6 Command Line (PowerShell & CLI) Tips & Tricks for Microsoft Azure you should know about!
There are many experiences and possibilities to manage your Microsoft Azure resources, one of them...
PowerShell Unplugged 2022 Edition
April Edwards and I had the chance to host the PowerShell Unplugged 2022 Edition and the video is now available on YouTube! In the...
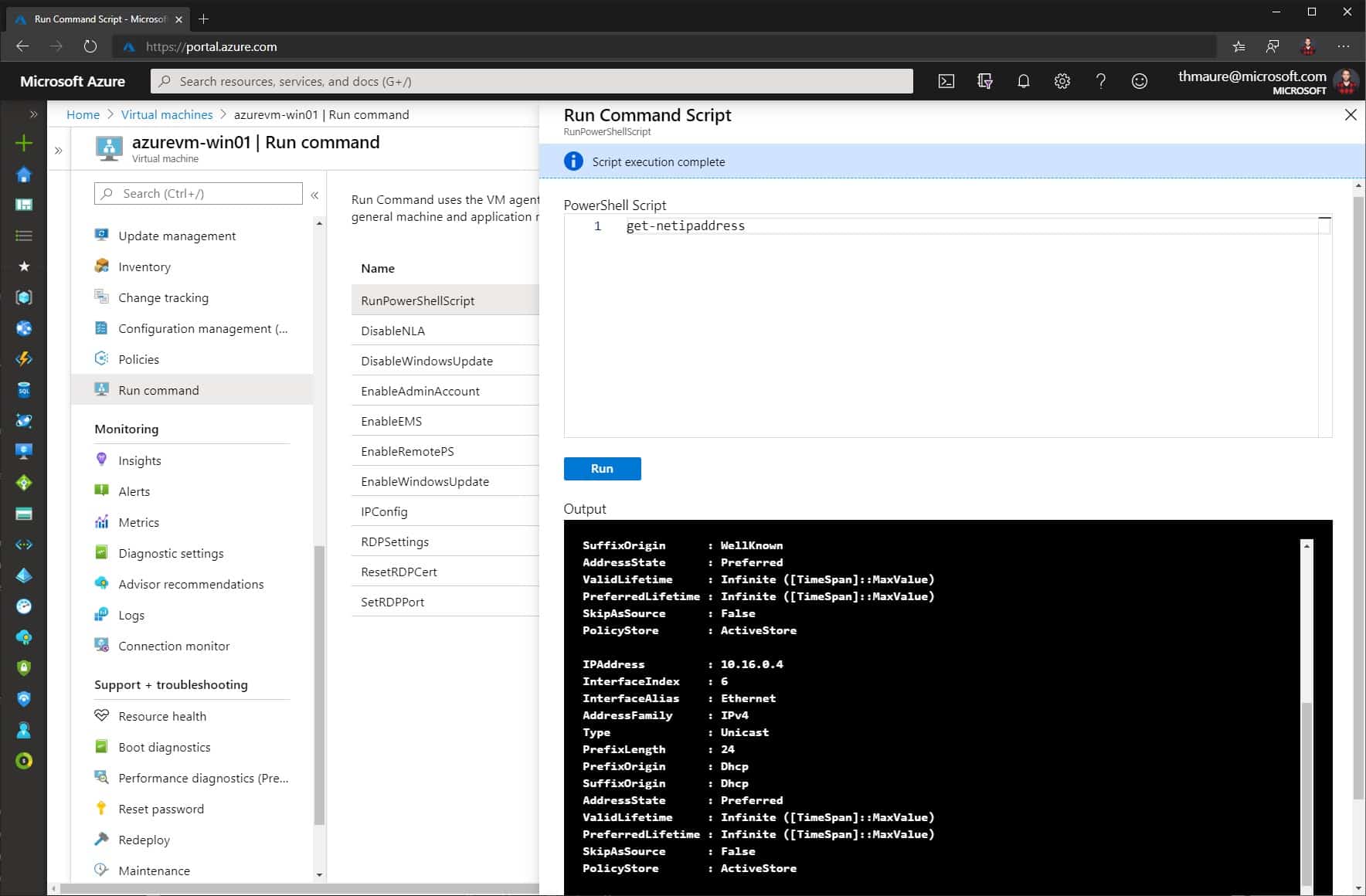
How to Run Scripts in your Azure VM using Run Command
You can access your Azure IaaS virtual machine (VM) in multiple ways like SSH or RDP, depending on your operating system and configuration....
