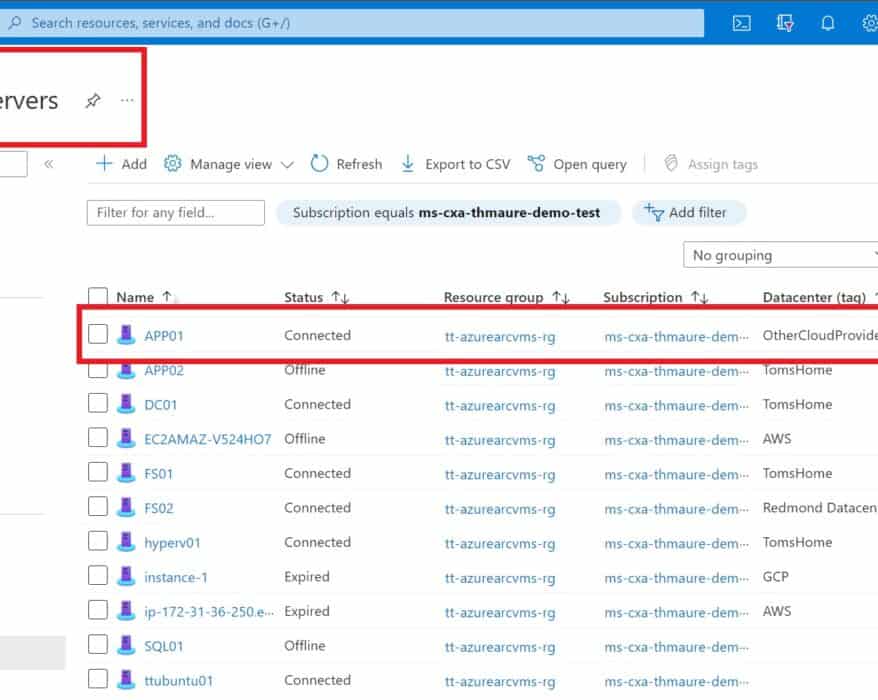
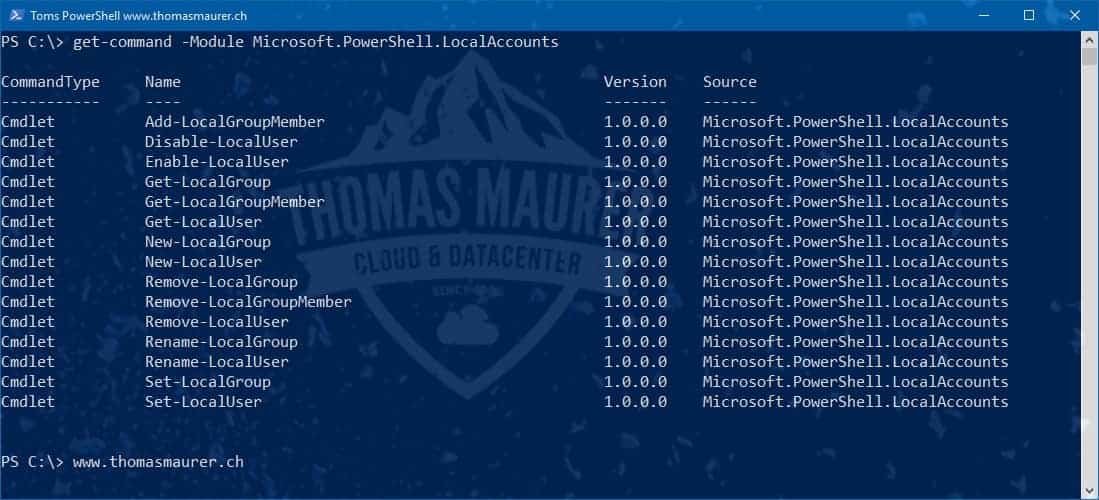
Use the Azure Arc Managed Identity with Azure PowerShell
In this blog post we are going to have a look at how you can use the Azure Arc provided Azure...
Create Azure P2S VPN with Azure AD authentication
A couple of days ago, we announced that you now can use Azure Active Directory to authentication Point-to-Site (P2S) VPN connections to...