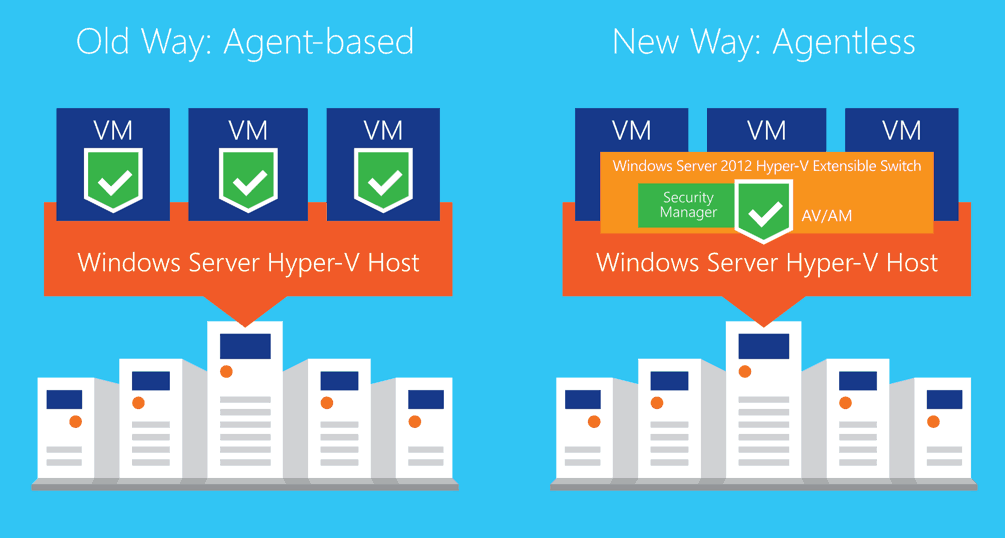
Secure your Hyper-V environment with 5nine Cloud Security 8.1
In the past years I was building several Hyper-V environments together with Enterprise customers...
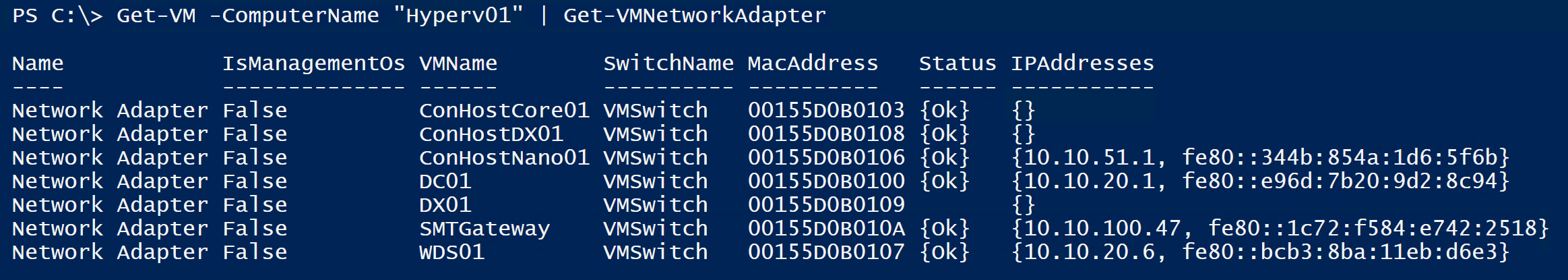
PowerShell One-liner to list IP Addresses of Hyper-V Virtual Machines
Here a very quick PowerShell command to list all the Virtual Network Adapters, including IP Addresses of Virtual Machines running on a...
Summary: Update Rollup 8 for System Center 2012 R2 and Azure Pack now available
Yesterday Microsoft released Update Rollup 8 for System Center 2012 R2 and Windows Azure Pack. Again with the Update Rollups for Windows...
Cisco UCS supports RoCE for Microsoft SMB Direct
As you may know we use SMB as the storage protocol for several Hyper-V deployments using Scale-Out...
Cisco UCS and Hyper-V Enable Stateless Offloads with NVGRE
As I already mentioned I did several Hyper-V and Microsoft Windows Server projects with Cisco UCS. With Cisco UCS you can now configure...
Overview on Windows Server and Hyper-V 2012 R2 NIC Teaming and SMB Multichannel
I know this is nothing new but since I had to mention the Whitepaper on NIC Teaming and the use of SMB Multichannel as well as the...
Green Cloud based on Windows Server Hyper-V and Windows Azure Pack
If you try to host some IaaS workloads or build a Hybrid Cloud environment connected to a service...
