Microsoft Windows Server 2016 Performance Tuning Guide
Yesterday Microsoft released the official Windows Server 2016 Performance Tuning Guide. The guide...
Change Office 365 password expiration policy
Well if you are using Office 365 and you may have the need to change the password expiration policy for some accounts. (Important: This is...
Manage Windows Azure AD using Windows PowerShell
Well I am a huge fan of Microsoft Office 365 and we are not only using this in our company, I am...
Windows Server 2012 Hyper-V: How to clone a Virtual Domain Controller
In Windows Server 2012 added a lot of improvements to Hyper-V and Active Directory. One of Microsoft strategic goals is to virtualize every...
Automated Active Directory Deployment with PowerShell
For a small presentation at KTSI I created a PowerShell script will automatically will deploys Active Directory Servers, adds other member...
How to add a Windows Server 2008 R2 Core as Secondary Domain Controller (replica)
This is a small How to which shows you how you can add a Windows Server 2008 R2 Core as a Secondary...
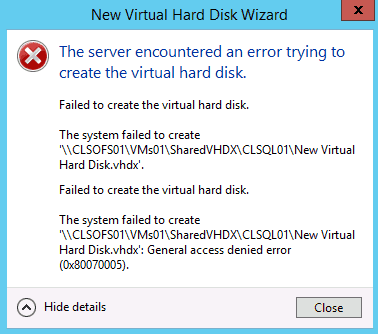
Time sync problems with Hyper-V Guests
If you have time sync problems with Hyper-V Guest Systems there is a simple solution for this. Problems: Time between Server and Active...