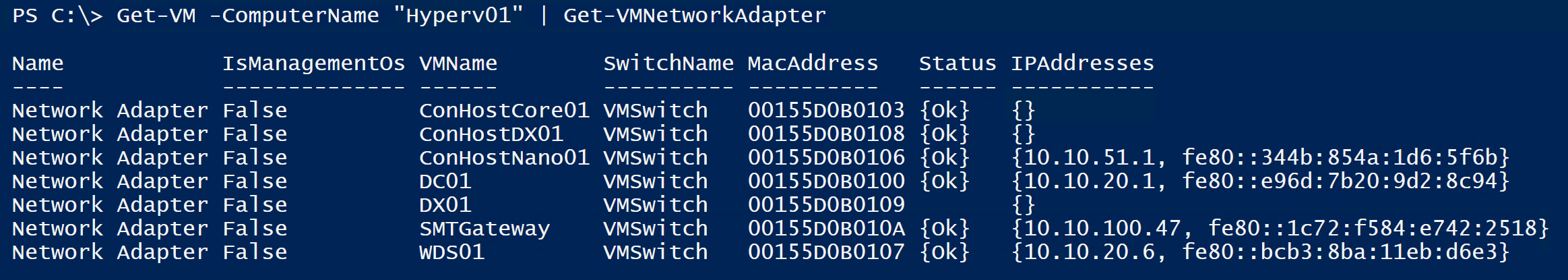
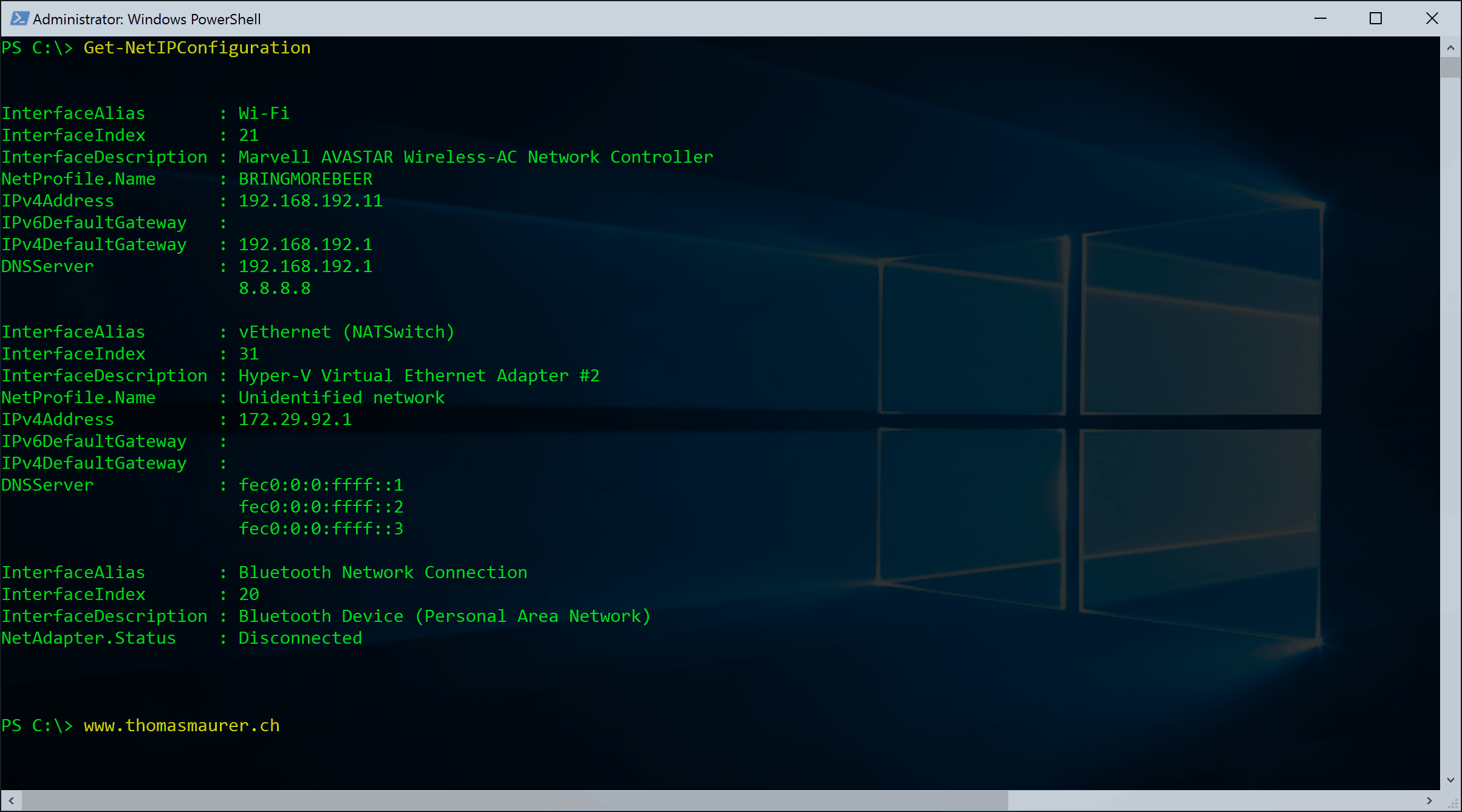
PowerShell One-liner to list IP Addresses of Hyper-V Virtual Machines
Here a very quick PowerShell command to list all the Virtual Network Adapters, including IP Addresses of Virtual Machines running on a...
Basic Networking PowerShell cmdlets cheatsheet to replace netsh, ipconfig, nslookup and more
