Connect Ubiquiti UniFi Dream Machine to Azure VPN
A couple of days ago I got a Ubiquiti UniFi Dream Machine, which is an all-in-one device with an...
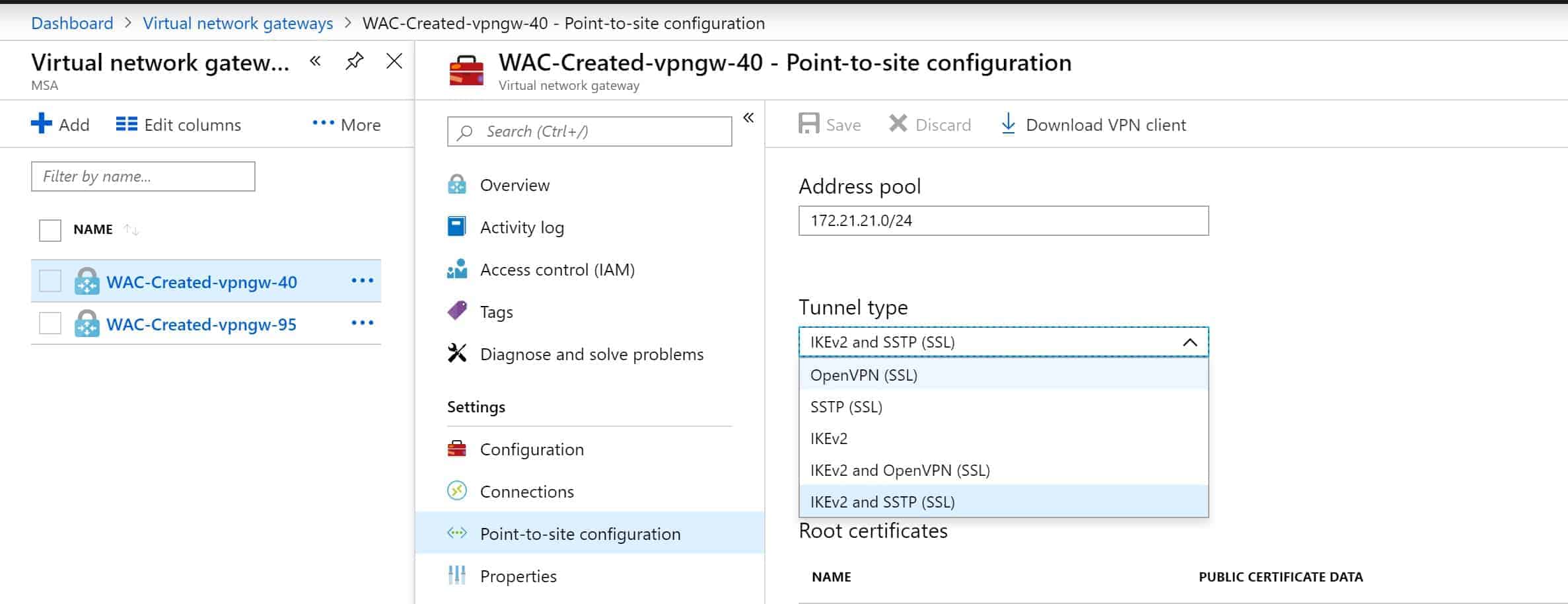
Create Azure P2S VPN with Azure AD authentication
A couple of days ago, we announced that you now can use Azure Active Directory to authentication Point-to-Site (P2S) VPN connections to...
OpenVPN support in Azure VPN gateways
Today, the Azure networking team announced the General Availability (GA) of OpenVPN protocol in Azure VPN gateways for P2S connectivity....
How to set up Windows Server Azure Network Adapter
In my series about Windows Server 2019, I have a new feature I want to introduce to you, called the...
