Speaking at PDCConf 2021
I am happy and honored to speak at this year’s PDC Conf 2021. PDC stands for PowerShell DevOps and Cloud and is the largest...
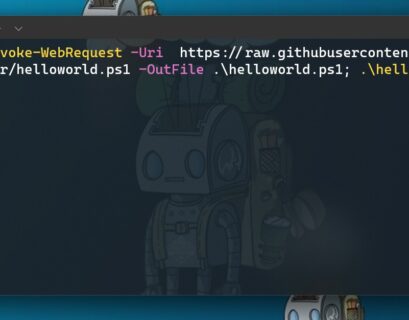
PowerShell: Download script or file from GitHub
Since a lot of people are starting to store their scripts and files in GitHub repositories, I often get the question, how can I download a...
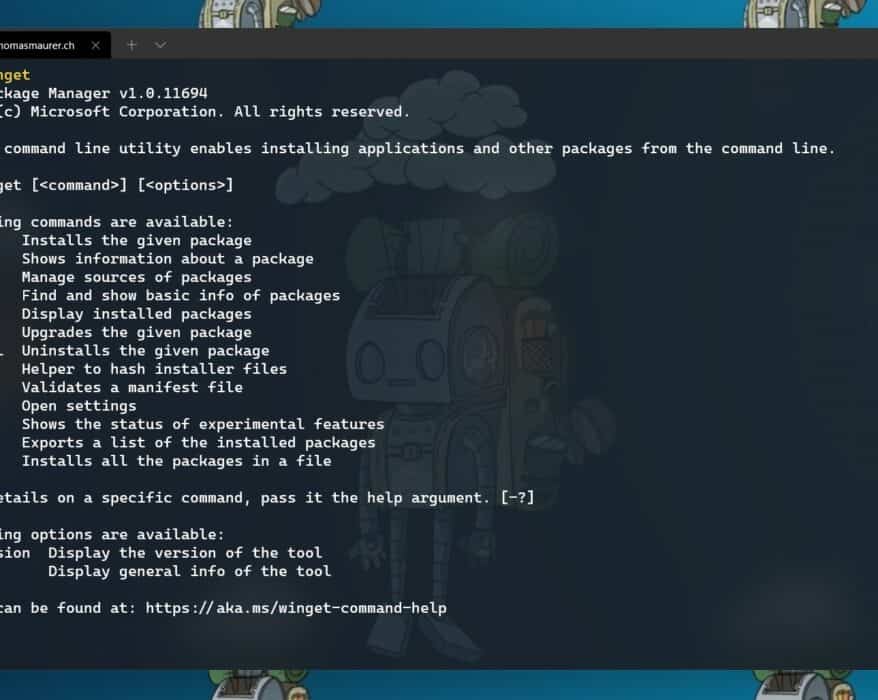
Getting started with Windows Package Manager WinGet
In this blog post I want to quickly share how you can get started with the new Windows Package...
Getting started and Learn PowerShell on Microsoft Learn!
I remember running my first commands and building my first automation using Windows PowerShell back in 2006. Since...
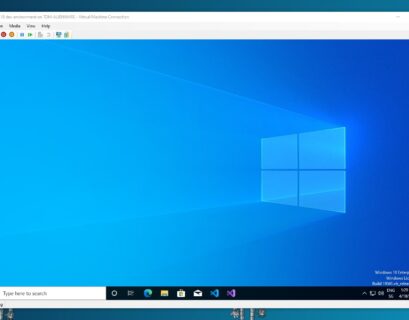
Create a Windows 10 development virtual machine
If you want to create a Windows 10 development virtual machine (VM) on your Windows 10 device, Microsoft Hyper-V with the quick start...
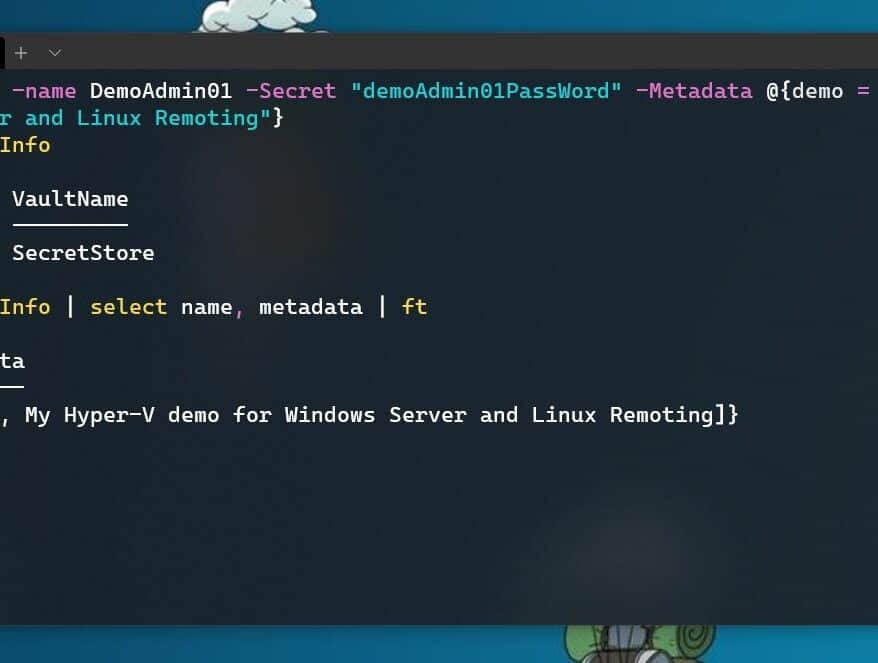
Stop typing PowerShell credentials in demos using PowerShell SecretManagement
We all sometimes create presentations with some PowerShell demos. And often, we need to use...
