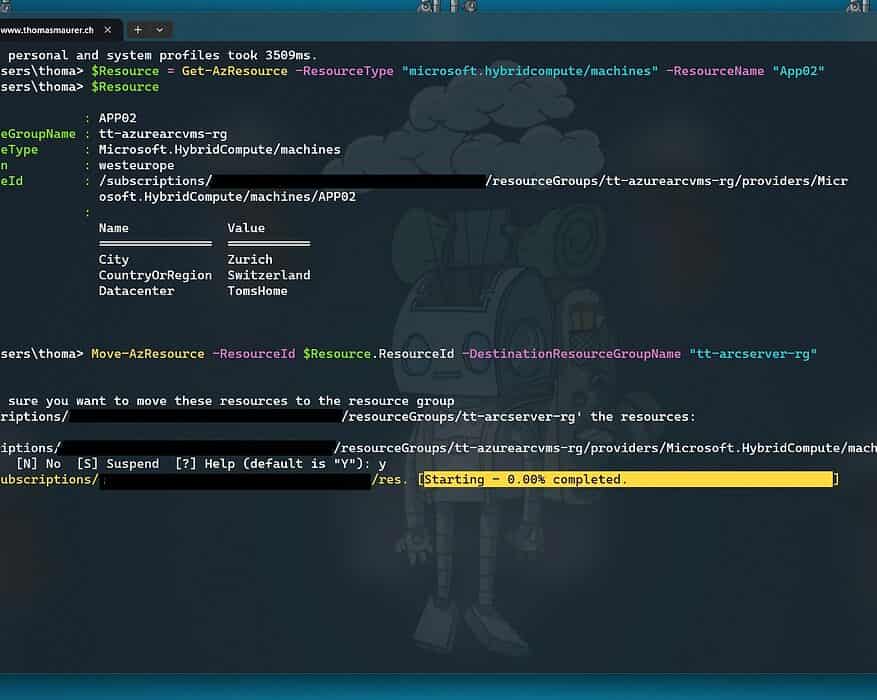
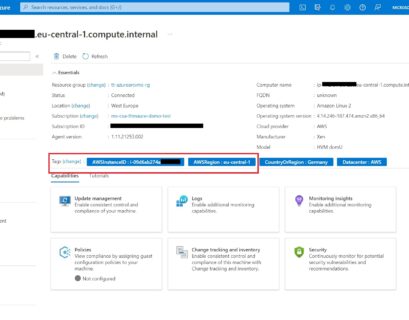
Move Azure Arc-enabled Server to a different resource group or subscription
This is just a quick post on how you can change and move your Azure Arc-enabled server to a...
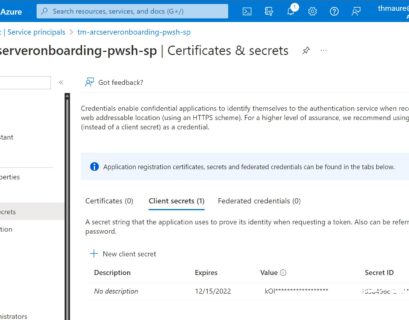
Create an Azure Arc Service Principal with longer expiration date using PowerShell
When you are onboarding at scale of Azure Arc enabled servers or Azure Arc enabled Kubernetes clusters, you want to use service principals...
Microsoft Azure Arc-enabled Servers Survey 2022
We want to learn from you about hybrid server management, so the team build a Microsoft Azure Arc-enabled servers survey 2022. Give us your...
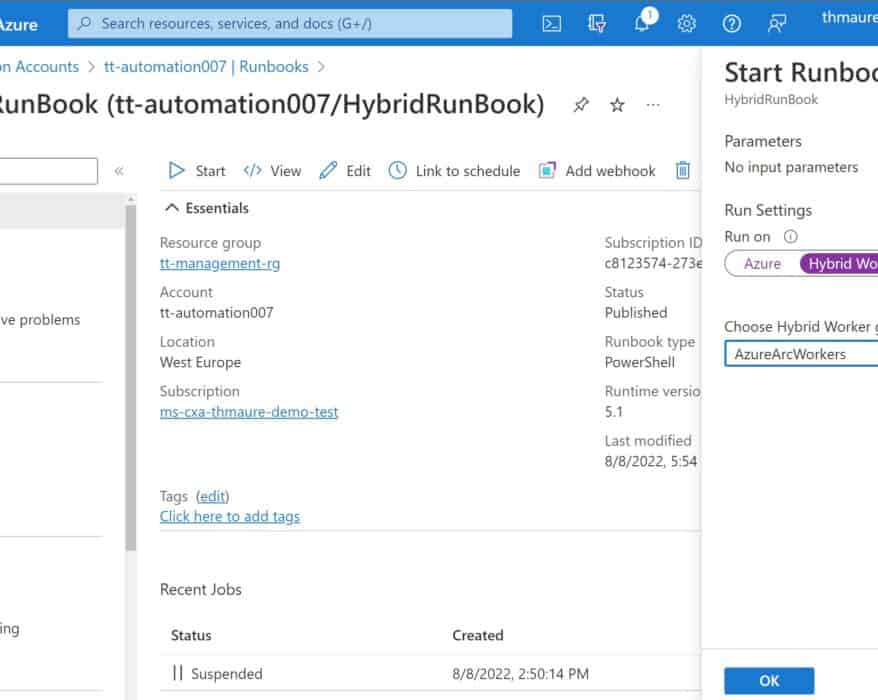
Run PowerShell Scripts with Azure Automation Hybrid Workers on-premises using Azure Arc
If you want to automate your on-premises environment Azure Arc enabled Server is a great offering...
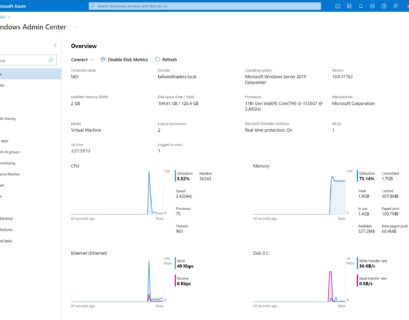
Manage Arc-enabled Windows Server with Windows Admin Center in the Azure Portal
With a new feature called Windows Admin Center in the Azure portal, you can now securely manage your Windows Server machines running as an...
Webinar: Windows Server Management, Security and Monitoring
I am happy to let you know that we are planning a Microsoft free online webinar for Windows Server Management, Security and Monitoring on...
Book: Azure Arc-Enabled Kubernetes and Servers: Extending Hyperscale Cloud Management to Your Datacenter
I know many of you want to learn more about Azure Arc and how you can leverage the Azure management...
Azure Arc Jumpstart Lightning Azure Arc-enabled servers metadata tags with Thomas Maurer
I am happy to let you know that I was able to join as a guest on Lior Kamrat video series called Azure Arc Jumpstart Lightning. In this...
Azure Webinar: Bring Cloud Value to Your Windows Server Anywhere
Windows Server and Azure are great platforms for your applications, and it gets even better when...