How to Run Custom Scripts on Azure Arc Enabled Servers
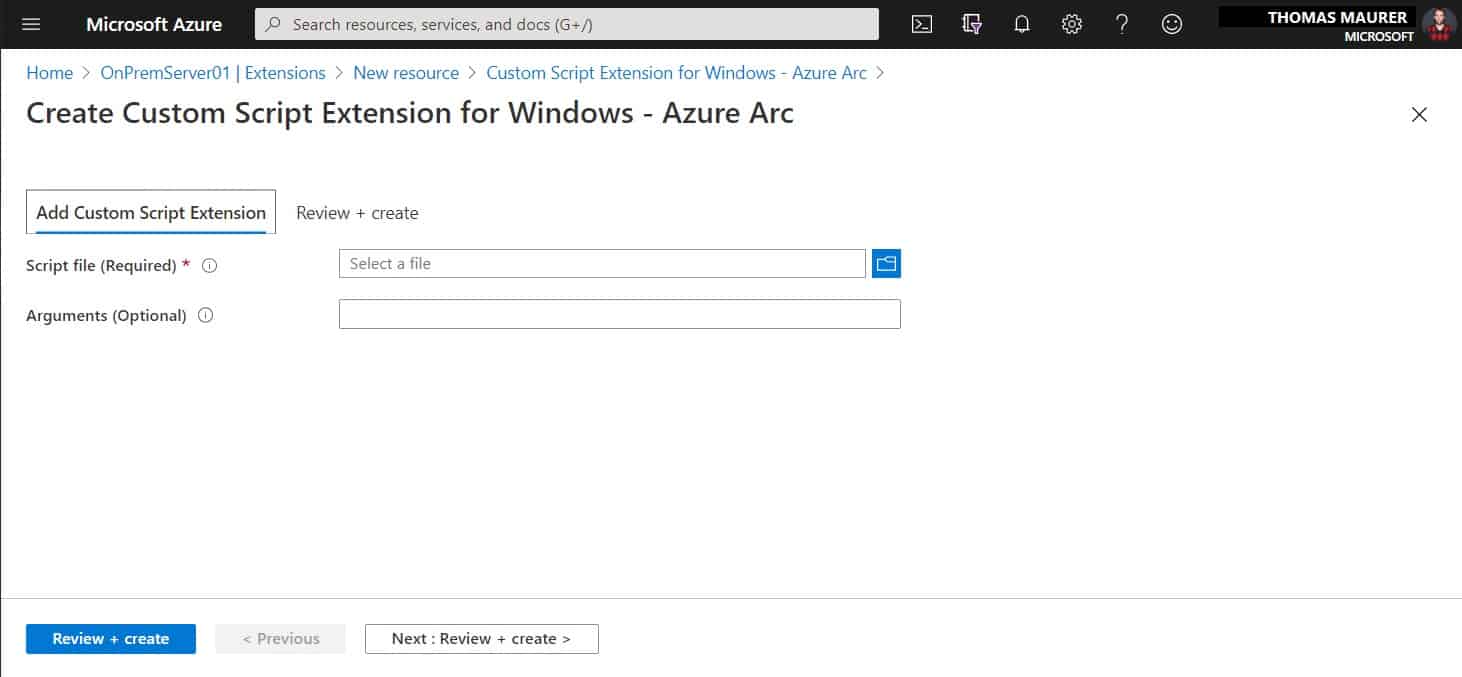
With the latest update for Azure Arc for Servers, you are now able to deploy and use extensions...
