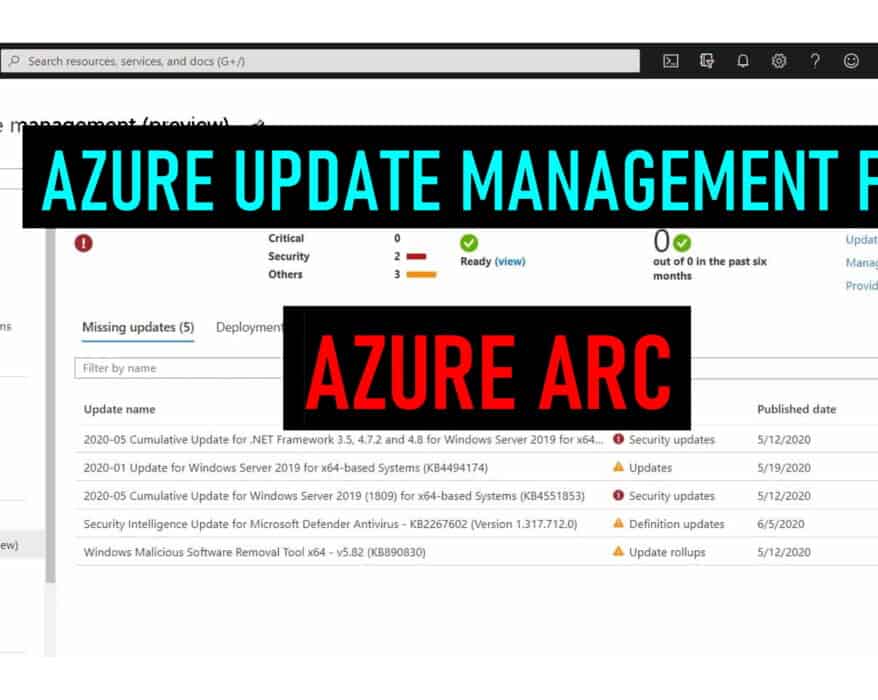
Manage updates of servers using Microsoft Azure Arc
The Azure Update Management solution is part of Azure Automation. And with Azure Update Management...
Manage updates and patches for your Azure VMs
In this week’s Azure tip video we are going to have a look at how to manage updates and patches for your Azure virtual machines...
