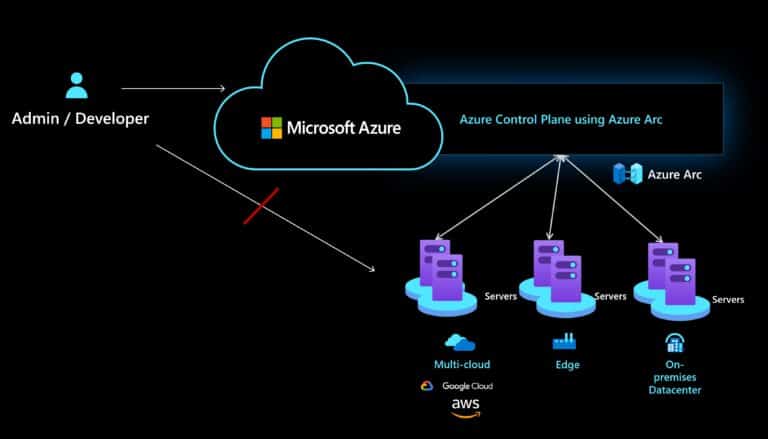
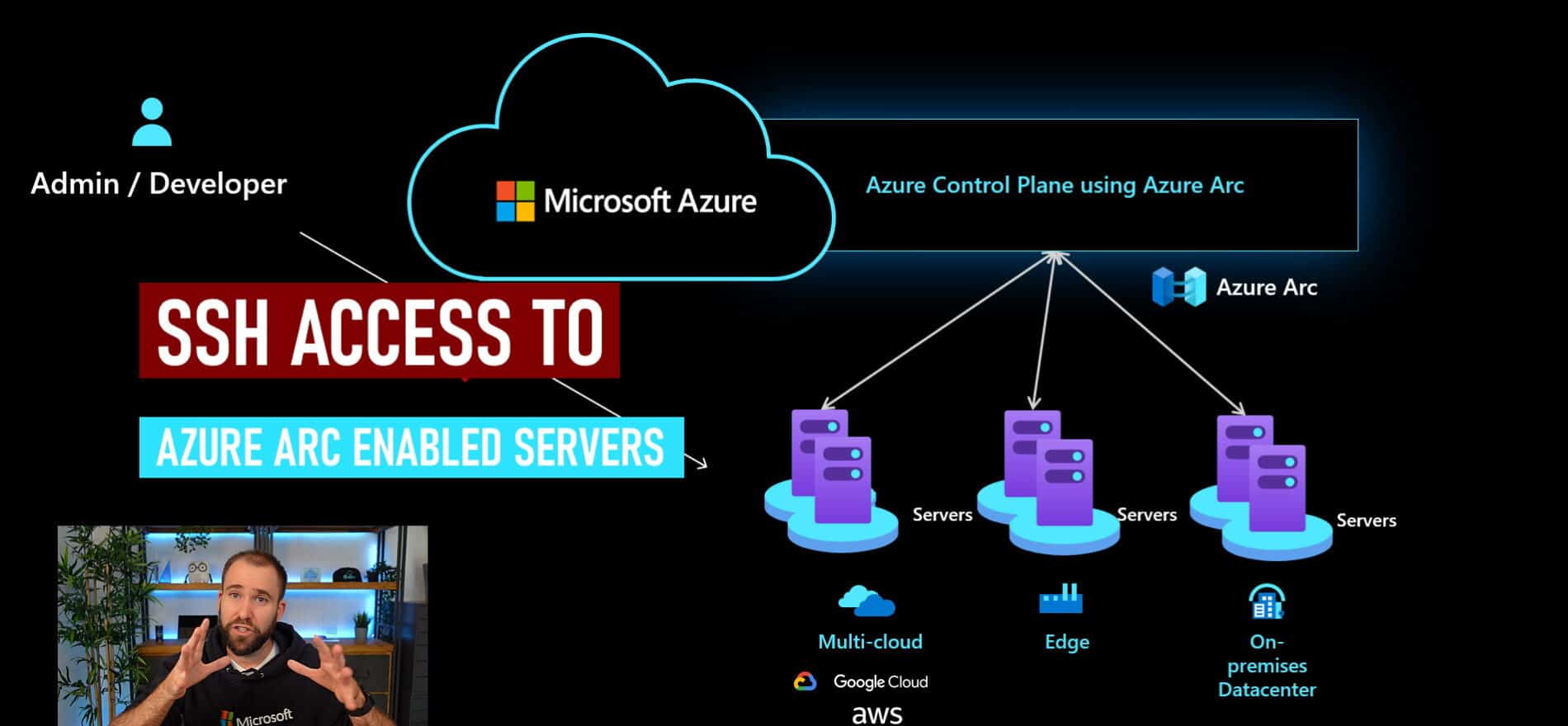
With Azure Arc, you can remotely manage your Linux and Windows Servers using the Azure control plane and management services, such as Azure Policy, Update Management, Security Center, Azure Monitor, and many more. This allows you to manage servers running on-premises, at the edge, or in mutlicloud environments at scale. However, in some cases, you will need to have direct access to your servers for troubleshooting for example using an SSH connection. In many of these hybrid and mutlicloud environments, direct network connectivity can be a challenge, that is why you now can get SSH access to your Linux and Windows Servers running anywhere using Azure Arc enabled servers.