Around 4 years ago I wrote a blog post about how to Replace netsh with Windows PowerShell which...
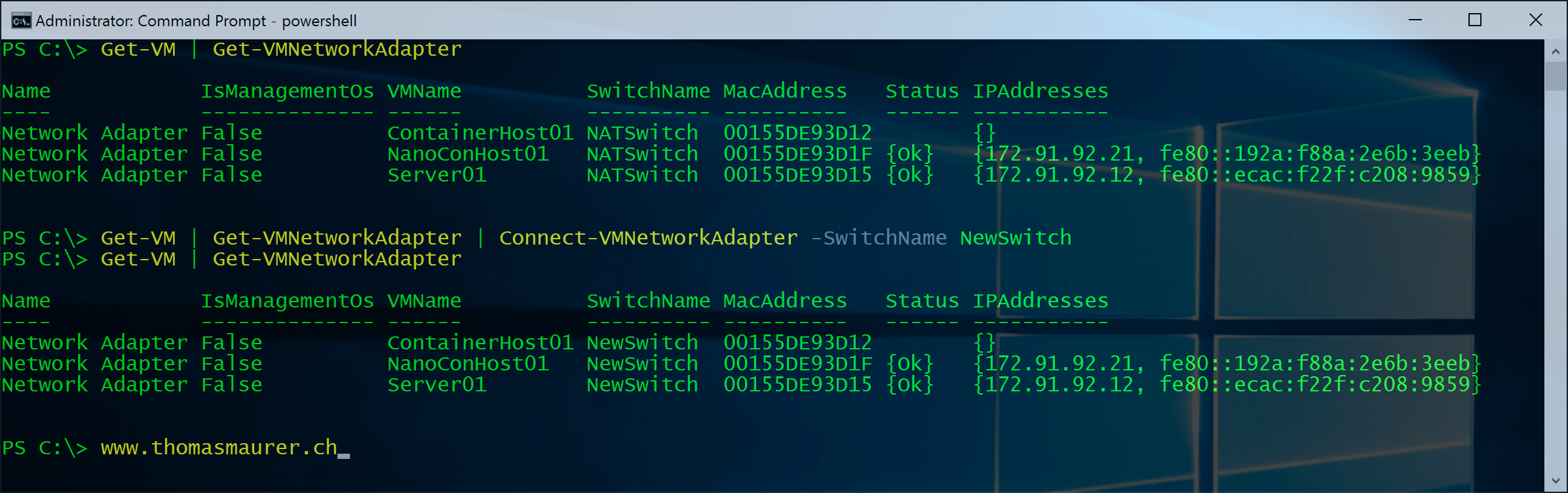
Change Hyper-V VM Switch of Virtual Machines using PowerShell
This is one of the first post of a short blog series with some simple PowerShell scripts and oneliners for Hyper-V. One this is how you...