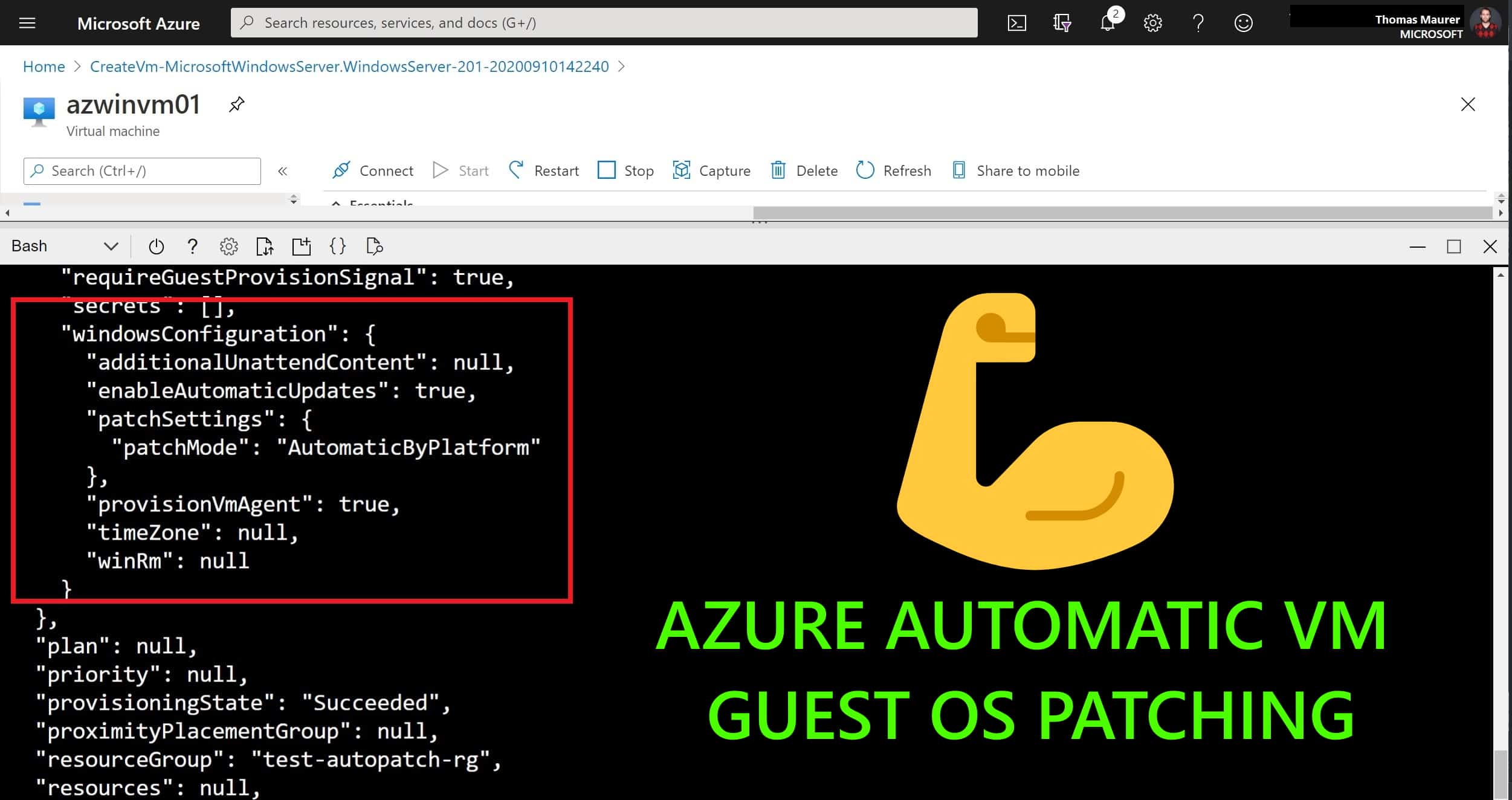
How to configure Azure Automatic VM guest OS patching
If you want to keep your Azure virtual machines (VMs) up-to-date, then there is a service called Azure Update Management, which helps you...
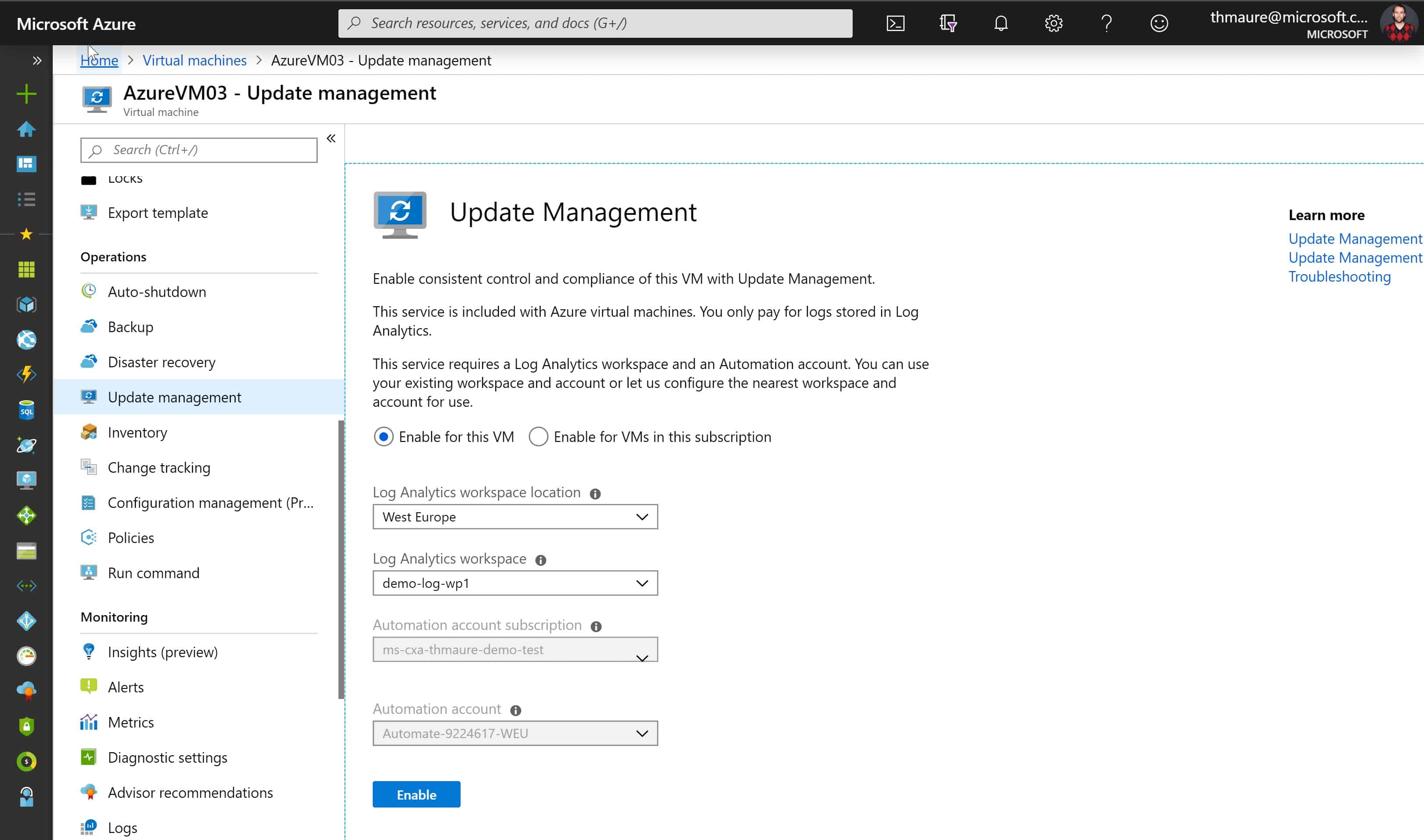
How to Manage Updates for Azure IaaS VMs
As a lot of customers are moving their workloads to Azure and specifically moving virtual machines...
