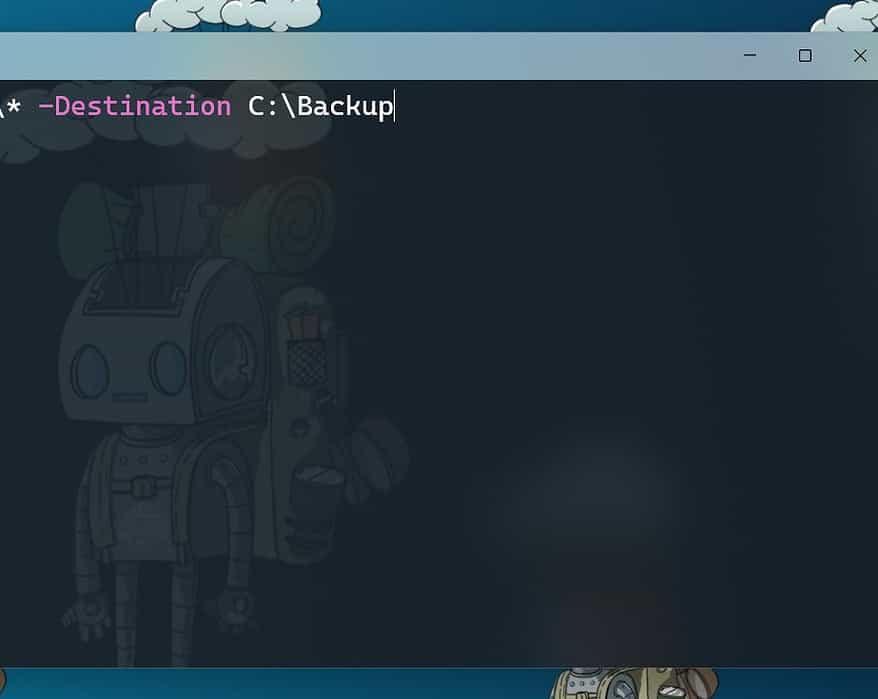
How to Move Files with PowerShell
PowerShell is a powerful scripting language that can help you automate various tasks on your...
6 Command Line (PowerShell & CLI) Tips & Tricks for Microsoft Azure you should know about!
There are many experiences and possibilities to manage your Microsoft Azure resources, one of them being the command line experience using...
PowerShell Unplugged 2022 Edition
April Edwards and I had the chance to host the PowerShell Unplugged 2022 Edition and the video is now available on YouTube! In the...
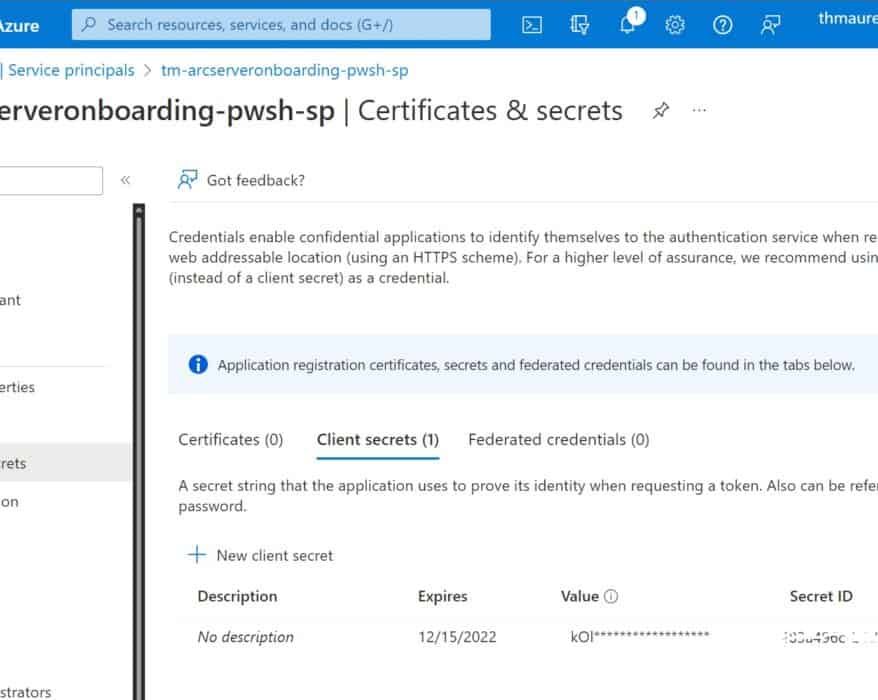
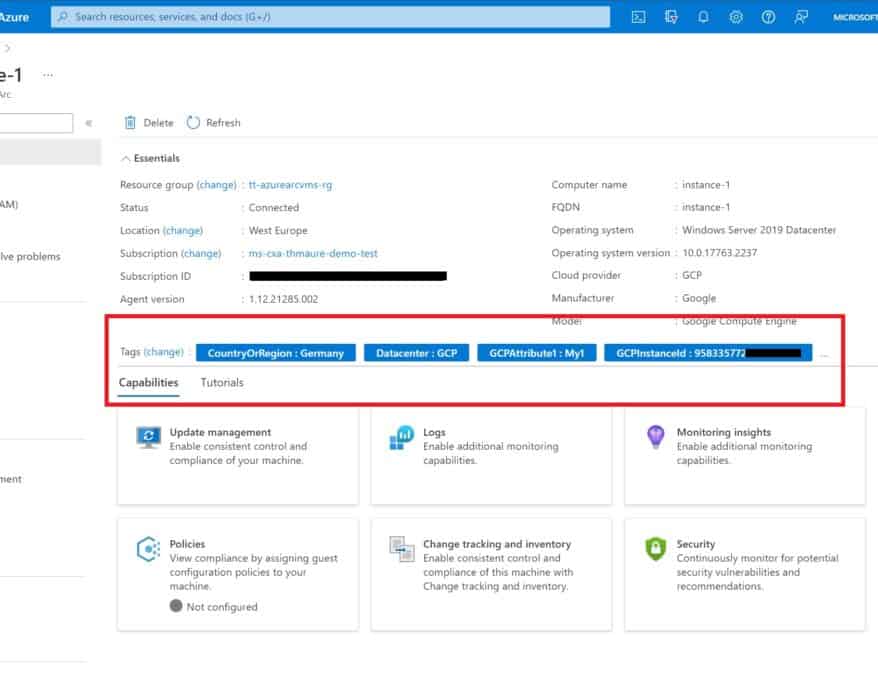
Create an Azure Arc Service Principal with longer expiration date using PowerShell
When you are onboarding at scale of Azure Arc enabled servers or Azure Arc enabled Kubernetes...
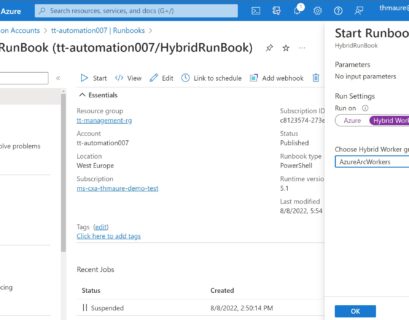
Run PowerShell Scripts with Azure Automation Hybrid Workers on-premises using Azure Arc
