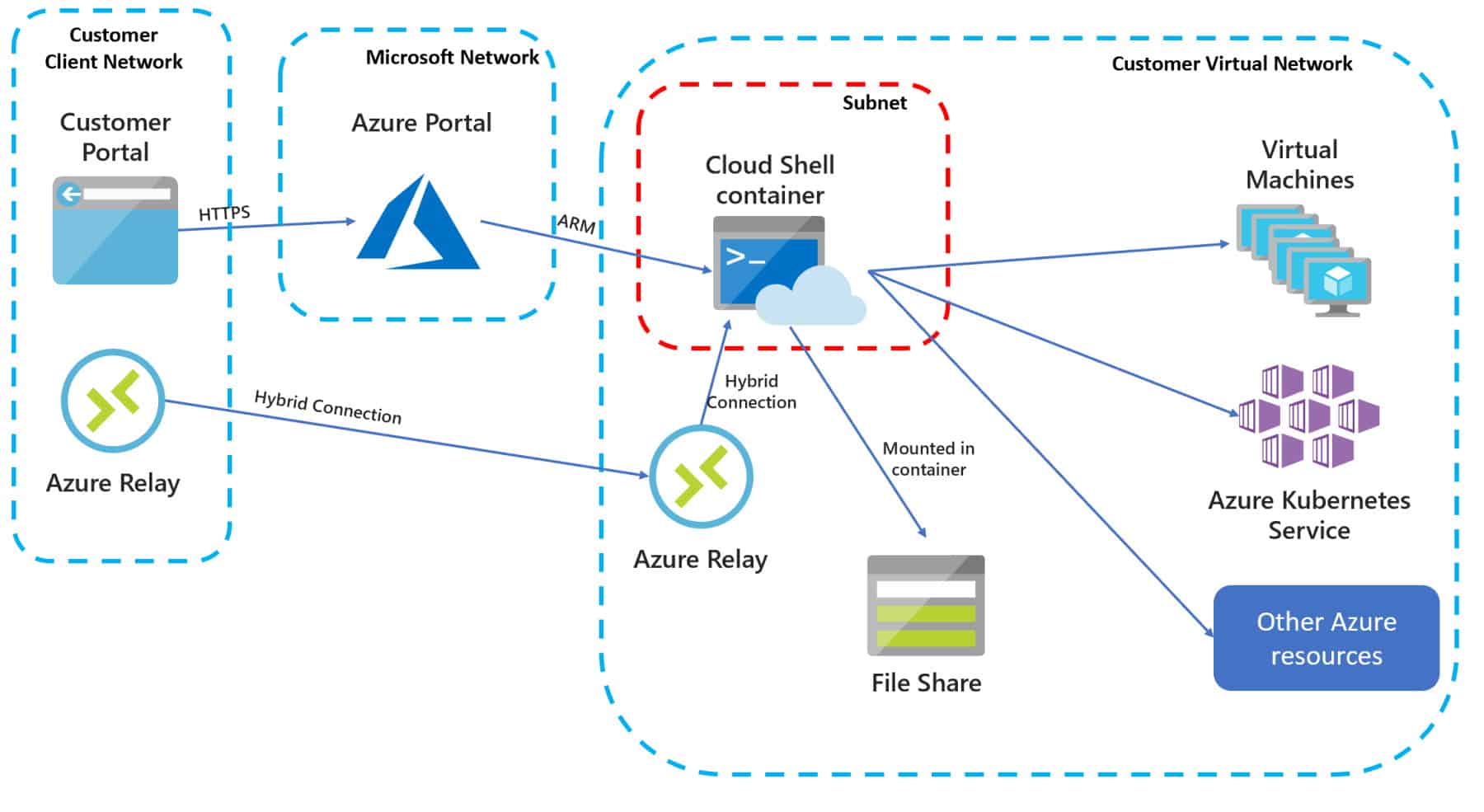
Connect Azure Cloud Shell to Virtual Network vNet
As you know, Azure Cloud Shell is a great management tool to manage your Azure resources. Azure...
Connect Ubiquiti UniFi Dream Machine to Azure VPN
A couple of days ago I got a Ubiquiti UniFi Dream Machine, which is an all-in-one device with an access point, 4-port switch, and a...
Cisco UCS Hyper-V Cluster – Configure Hyper-V Networks – Part 5
This How-To shows you how you configure the (Virtual) Network Adapters of the Hyper-V Servers. This is not really heavy, but to complete...