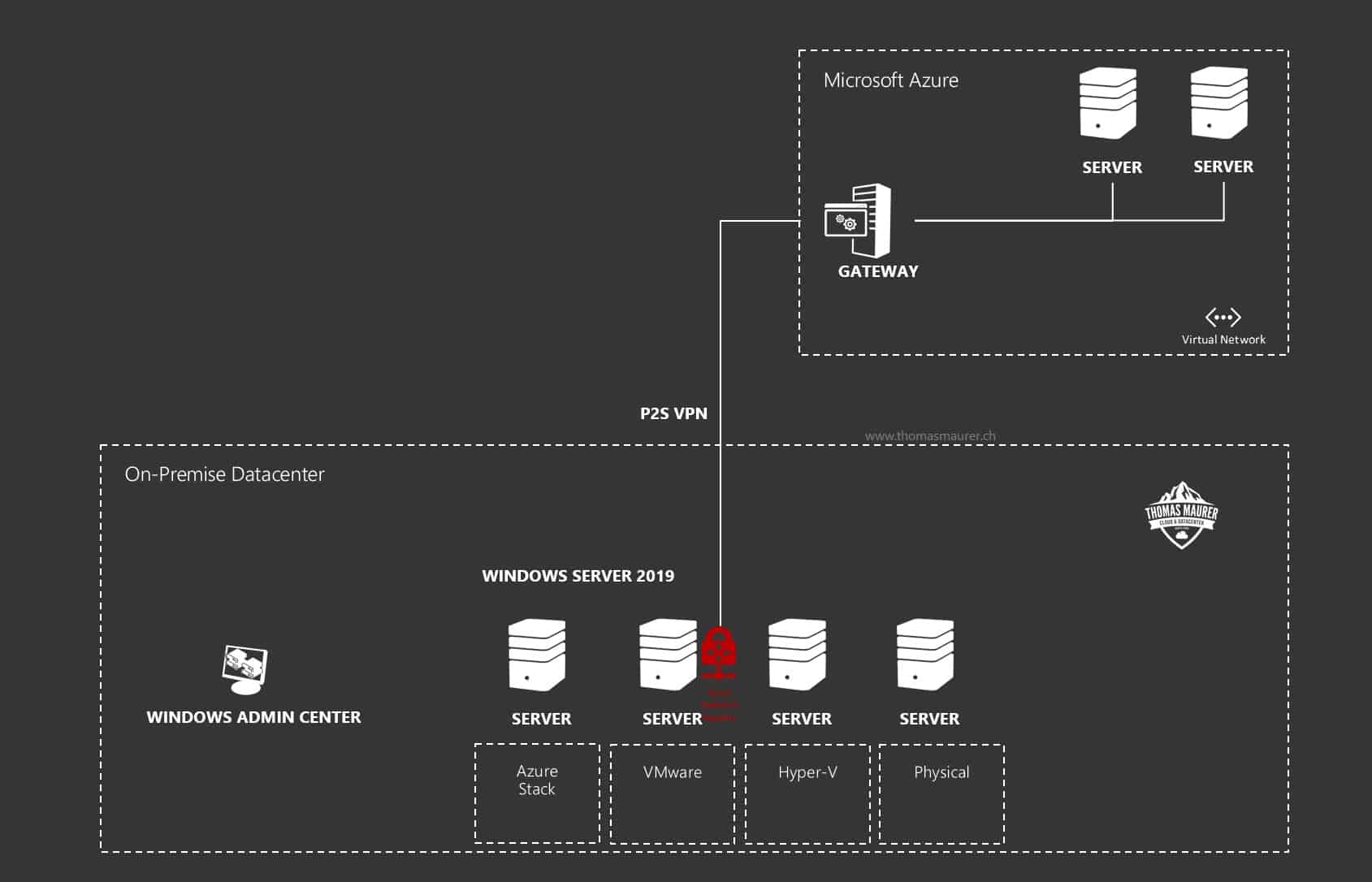
How to install VPN on Windows Server 2019
This blog post is a step by step guide how to install and configure VPN on Windows Server 2019. The blog post shows you how you can easily...
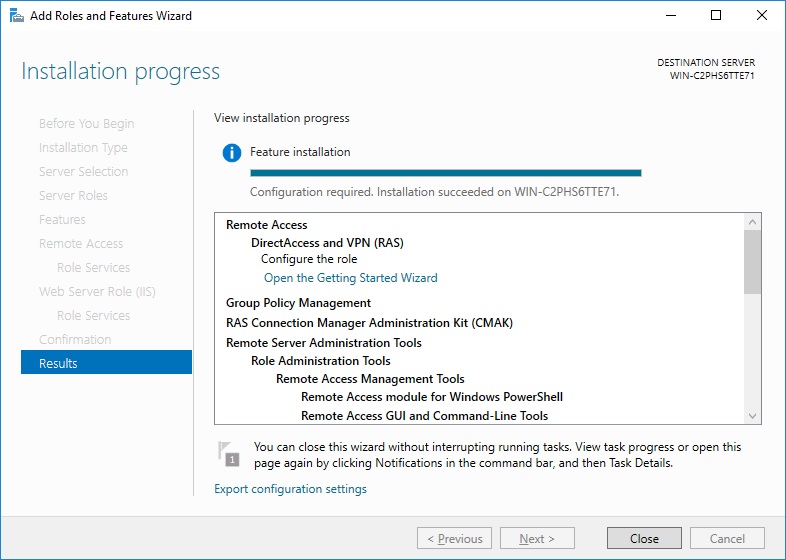
How to Install VPN on Windows Server 2016
This post shows you how you can install a VPN Server on Windows Server 2016 Step-by-Step. It shows you how you can easily setup a VPN...
Green Cloud based on Windows Server Hyper-V and Windows Azure Pack
If you try to host some IaaS workloads or build a Hybrid Cloud environment connected to a service...
How to Install VPN on Windows Server 2012 R2
This post shows you how you can install a VPN Server on Windows Server 2012 R2 Step-by-Step. It shows you how you can easily setup a VPN...
How to Install VPN on Windows Server 2012
This post should show you how to install a VPN Server on Windows Server 2012. This post covers a VPN server for a small environment or for...
Remove a VPN connection in Windows 7
In Windows 7 you an create VPN connections for PPTP, L2TP or SSTP. To delete a connection you can...