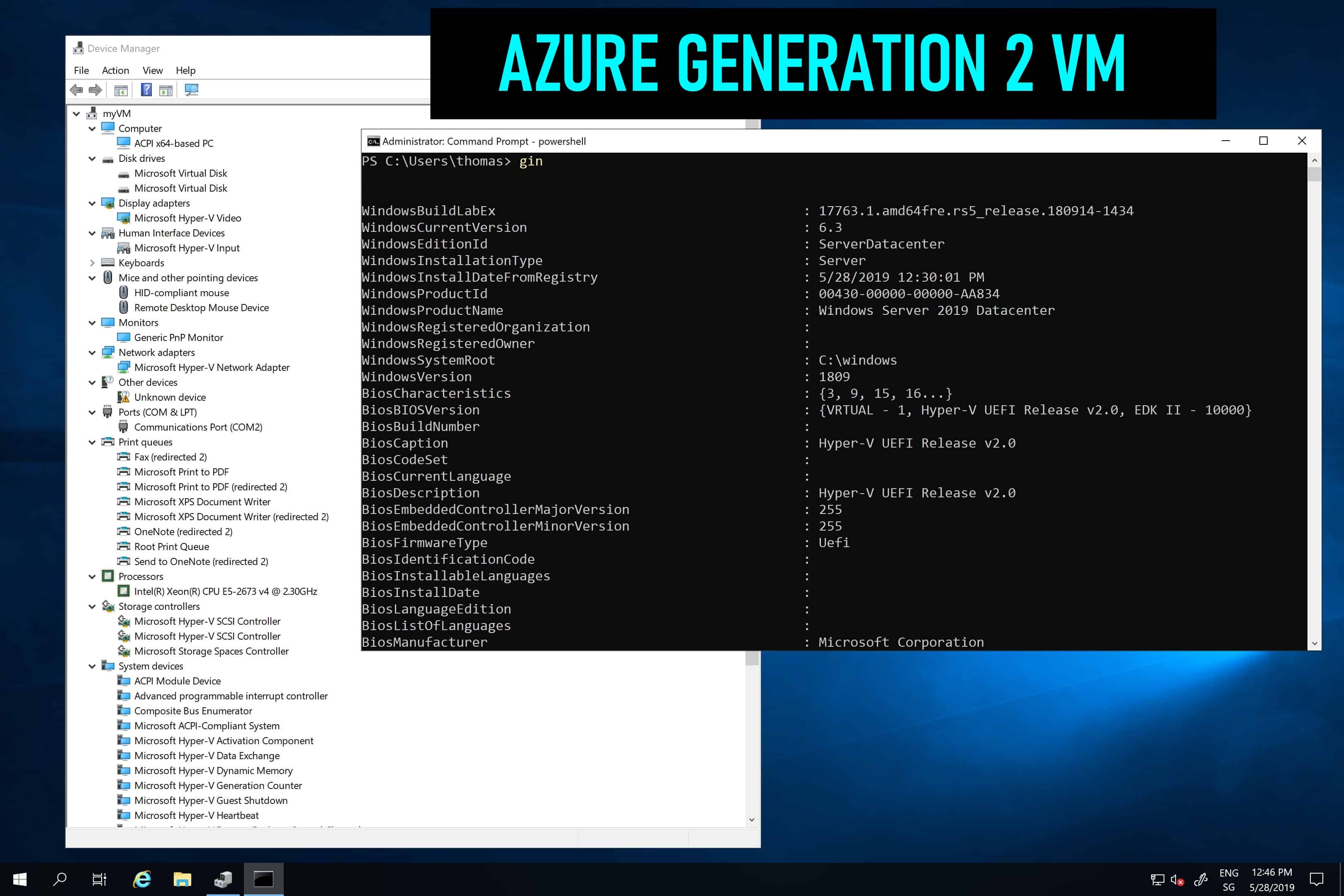
Generation 2 VM support on Azure – and why should I care?
A couple of days ago Microsoft announced the public preview of Generation 2 virtual machines on...