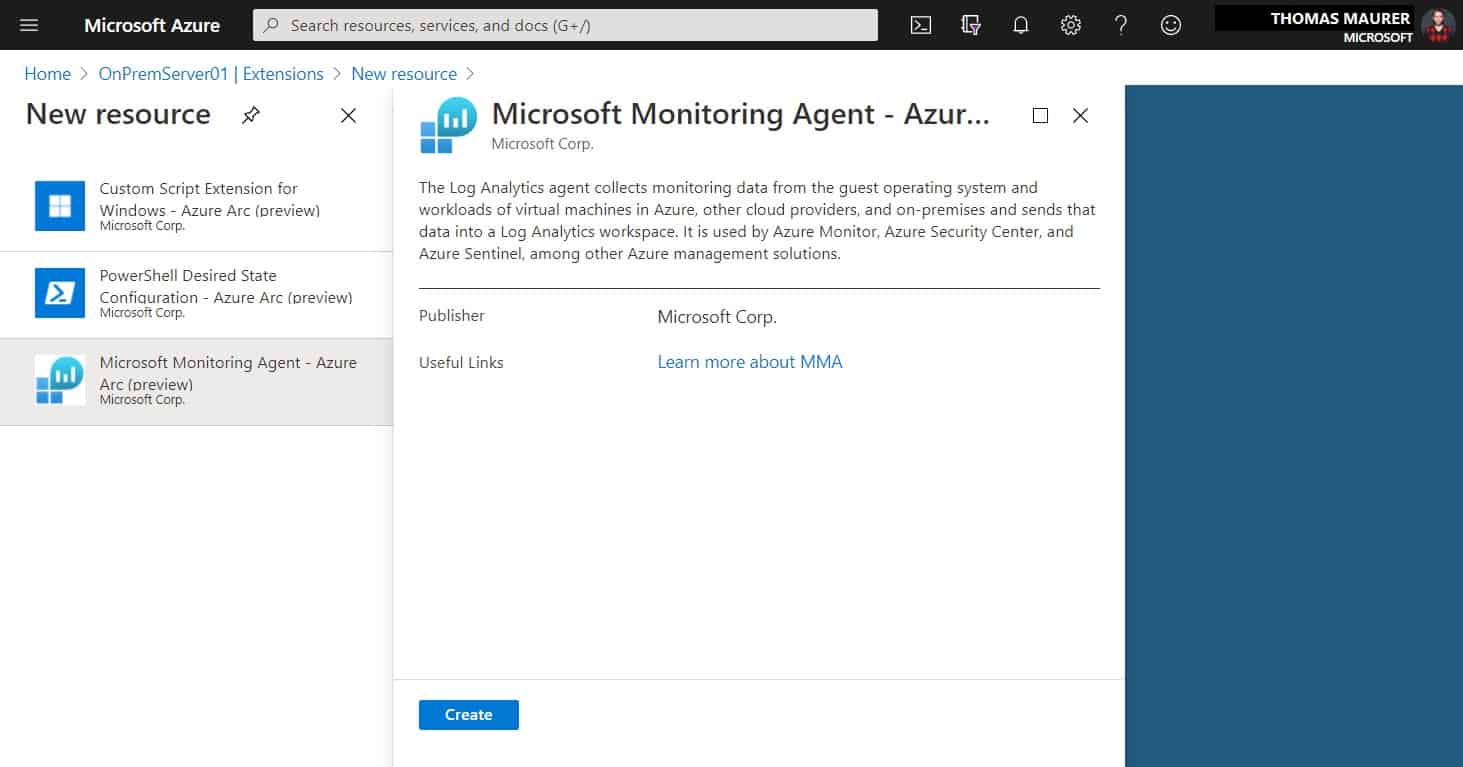
How to Add the Microsoft Monitoring Agent to Azure Arc Servers
To use some of the functionality with Azure Arc enabled servers, like Azure Update Management, Inventory, Change Tracking, Logs, and more,...
Azure Arc Enabled Servers Extension Management
Azure Arc for Server just got a couple of new features. In this blog post, we are going to have a look at the new feature on Azure Arc...