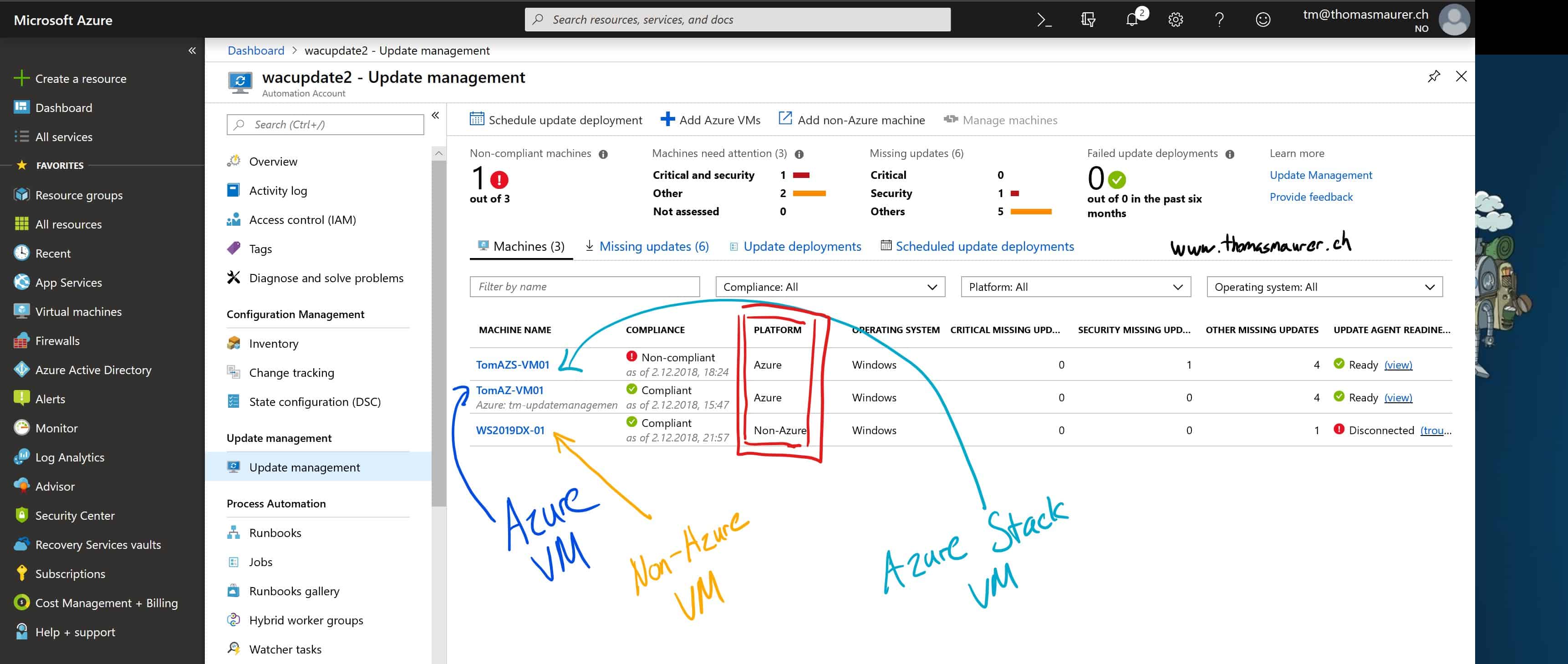
Using Azure Update Management on Azure Stack
At Microsoft Ignite 2018, Microsoft announced the integration of Azure Update and Configuration Management on Azure Stack. This is a...
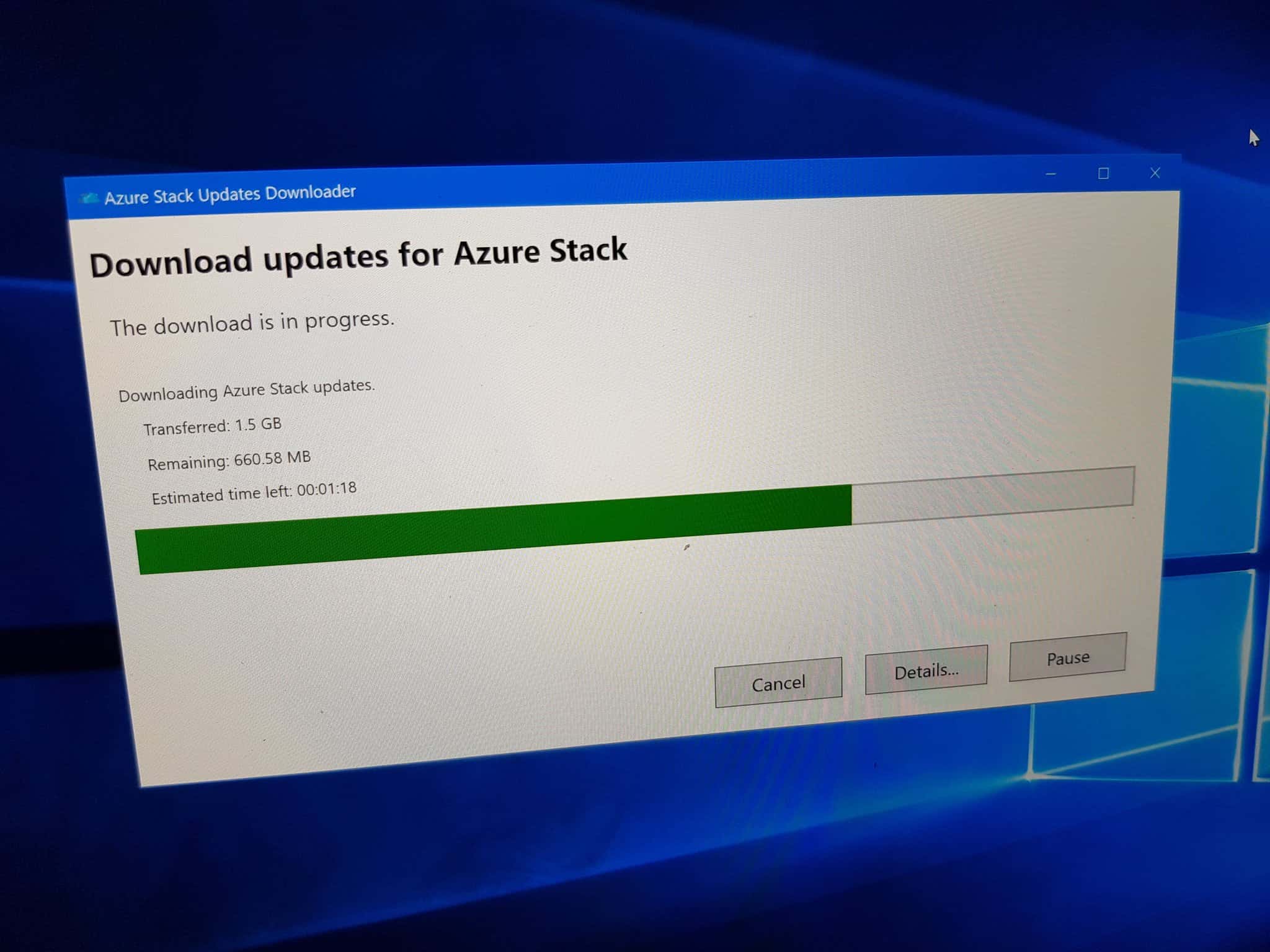
How to install and manage Azure Stack Updates