Imagine a scenario where you as an IT Pro or developer need to access a server remotely using SSH, to troubleshoot a system or install or configure an application or the server. However, you might don’t have direct network access to the server since you are working remotely or you don’t have a VPN set up. Azure Arc enabled server now allows you to use the Azure CLI SSH extension to connect to the Azure control plane and from there to securely connect to the Azure Arc enabled server using the Azure Connected Machine Agent without opening additional ports or firewall configurations. In addition, to enable the connection you can also use Azure AD for role-based access control.
SSH access to Azure Arc-enabled servers offers the following benefits:
- Create interactive and automated SSH connections to Arc-enabled Servers
- Securely access hybrid servers without any additional ports or a public IP address
- Access to Windows and Linux machines
- Leverage different authentication options: AAD login based on RBAC roles (Linux only), Key-based authentication, and username & password authentication
- Connect as a local user or as an Azure user
- Connect with existing SSH clients using a config file
- Connect to servers using Azure Cloud Shell
- Leverage existing workflows & scripts for Azure IaaS Virtual Machines on Arc-enabled Servers
You can read more on the official Tech Community blog.
How to set up SSH access for Azure Arc enabled servers
Prerequisites
Setting up this new feature (which is currently in preview) is very simple. If you haven’t already connected your Linux or Windows Server to Azure using Azure Arc, you need to first install the Azure Arc agent. You can find a simple blog post and video on how to install the Azure Arc agent here. If you are already using Azure Arc, make sure your servers hybrid agent version is “1.13.21320.014” or higher. You can check this by running the following command:
azcmagent show
Importantly your server needs to have SSH configured and working, otherwise, Azure Arc cannot use it. If you want to set up SSH on a Windows Server, check out Microsoft Docs or follow my blog.
Supported Operating Systems
- Windows: Windows 7+ and Windows Server 2012+
- Linux: Supported Linux distros and versions can be found on the Azure Documentation page.
After you have connected your server, and it shows up in the Azure portal. You now need to add the port to your server, for that you can run the following command on your server.
Enable the SSH capability on the Arc-enabled servers
Run the following in an elevated terminal on the Arc-enabled server:
azcmagent config set incomingconnections.ports 22<,other open ports,…>
Note: If you would like to use a custom port for the SSH connection, change the above command to use the custom port.
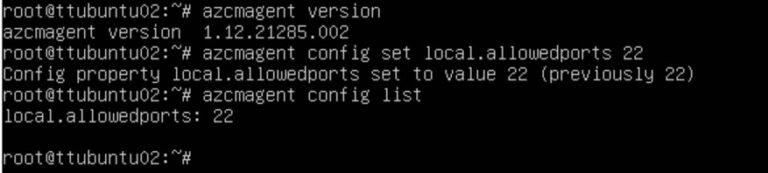
To view existing ports
azcmagent config list
Create default connectivity endpoint
Run the following commands for each of your Azure Arc enabled servers, replace subscription, resource group, and arc enabled server name.
az rest --method put --uri https://management.azure.com/subscriptions/<subscription>/resourceGroups/<resourcegroup>/providers/Microsoft.HybridCompute/machines/<arc enabled server name>/providers/Microsoft.HybridConnectivity/endpoints/default?api-version=2021-10-06-preview --body '{\"properties\": {\"type\": \"default\"}}'
az rest --method get --uri https://management.azure.com/subscriptions/<subscription>/resourceGroups/<resourcegroup>/providers/Microsoft.HybridCompute/machines/<arc enabled server name>/providers/Microsoft.HybridConnectivity/endpoints/default?api-version=2021-10-06-previewInstall and update the Azure CLI extension
On the client, you will need to add or update the Azure CLI SSH extension.