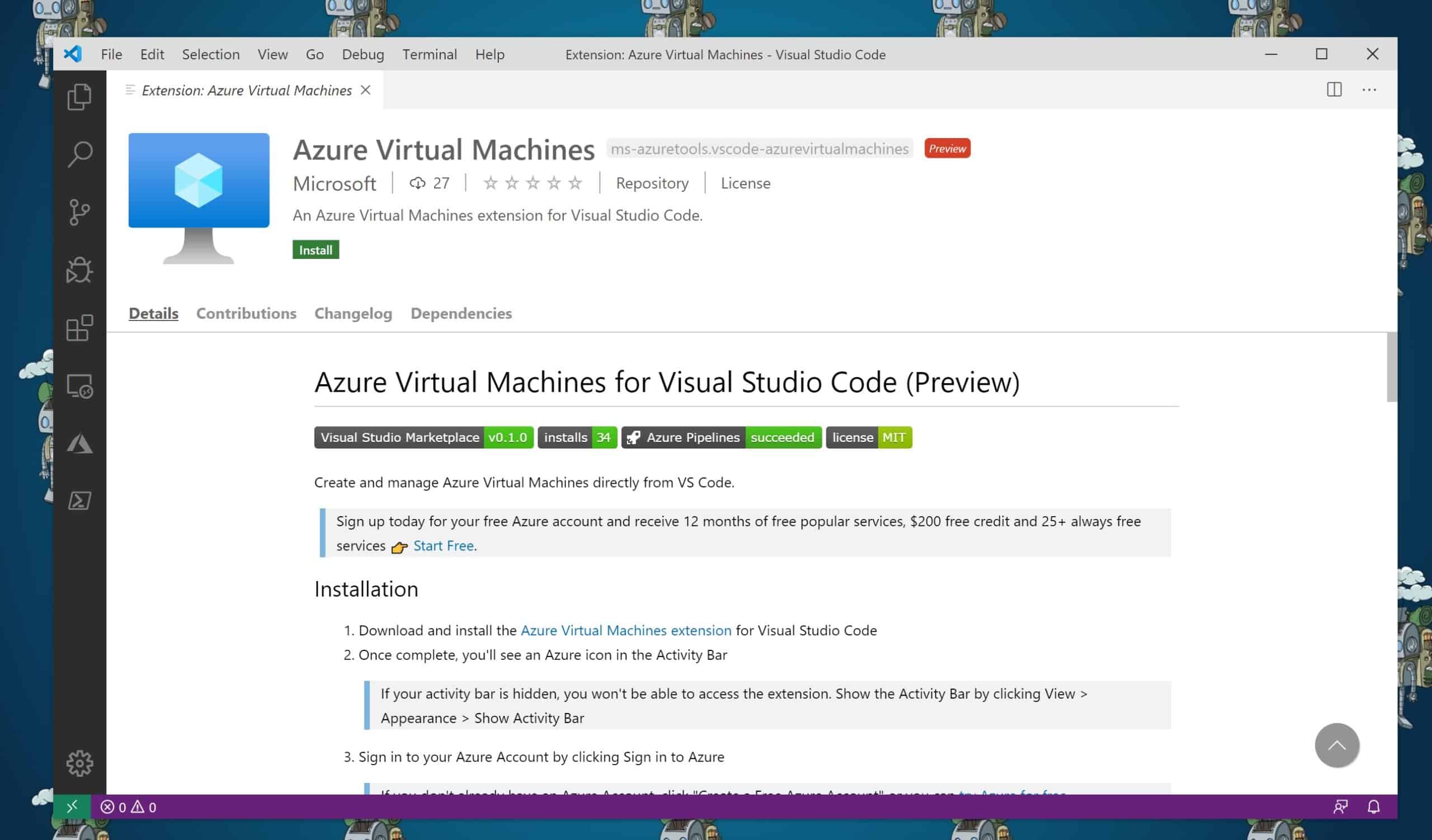
Create and Manage Azure VMs from VS Code
With the new Azure Virtual Machines (VMs) extension for Visual Studio Code (VS Code), you can now...
