Deploy and Install Windows Admin Center in an Azure VM
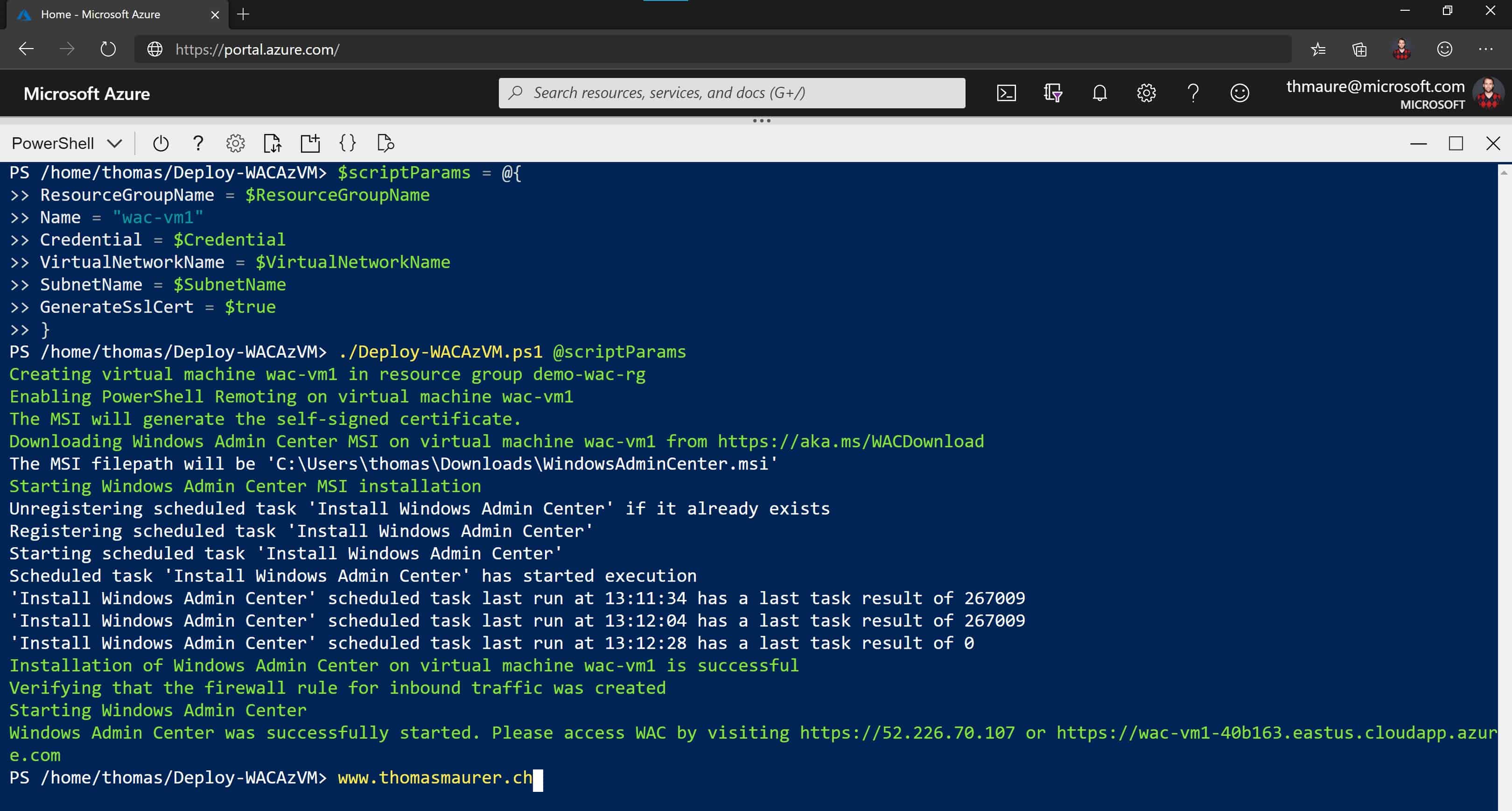
The great thing about Windows Admin Center (WAC) you manage every Windows Server doesn’t...