Add Az CLI SSH extension
az extension add --name ssh
Update Az CLI SSH extension
az extension update --name ssh
Optional: Enable Azure AD login on Linux
You can also use Azure AD to log in to the Linux server. For that, you can simply run the following command on your Linux machine
sudo apt-get install aadsshlogin
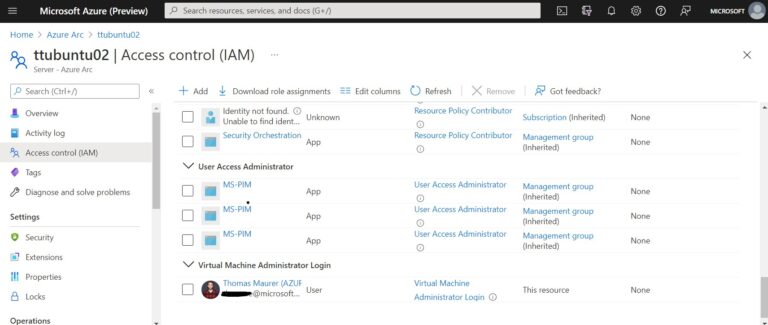
To enable the Azure AD user or group to log in you need to follow the “Configure role assignments for the VM” instructions on the AAD Login for Linux documentation.
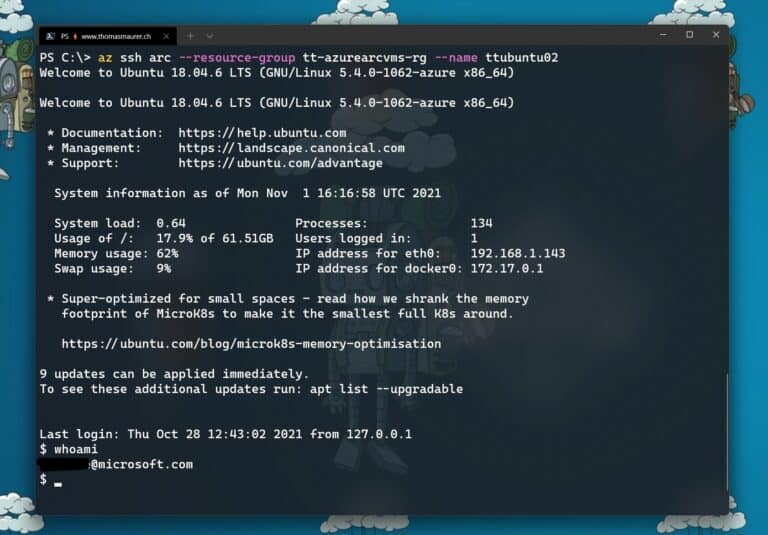
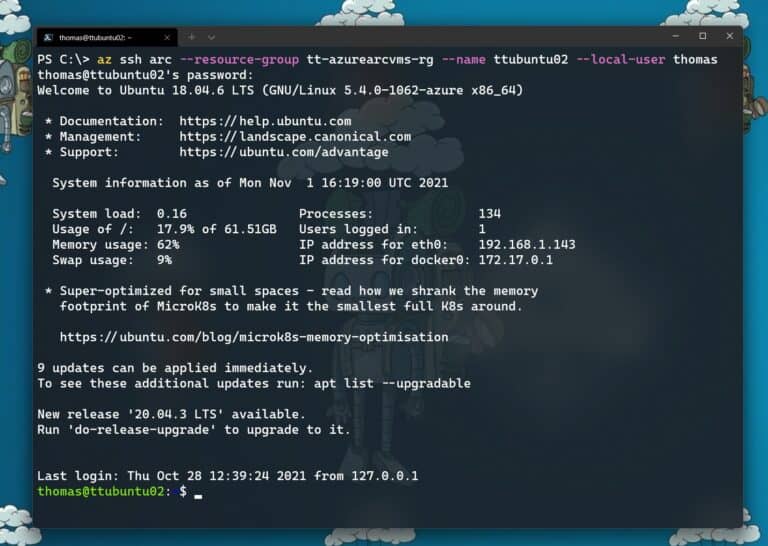
SSH connect to Azure Arc enabled servers using the Azure CLI
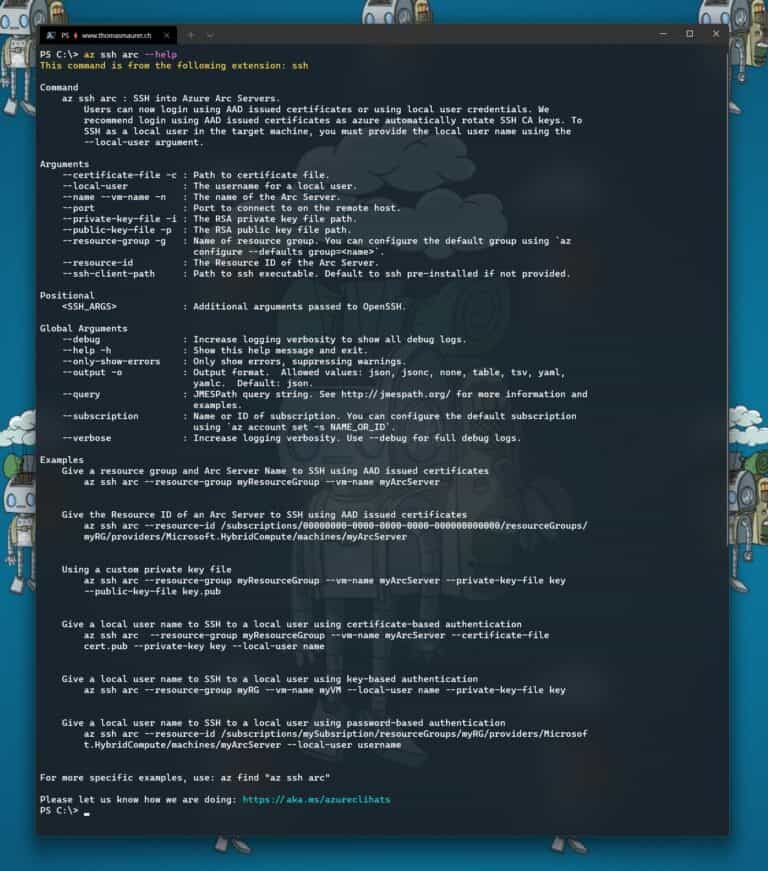
Now after you have done that setup and have the right version of the Azure CLI SSH extension, you can now SSH connect to your Azure Arc enable server. Now you have multiple options, depending on how you want to connect. You can learn more by running: az ssh arc --help.
Give a resource group and Arc Server Name to SSH using AAD issued certificates
az ssh arc --resource-group myResourceGroup --vm-name myArcServer
Give the Resource ID of an Arc Server to SSH using AAD issued certificates
az ssh arc --resource-id /subscriptions/00000000-0000-0000-0000-000000000000/resourceGroups/myRG/providers/Microsoft.HybridCompute/machines/myArcServer
Using a custom private key file
az ssh arc --resource-group myResourceGroup --vm-name myArcServer --private-key-file key --public-key-file key.pub
