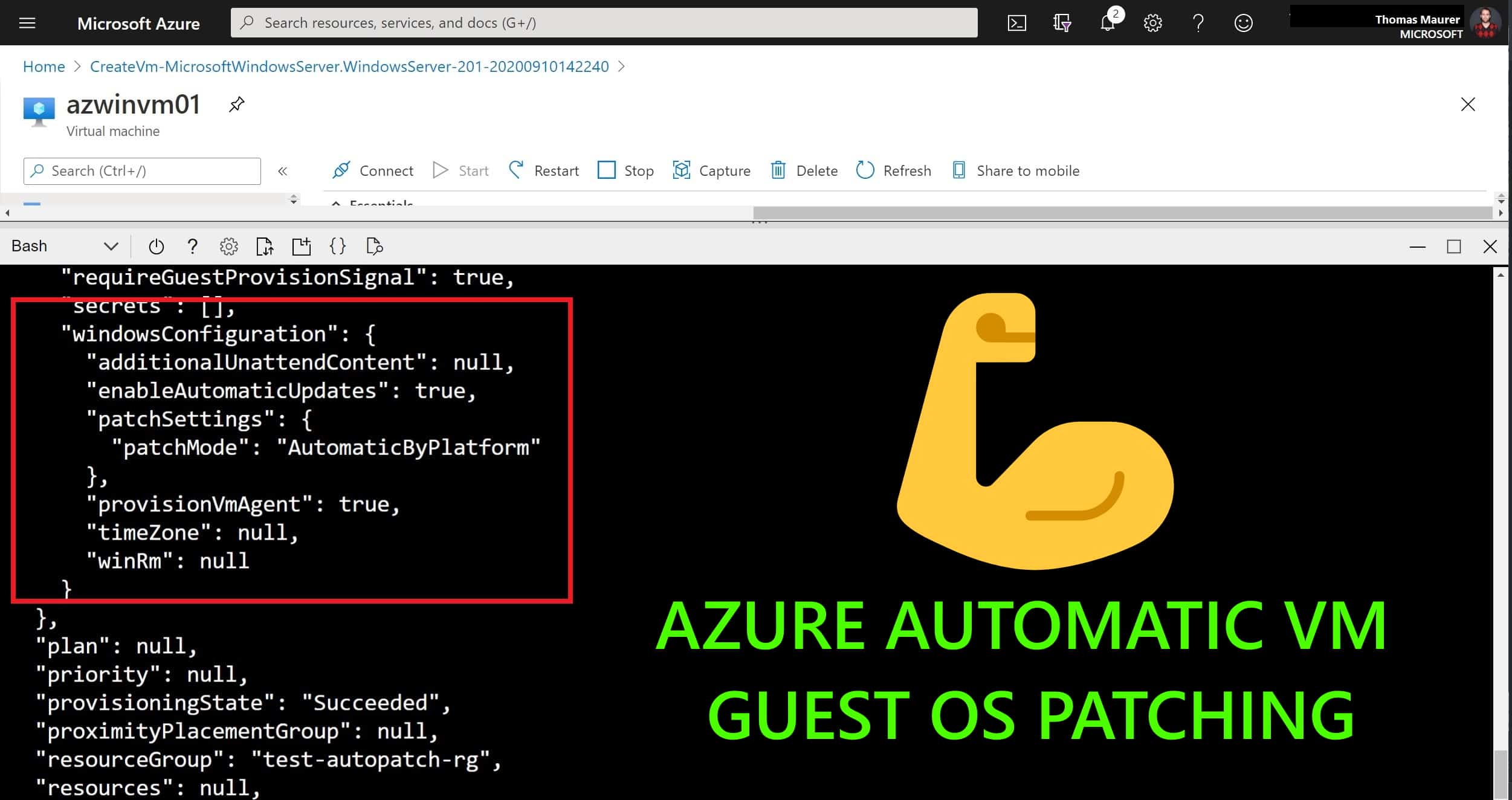
How to configure Azure Automatic VM guest OS patching
If you want to keep your Azure virtual machines (VMs) up-to-date, then there is a service called...
Updating offline VHDs via Virtual Machine Servicing Tool
Some weeks ago Microsoft announced the beta of a solution accelerator called Virtual Machine Servicing Tool 2012. The VMST 2012 allows you...