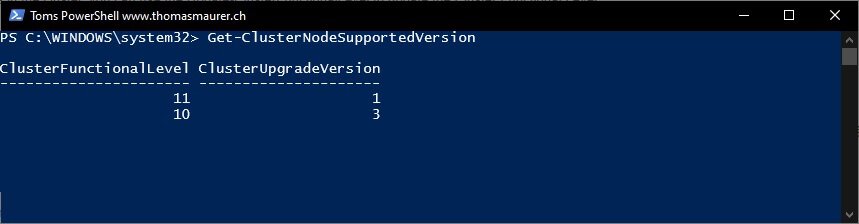
Learn about Windows Server Cluster Functional Levels
A couple of weeks ago, I released a blog post about Hyper-V VM Configuration versions to give an overview about the version history of...
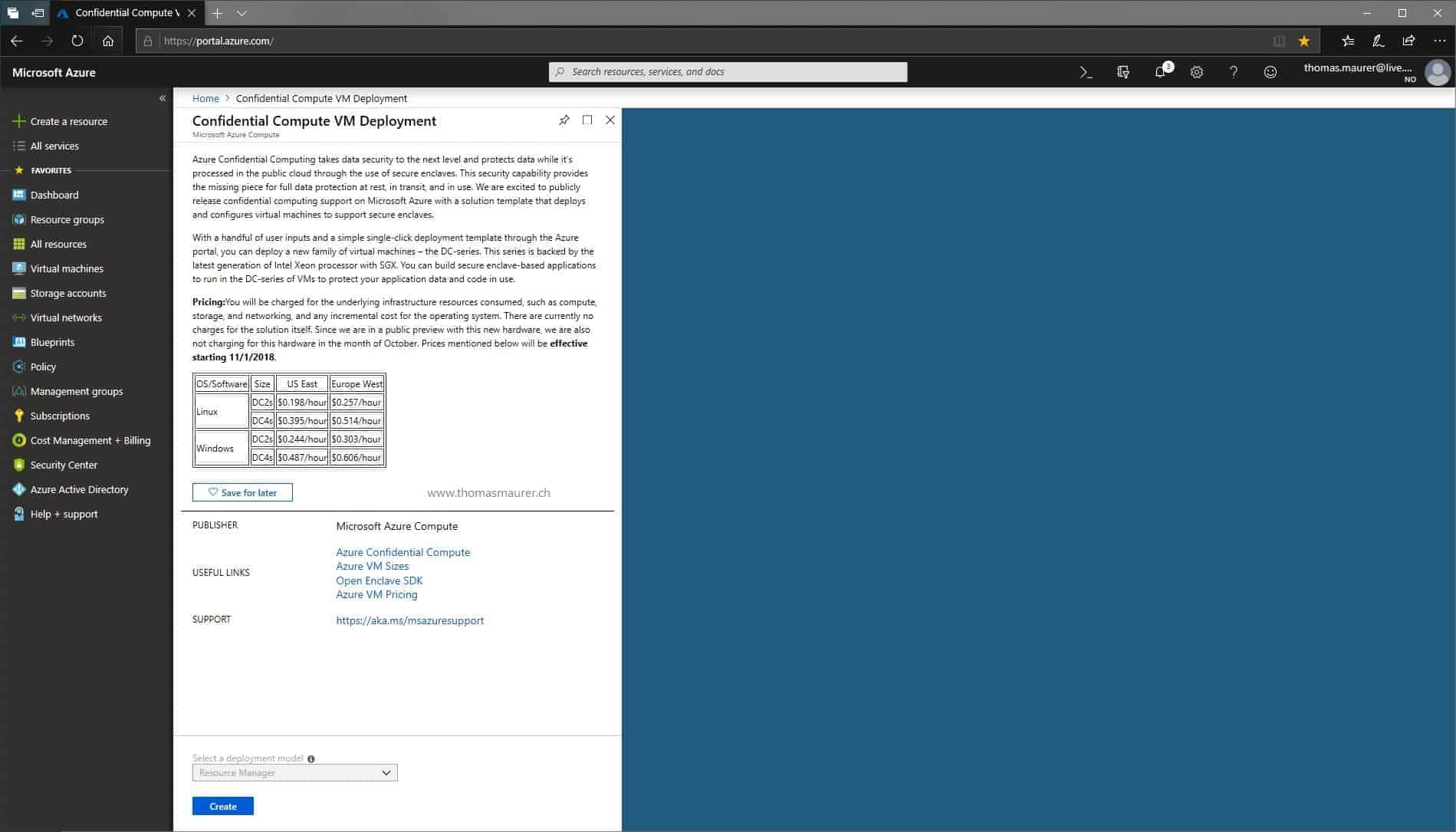
Protect Workloads with Azure Confidential Computing
A year ago Microsoft announced that they were working on a new technology in Azure to protect and encrypt data in use, called Azure...