At itnetX, we help customers to implement as well as to operate Azure Stack. One part of operating Azure Stack is keeping it up-to-date....
Windows Server release information – Windows Server Semi-Annual Channel and LTSC
As mentioned a couple of months ago, Microsoft has updated the Windows Server servicing model. The...
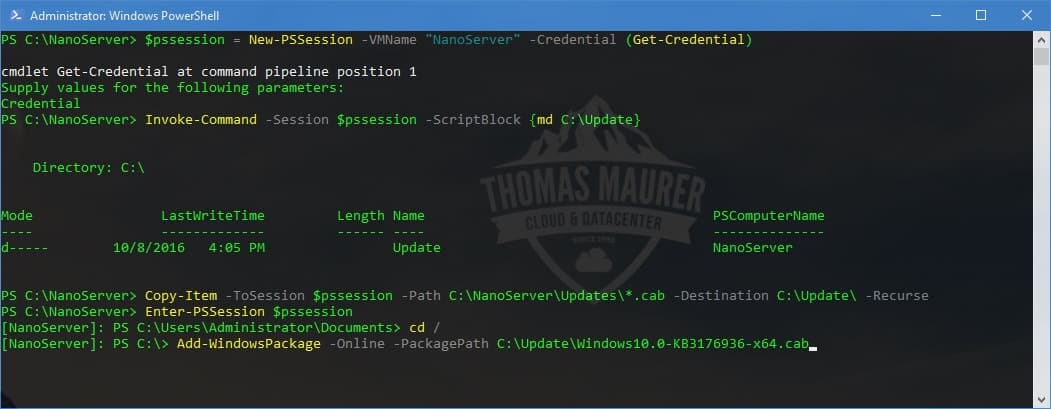
How to install Updates on Nano Server
Microsoft just released Windows Server 2016, which comes with a new deployment option called Nano Server. Nano Server is a very small...
List of Recommend Hotfixes and Updates for Hyper-V Network Virtualization (HNV)
I already made some post where I list the websites to recommended hotfixes and updates for Clusters, Hyper-V and File Server such as the...