How to chain multiple PowerShell commands on one line
PowerShell one-liners sometimes are an easy way to achieve something quickly. There are cases where you might want to run multiple...
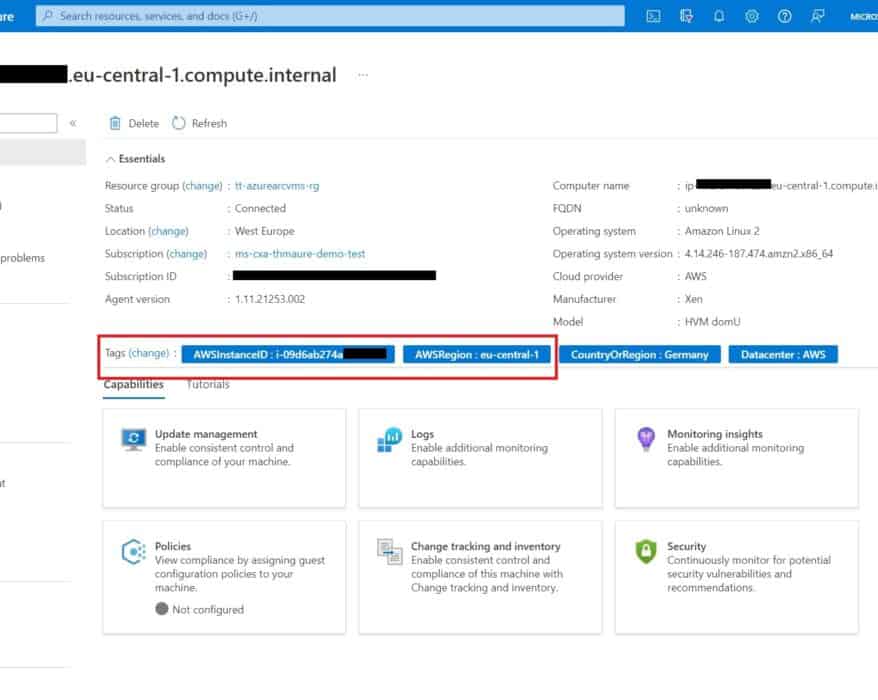
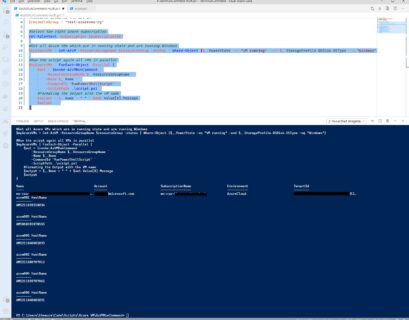
How to run scripts against multiple Azure VMs by using Run Command
I wrote a blog post on how to run scripts in your Azure VM by using Run Command, and explained how handy this feature is to manage Azure...
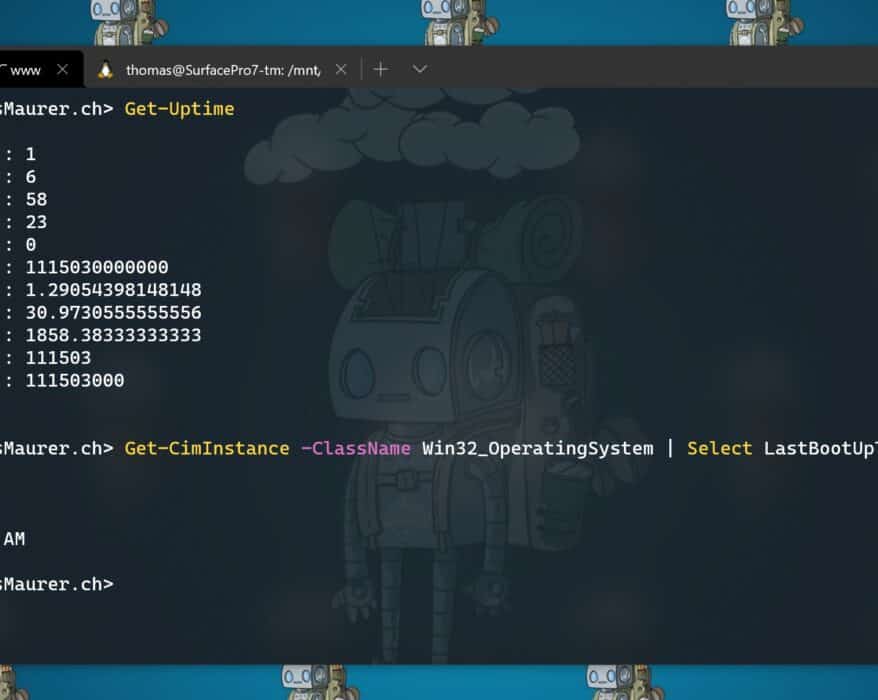
Get System Uptime with PowerShell
Sometimes you want to know how long your system is running. There are multiple ways to get the...