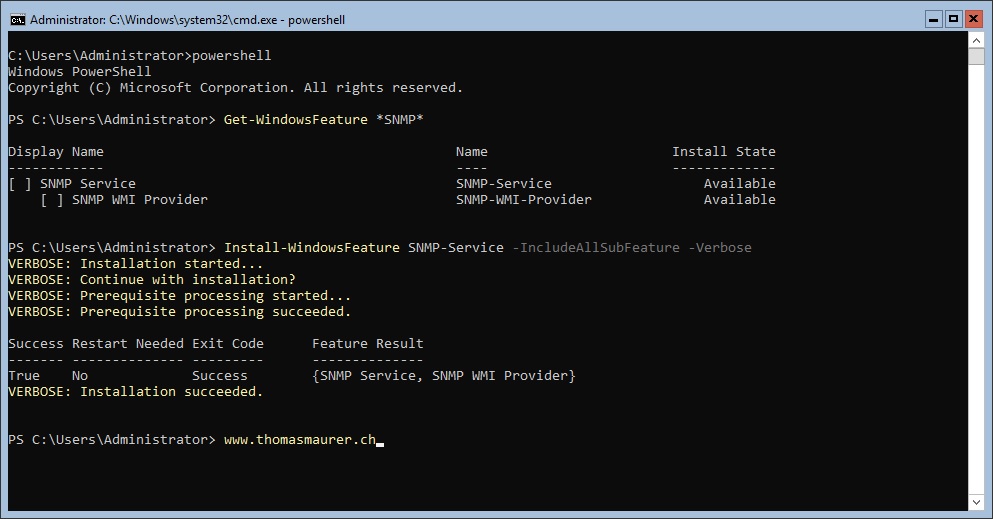
Install SNMP on Windows Server Core
If you run Windows Server as Core Installation, like Windows Server 2016 Core or any Microsoft...
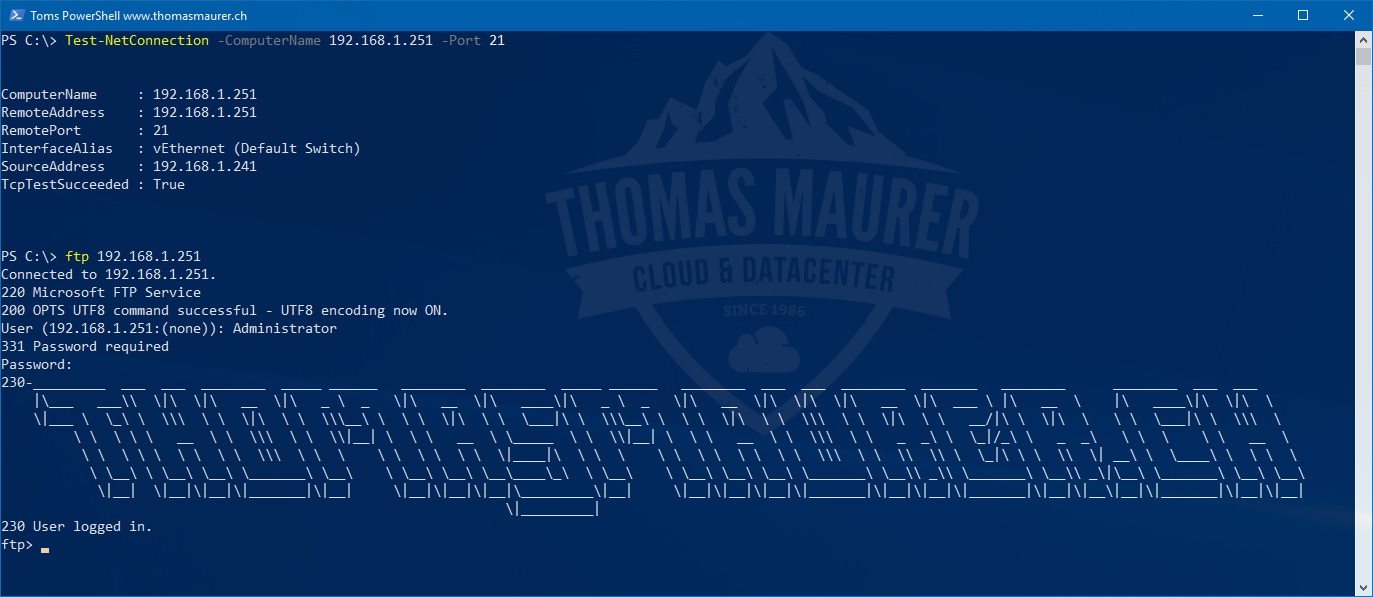
Install FTP Server on Windows Server
Windows Server has IIS build in, which also offers an FTP server option. The File Transfer Protocol (FTP) is still a very popular protocol...