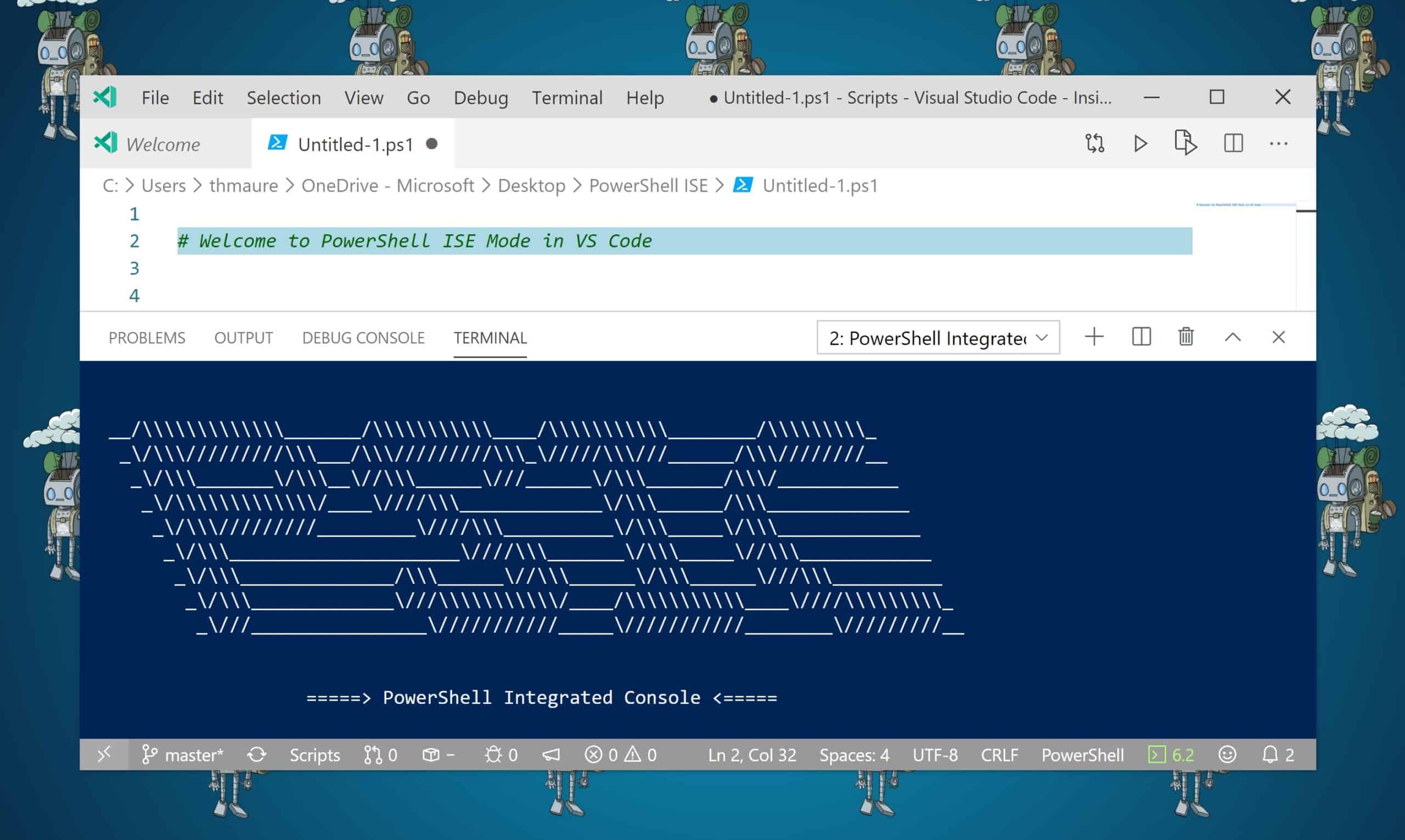
How to use PowerShell ISE Mode in Visual Studio Code
If you are writing PowerShell code, you might have realized that there weren’t really improvements to the PowerShell Integrated...