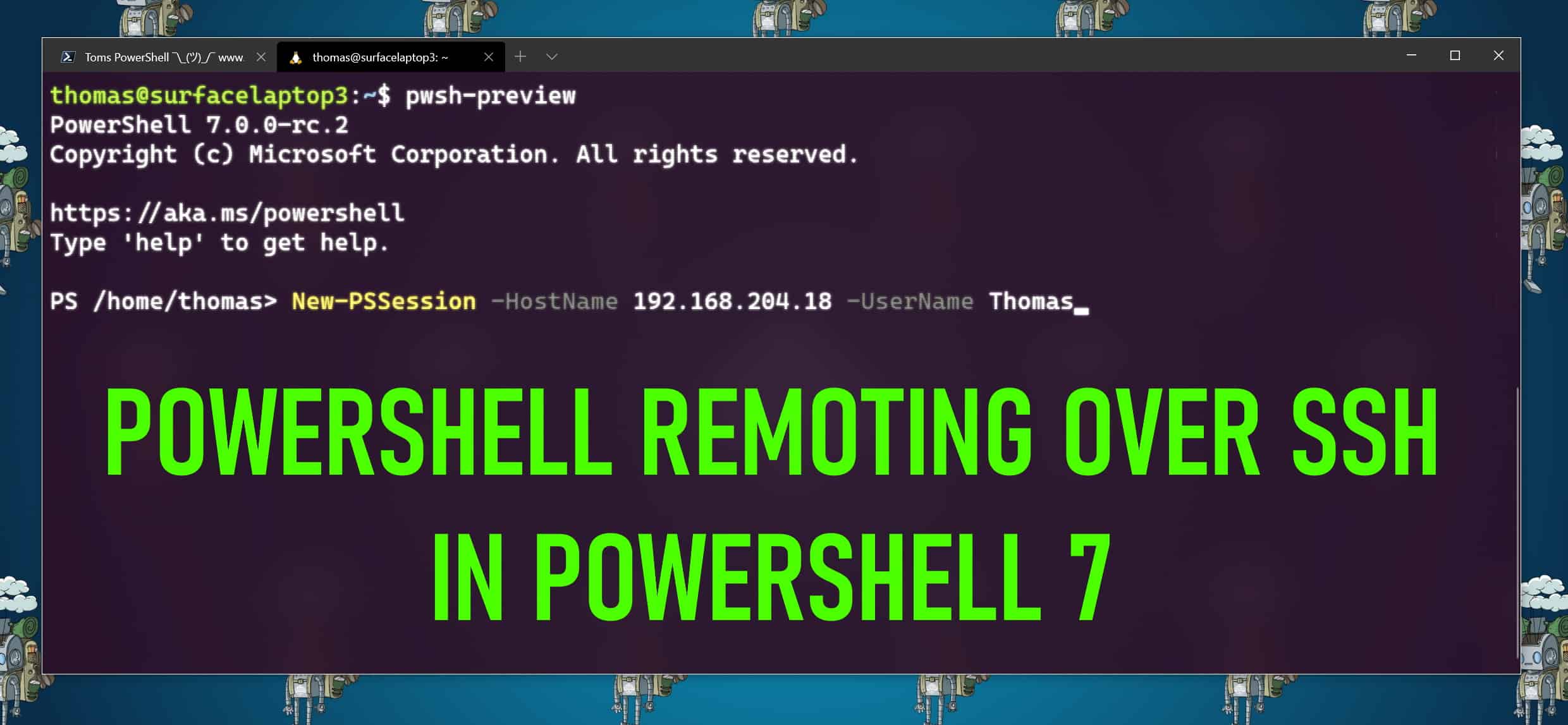
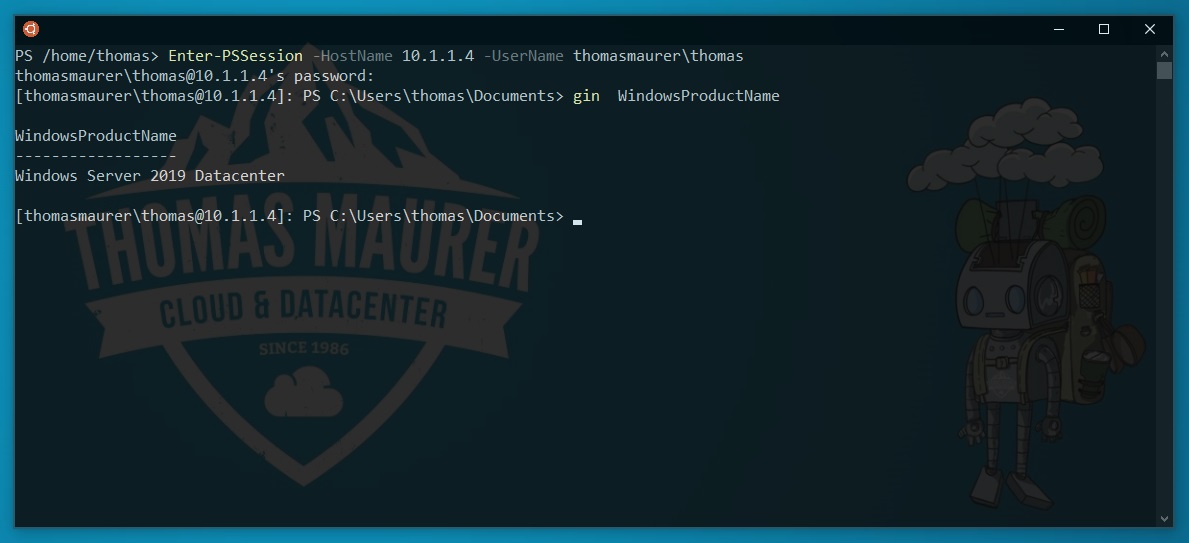
Enable PowerShell SSH Remoting in PowerShell 7
In this blog post, we will have a look at how you can enable and set up PowerShell SSH Remoting or PowerShell Remoting over SSh with...