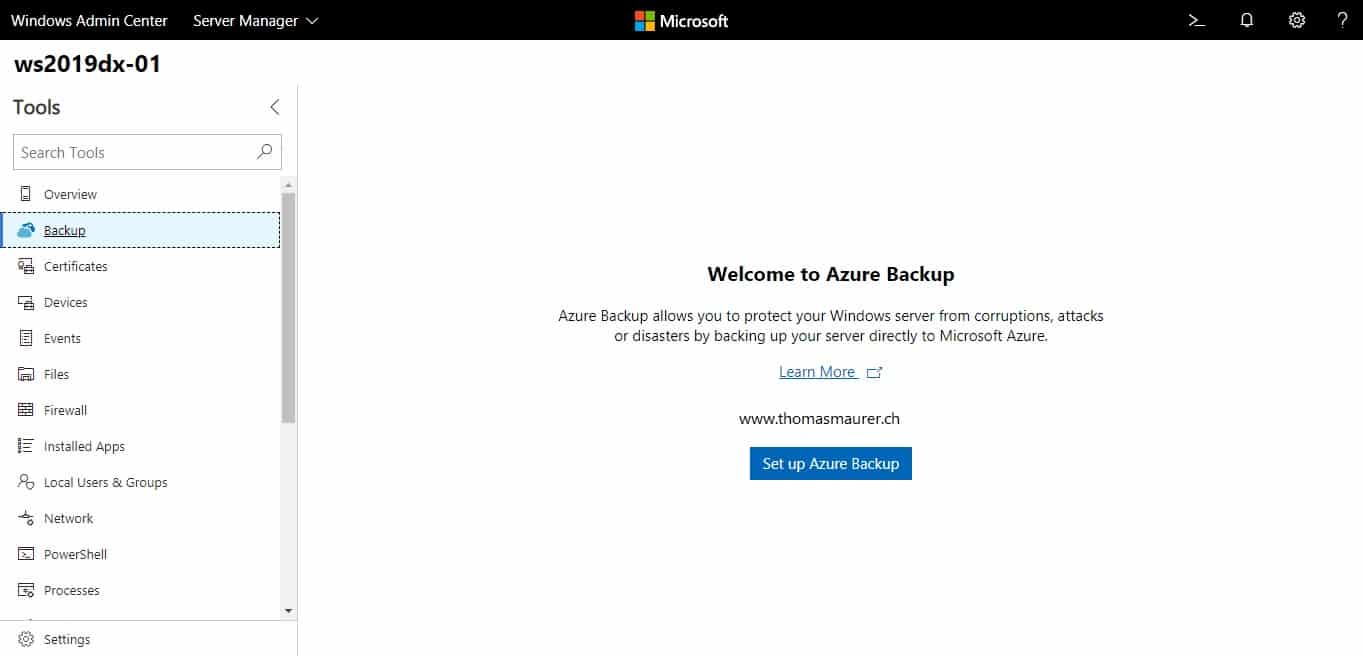
Set up Azure Backup in Windows Admin Center
With Windows Admin Center you have a great new web-based management experience for Windows Server. With Microsoft efforts to bring Hybrid...