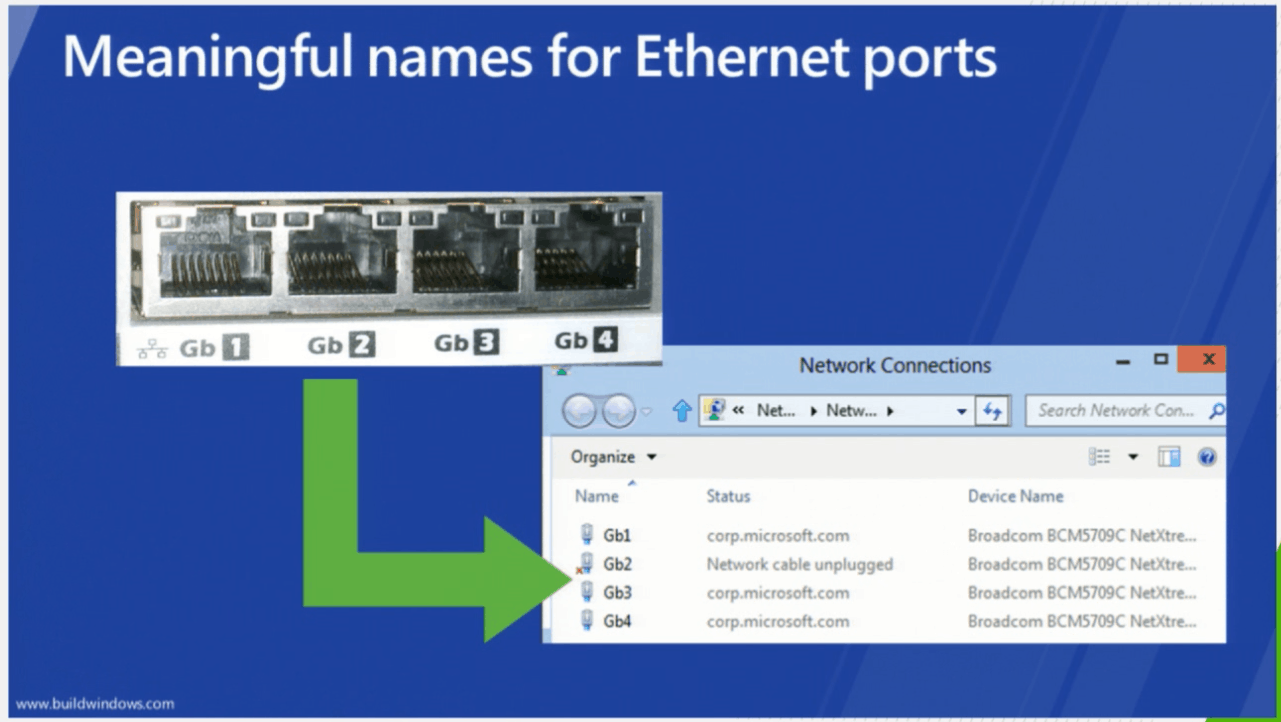
Cisco UCS supports Consistent Device Naming (CDN)
Yesterday I posted about Cisco UCS supporting RDMA (SMB Direct) with firmware version 2.2(4b)B. Walter Dey, former Cisco Distinguished...
Passed Microsoft Exam 70-533 Implementing Microsoft Azure Infrastructure Solutions
A couple of weeks ago I passed Microsoft Exam 70-533 Implementing Microsoft Azure Infrastructure...