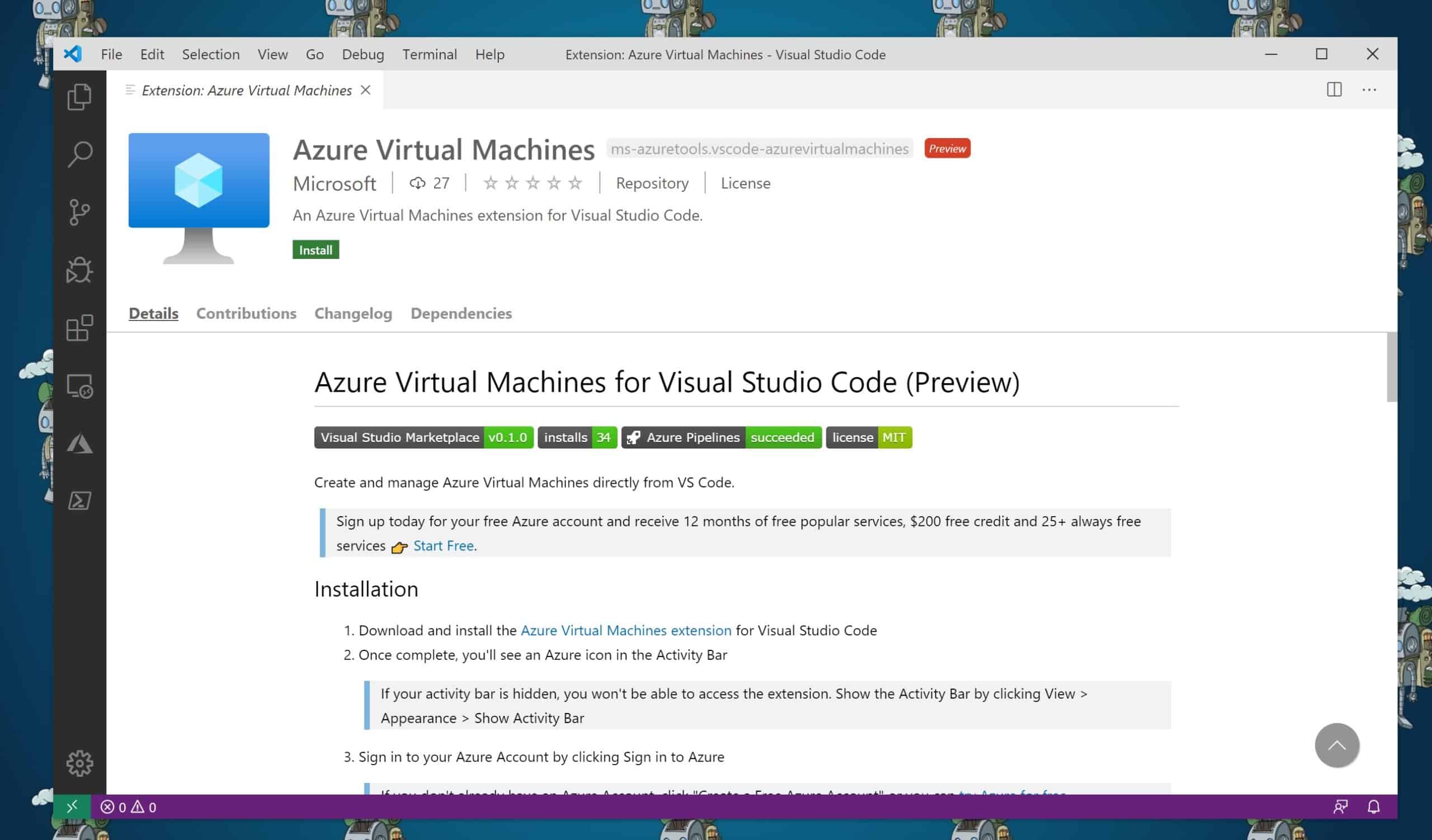
Create and Manage Azure VMs from VS Code
With the new Azure Virtual Machines (VMs) extension for Visual Studio Code (VS Code), you can now create and manage Azure VMs directly from...