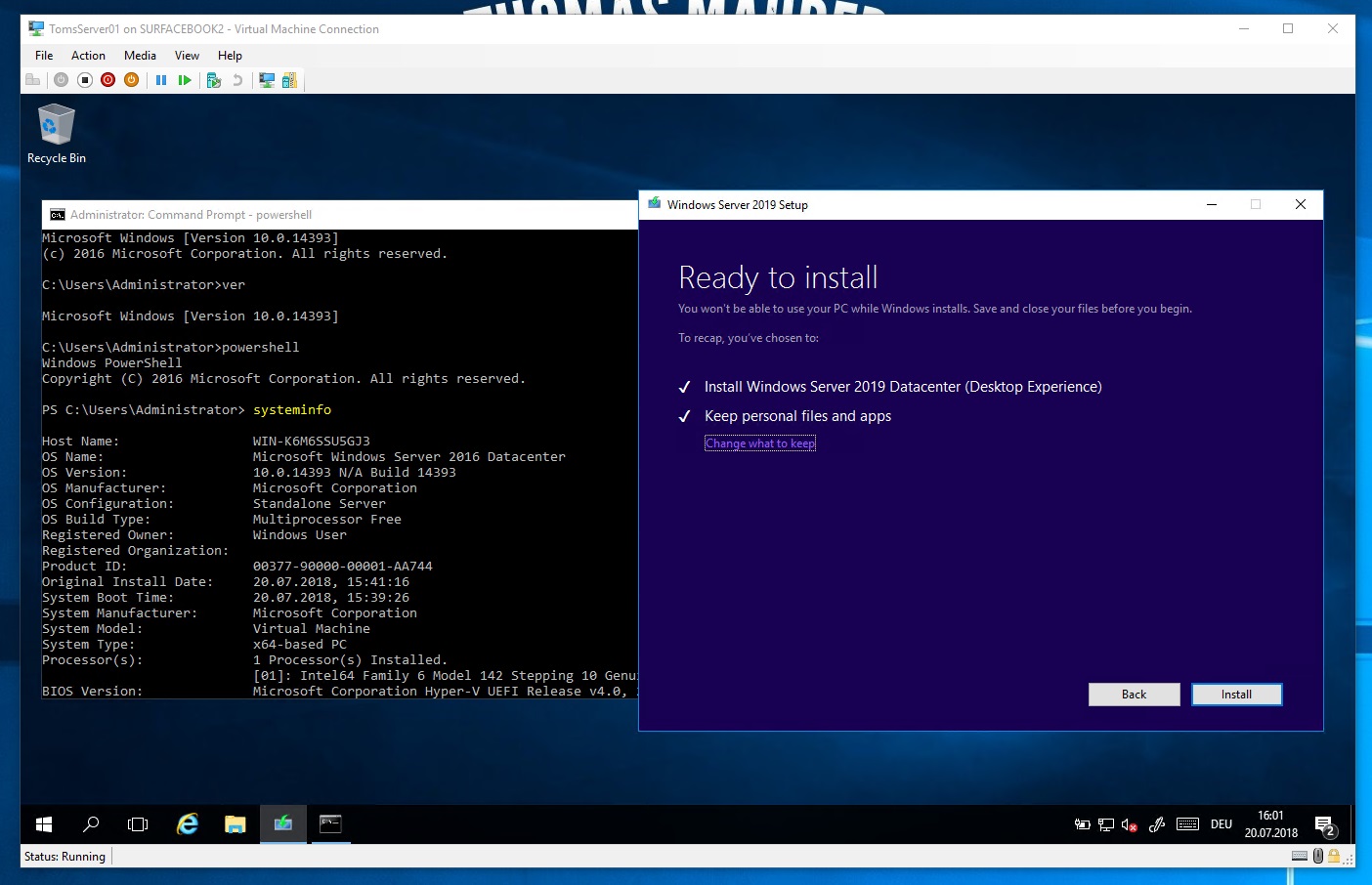
Windows Server 2019 In-place Upgrade
As another part of my series for Windows Server 2019, this blog post covers the in-place upgrade...
Install OpenSSH Server on Windows Server
Back in 2017 Microsoft made OpenSSH available on Windows 10. Shortly after OpenSSH was also available for Windows Server, version 1709....