Veeam Hyper-V 2012 R2 Webinar recording available
Yesterday I had the chance to do a webinar on Windows Server 2012 R2 Hyper-V and Veeam Backup & Replication V7 R2 together with Moritz...
TechNet Switzerland Event: From VMware to Hyper-V
On Tuesday, December 03 I will present together with Markus Erlacher, former Microsoft Switzerland TSP and now Managing Director at itnetx...
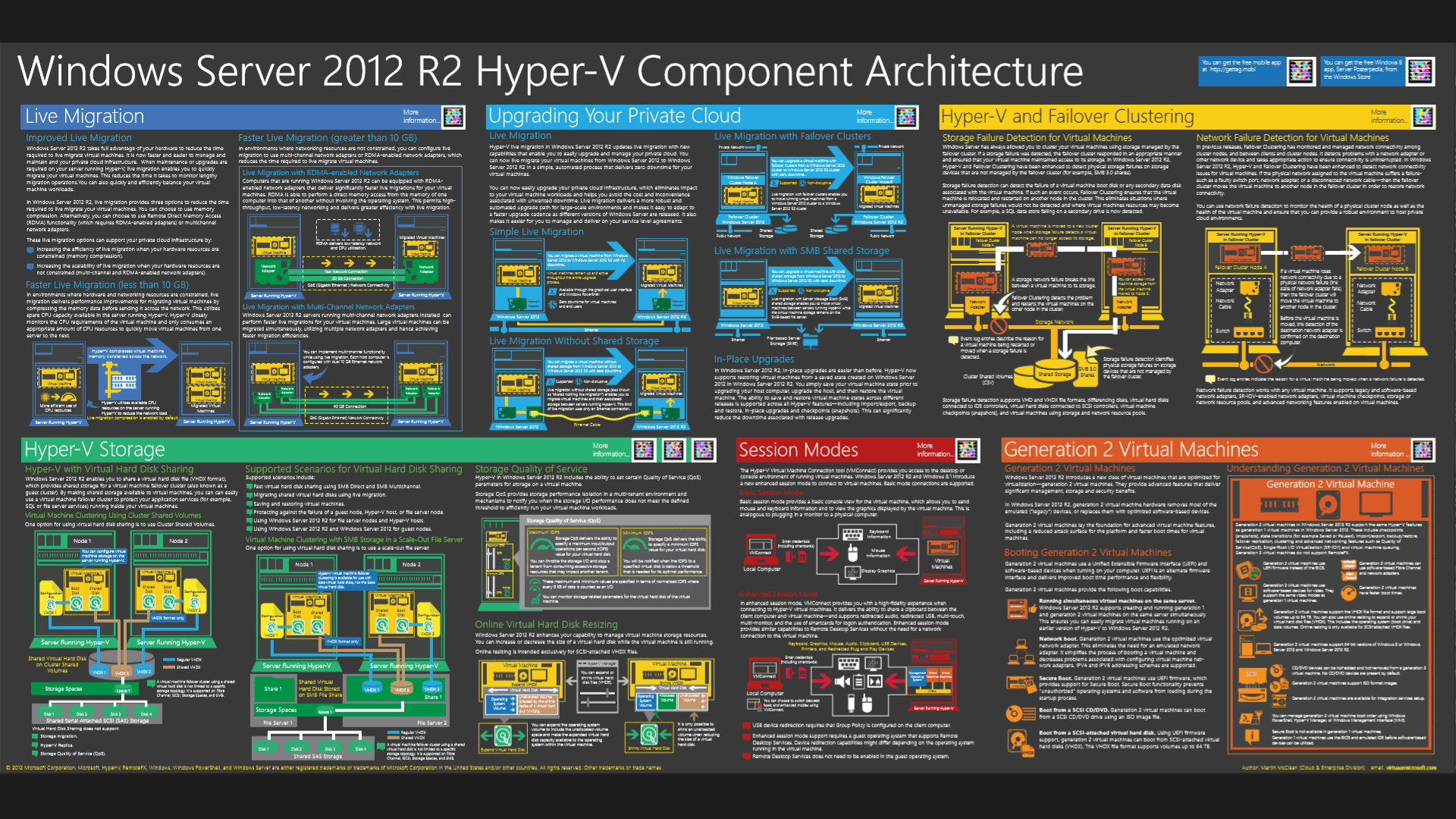
Windows Server 2012 R2 Hyper-V Component Architecture Poster and Hyper-V Mini-Posters
Microsoft today released the Windows Server 2012 R2 Hyper-V Component Architecture Poster and...