How to Move Files with PowerShell
PowerShell is a powerful scripting language that can help you automate various tasks on your...
Use the Azure Arc Managed Identity with Azure PowerShell
In this blog post we are going to have a look at how you can use the Azure Arc provided Azure Active Directory (Azure AD) managed identity...
Microsoft Azure Arc-enabled Servers Survey 2022
We want to learn from you about hybrid server management, so the team build a Microsoft Azure Arc-enabled servers survey 2022. Give us your...
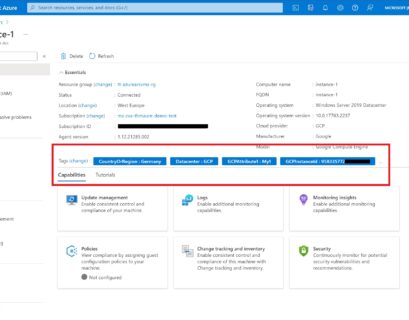
Azure Arc Jumpstart Lightning Azure Arc-enabled servers metadata tags with Thomas Maurer
I am happy to let you know that I was able to join as a guest on Lior Kamrat video series called...
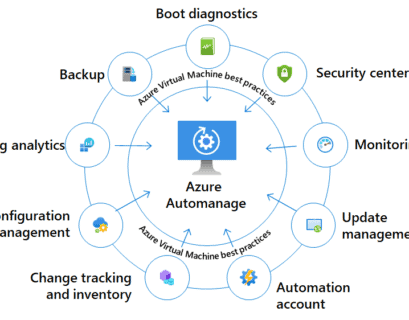
Azure Automanage for Arc enabled servers
At the last Azure Hybrid and Multicloud digital event, Microsoft not just announced the general availability of Azure SQL enabled by...
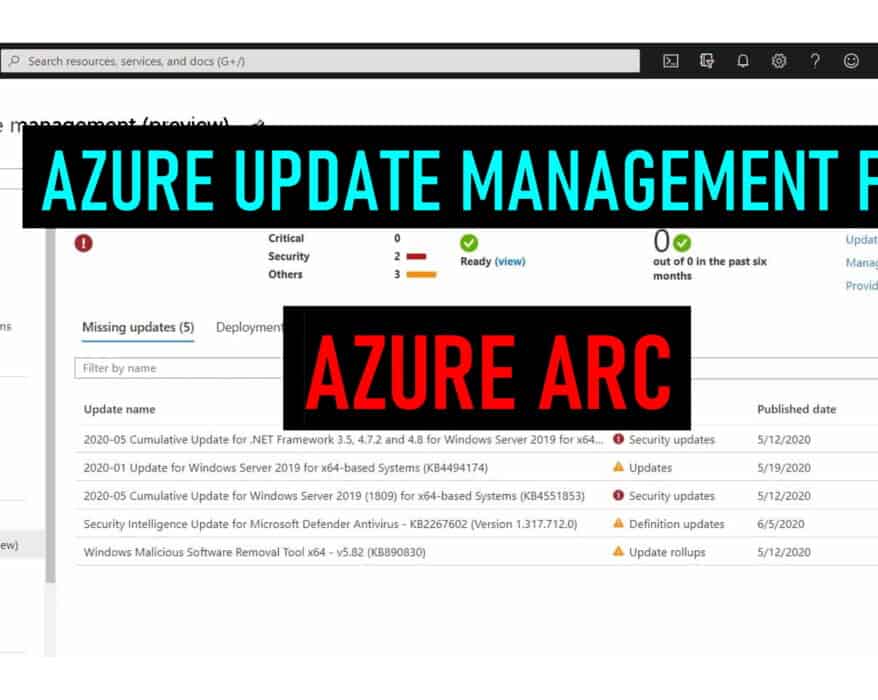
Manage updates of servers using Microsoft Azure Arc
The Azure Update Management solution is part of Azure Automation. And with Azure Update Management...
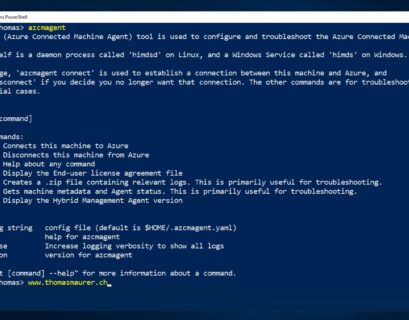
The Azure Arc Connected Machine Agent (Azcmagent)
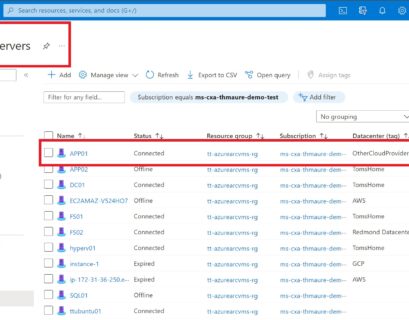
Azure Arc enabled servers allows you to add on-premises servers or servers running on another cloud provider. The onboarding is done by...
Getting started and Learn PowerShell on Microsoft Learn!
I remember running my first commands and building my first automation using Windows PowerShell back in 2006. Since...
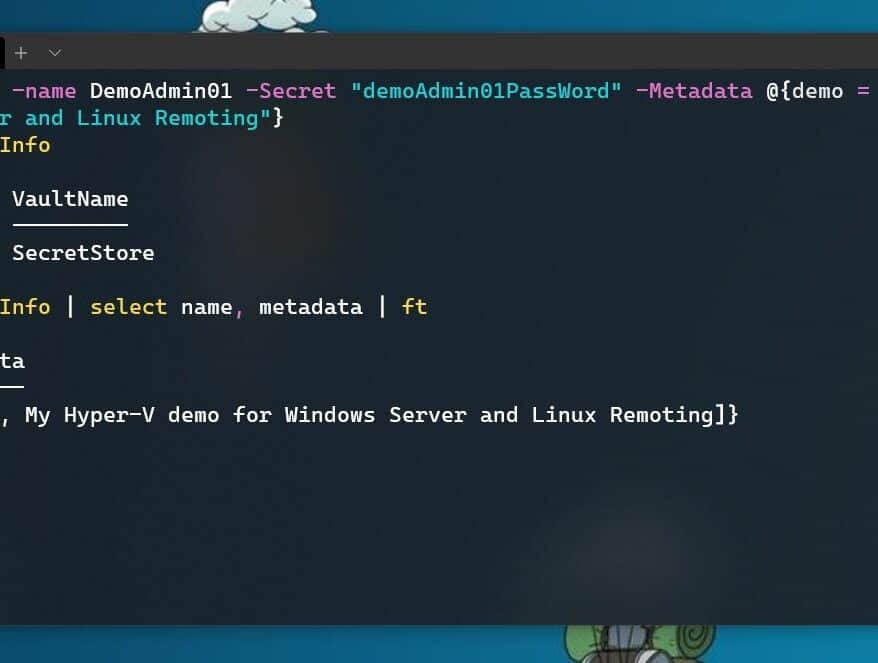
Stop typing PowerShell credentials in demos using PowerShell SecretManagement
We all sometimes create presentations with some PowerShell demos. And often, we need to use...