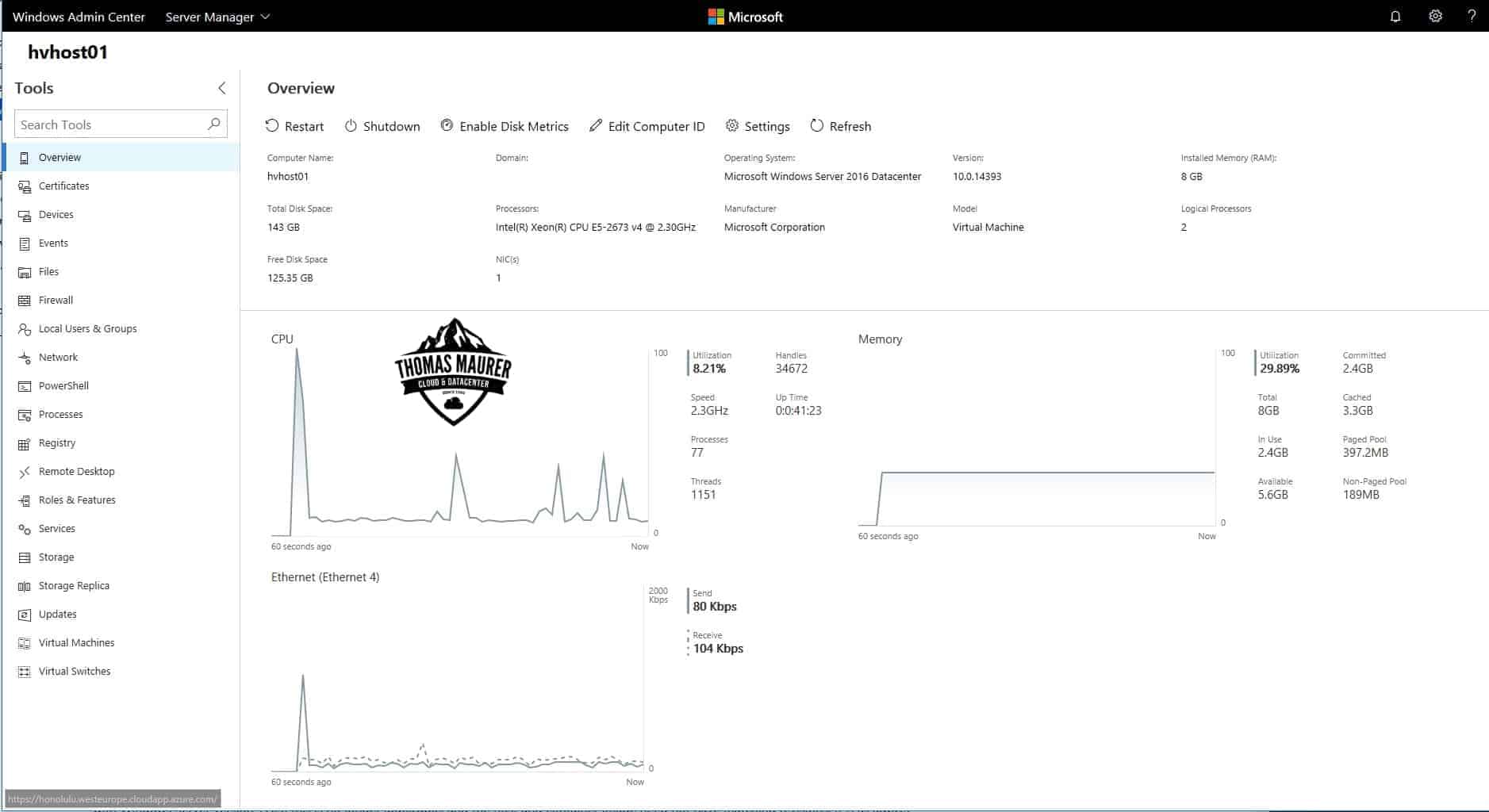
Windows Admin Center – The Next Generation Windows Server Management Experience
Back in September Microsoft released Project Honolulu, which is the codename for a new Windows Server management experience. Today...
Windows Server – Semi-Annual Channel (SAC) vs Long-Term Servicing Channel (LTSC)
Update March 2018: Microsoft Updated some of the information about the use cases of the Semi-Annual...