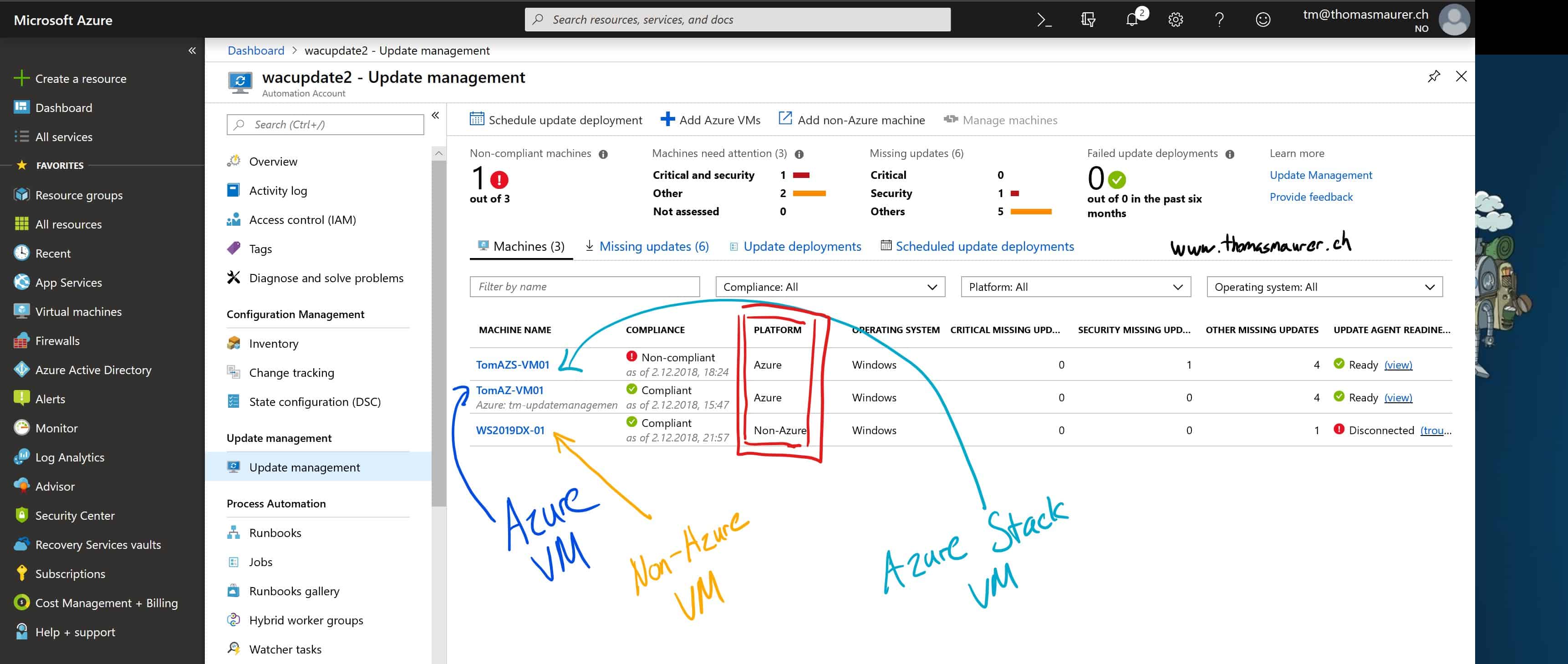
Using Azure Update Management on Azure Stack
At Microsoft Ignite 2018, Microsoft announced the integration of Azure Update and Configuration Management on Azure Stack. This is a...
PowerShell: How to export Windows Eventlogs with PowerShell
This is a little dirty Windows PowerShell script which exports or backups Windows Eventlogs. The...
PowerShell Integration Into Visual Studio
The PowerGUI Visual Studio Extension adds PowerShell IntelliSense support to Visual Studio. This is nothing new but Adam Driscoll just...