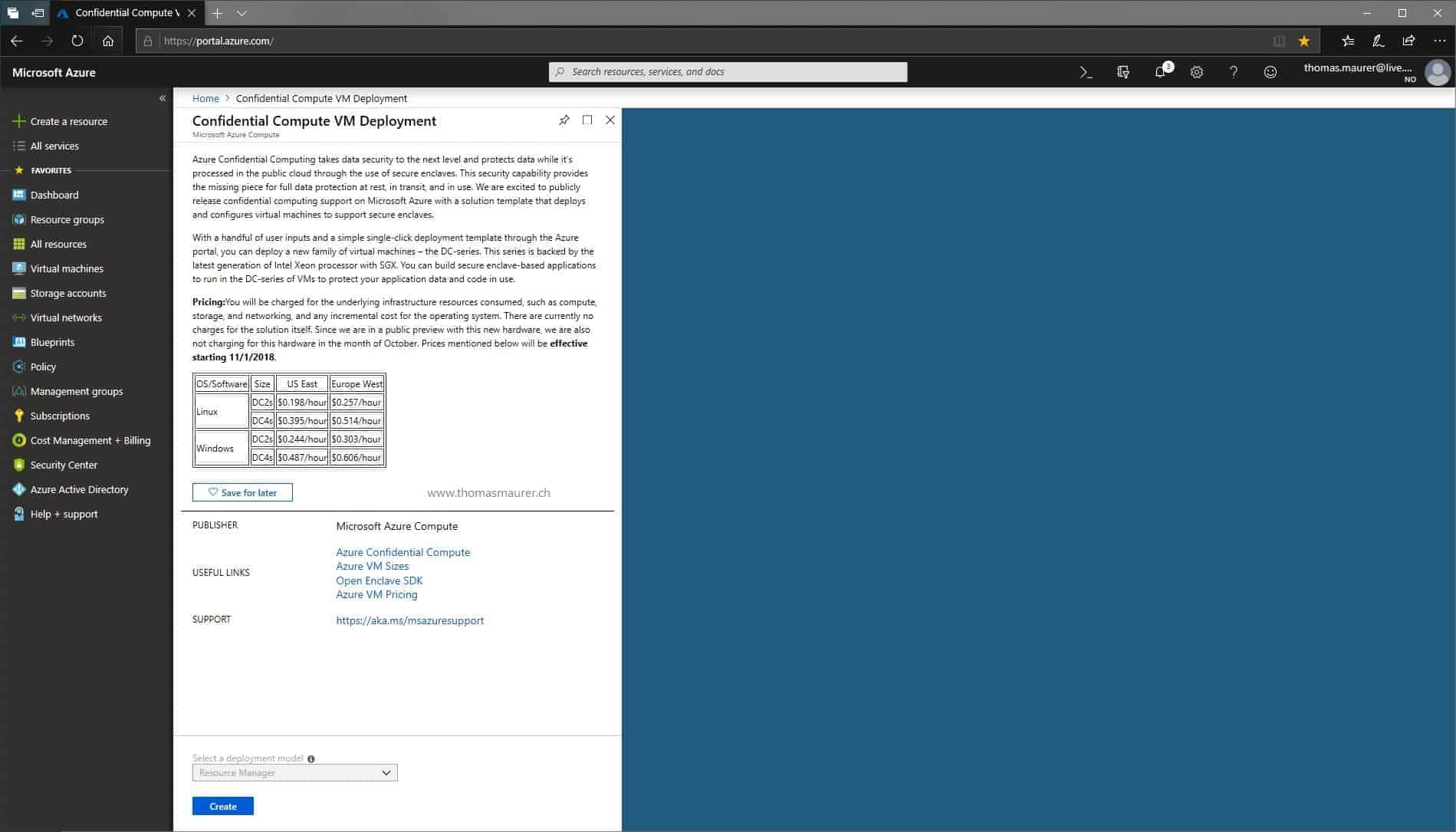
Protect Workloads with Azure Confidential Computing
A year ago Microsoft announced that they were working on a new technology in Azure to protect and encrypt data in use, called Azure...