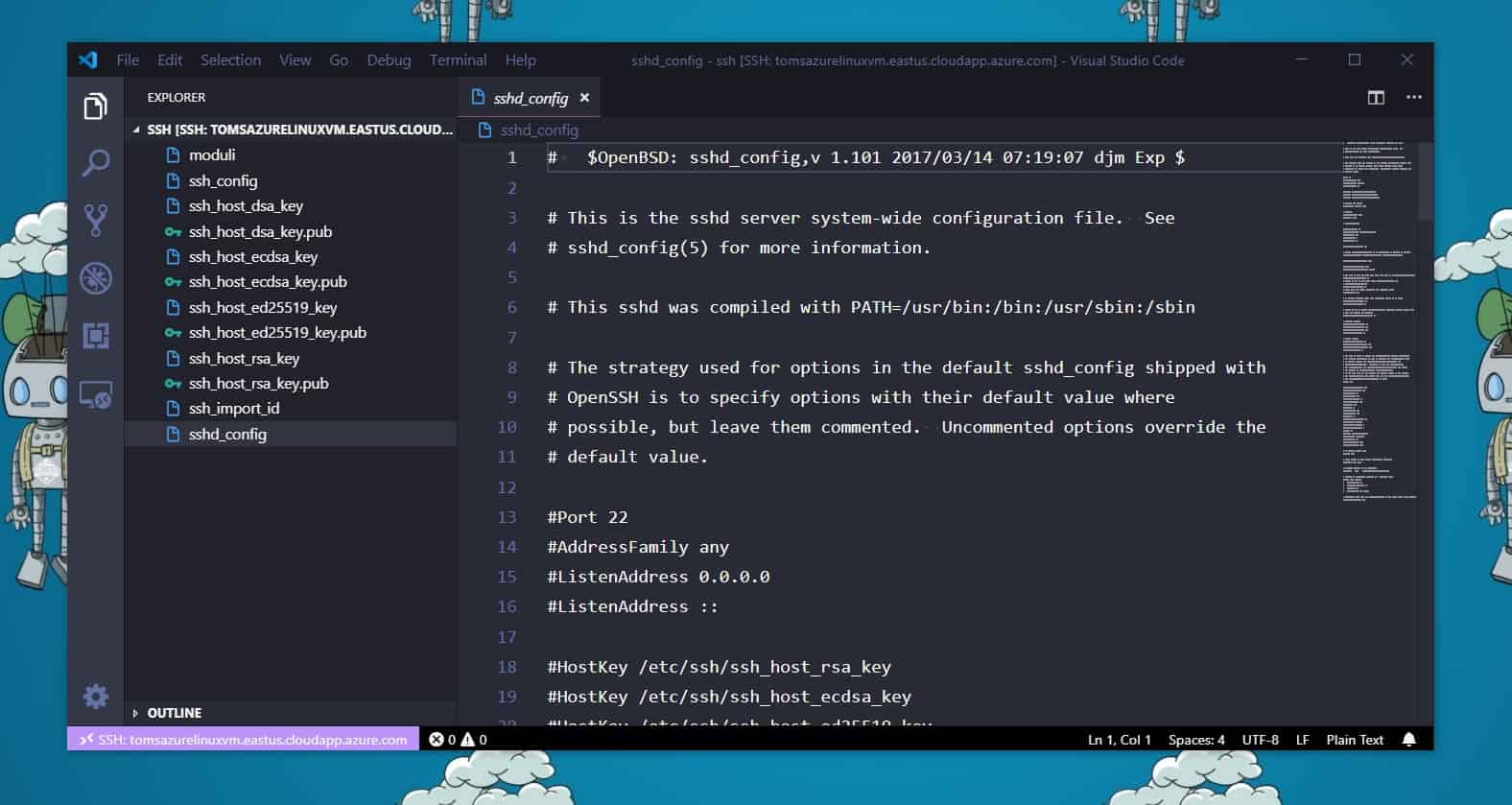
Remote Edit Files on Azure Linux VMs using VS Code
There are a lot of different ways to remote manage your Azure virtual machines using various tools...
Azure Bastion – Private RDP and SSH access to Azure VMs
Azure Bastion is a new service which enables you to have private and fully managed RDP and SSH access to your Azure virtual machines. If...
Setup PowerShell SSH Remoting in PowerShell 6
With PowerShell version 6, Microsoft introduced PowerShell Remoting over SSH, which allows true multiplatform PowerShell remoting between...
Mastering Azure with Cloud Shell
There are multiple ways to interact and manage resources in Microsoft Azure. You can use the Azure...