Give a local user name to SSH to a local user using certificate-based authentication
az ssh arc --resource-group myResourceGroup --vm-name myArcServer --certificate-file cert.pub --private-key key --local-user name
Give a local user name to SSH to a local user using key-based authentication
az ssh arc --resource-group myRG --vm-name myVM --local-user name --private-key-file key
Give a local user name to SSH to a local user using password-based authentication
az ssh arc --resource-id /subscriptions/mySubsription/resourceGroups/myRG/providers/Microsoft.HybridCompute/machines/myArcServer --local-user username
If you want to learn more check out Microsoft Docs and the Azure CLI help command.
Conclusion
For more information check out the documentation page here on Microsoft Docs. I hope this provides you with a great overview of how you can manage and SSH access your Linux and Windows Servers anywhere using Azure Arc. If you have any questions, feel free to leave a comment.
Last modified: April 19, 2022







Port forwarding ..
az ssh arc –resource-group myResourceGroup –vm-name myArcServer “-L 3333:x.x.x.x:3389”
Great stuff Thomas, thank you for detailed post and very clearfull video!
Just sharing a couple of questions:
1.- You logged as non-privileged user, what if login with Admnistrator role? It makes you root directly o anything need to be setup first?
2.- As non-privileges users from AAD, is it possible to assign permissions them into local folders?
Very appreciated!
When I try to connect using AAD I get error Permission denied (publickey)
Any idea ?