If you want to automate your on-premises environment Azure Arc enabled Server is a great offering to onboard Azure management services such...
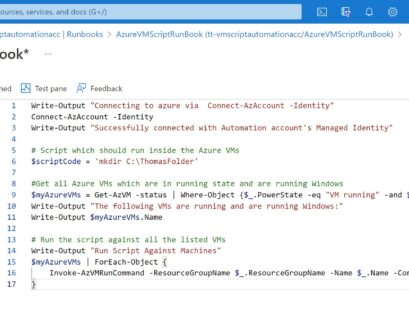
Schedule and Run PowerShell Scripts for Azure VMs using Azure Automation
A while ago I wrote a blog post on how you can run a PowerShell or Bash script against multiple Azure Virtual Machines (VMs) using Run...
Speaking at PSConf.EU 2022
I am happy and proud to let you know that I will be speaking at PowerShell Conference Europe 2022...
Windows Server 2022 Hybrid Management with Azure Arc, Automanage, Windows Admin Center, and more!
A lot of people are deploying WIndows Server on-premises, in Azure, and at the edge. I often get asked how you can implement modern Windows...
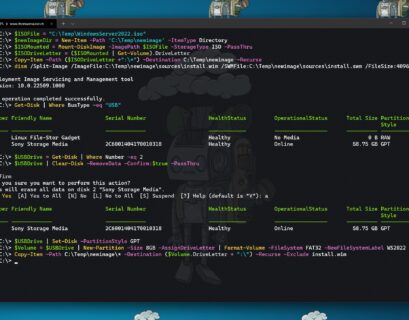
Create an USB Drive for Windows Server 2022 Installation
This blog post covers how you can create a bootable USB media drive to install Windows Server 2022 on a physical server. This...