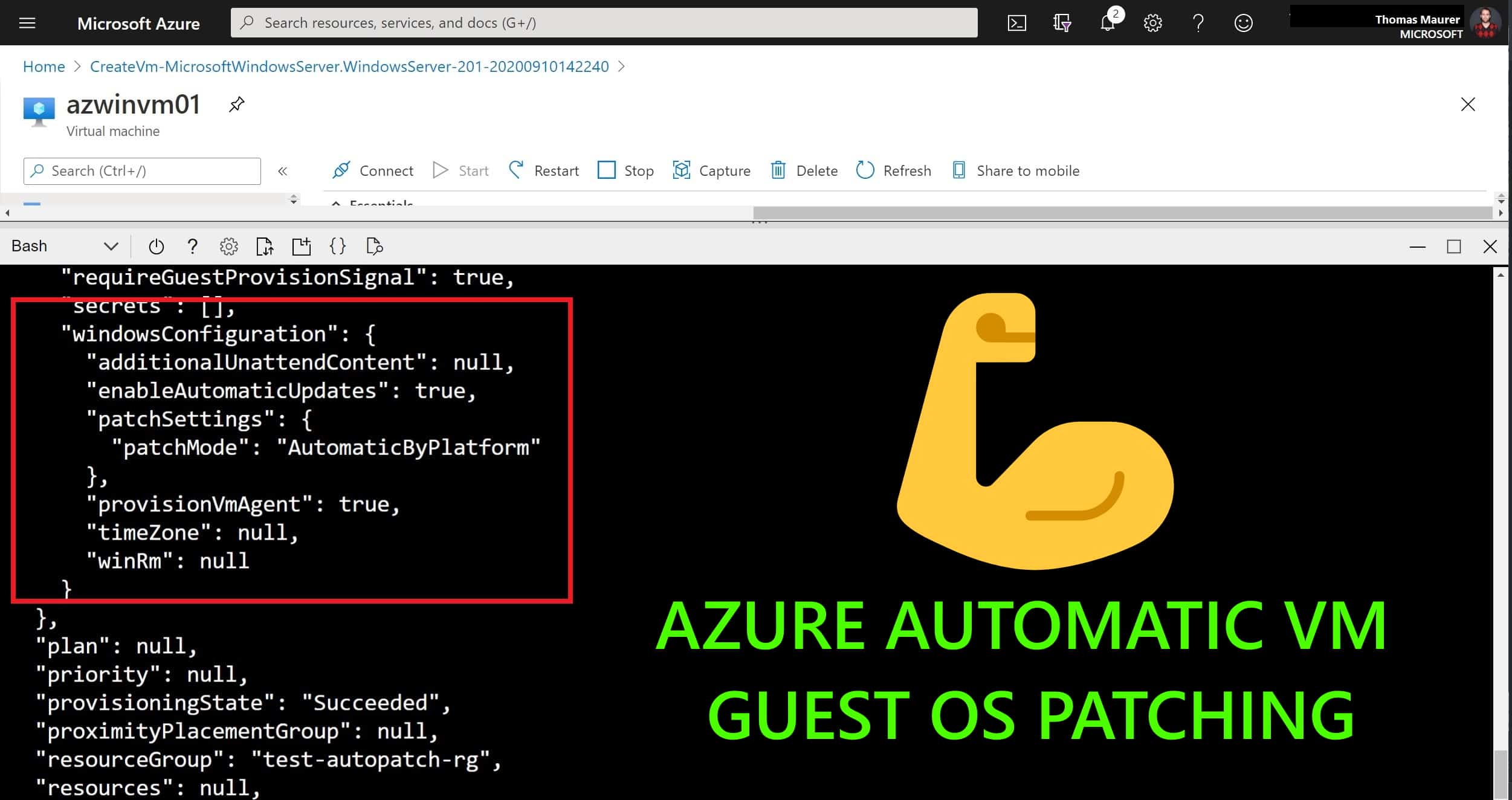
How to configure Azure Automatic VM guest OS patching
If you want to keep your Azure virtual machines (VMs) up-to-date, then there is a service called...
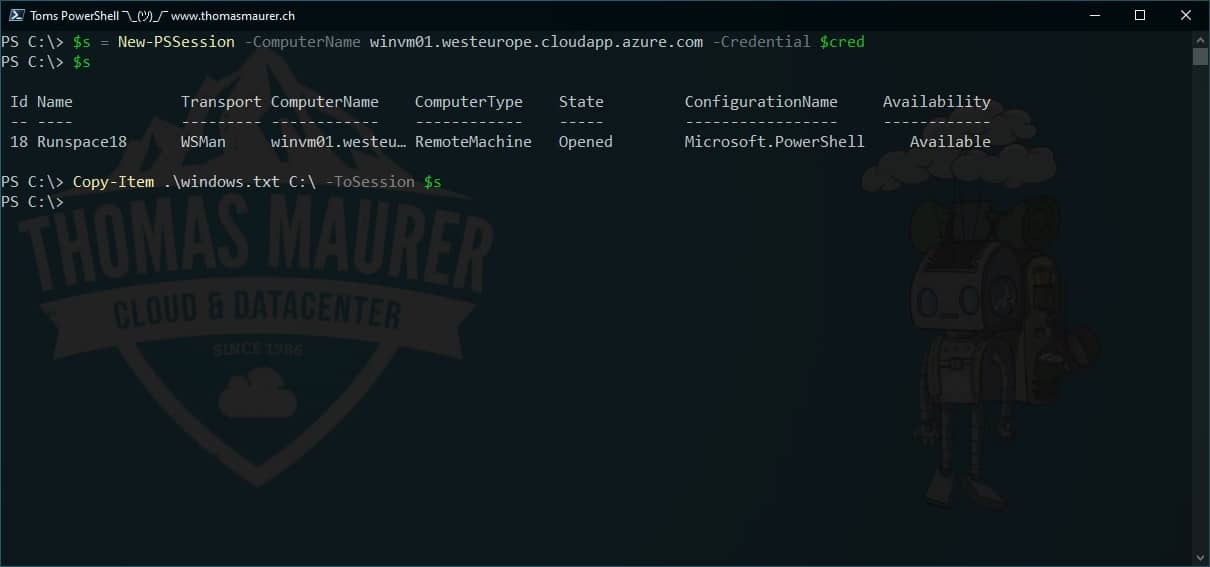
Copy Files to Azure VM using PowerShell Remoting
There are a couple of different cases you want to copy files to Azure virtual machines. To copy files to Azure VM, you can use PowerShell...